Recently, while performing some tasks for a customer, I was able to flex my information gathering skills quite a lot. The ensuing bit of investigation (which we’ll discuss more in-depth in the next post) led to me discovering that a customer’s main public-facing web server contained a remote file upload vulnerability and that an attacker could gain shell access to that server (behind their firewall) in a single easy step.
While it turned out this was very easy to investigate, identify the vulnerability and then exploit it, I realized that there aren’t a lot of tutorials out on the web to show in-depth or step-by-step what you can do with a remote file upload vulnerability.
In addition to the fact that in-depth tutorials are not plentiful, there seem to be very few instruction sets on where to find shells and what to do with them once you’ve determined you can gain access.
So, I set aside some time to put together a couple of tutorials over the next couple of weeks. The first scenario we’re going to deal with is an ASP.NET web application that has a remote file upload vulnerability. First, we’ll build a virtual machine to exploit and then, in the next couple of posts, we’ll exploit it and see what damage we can really do.
The reason I decided we were going to build a vulnerable virtual machine is because I have found numerous quick posts about how to exploit the vulnerability we’re going to showcase here and, unfortunately, they all have listed the Google Dorks (or web searches) you can use to find web servers that are vulnerable. While, I’m enough of a curious hacker to maybe play with one of these vulnerable servers while anonymized and connected to a Starbucks, I take some exception to this as “de facto” system of learning. If you’re going to want to learn how to exploit remote file uploads, standing up a virtual machine to play with accomplishes two things: a) you stay ethical (and that’s a good thing) and b) you can actually see what files are created, what logs are created, and what the residual damage is to the server, once you breach it. This, to me, helps reinforce the whole “hack to learn” mentality, then just finding someone else’s server to breach. Instead, you can take this example and learn from it so that maybe you see how a “defense-in-depth” approach helps fortify your server’s security.
Building the VM
The vulnerable web application we’re going to tinker with on this tutorial is dotnetnuke. It runs under ASP.NET, Microsoft SQL Server and Microsoft’s Web server, also known as IIS – Internet Information Services.
First, your best bet is to install Windows XP. The SP doesn’t matter because we’re not going to be penetrating this Virtual Machine at the OS level, we’re going to be attacking the web application stack.
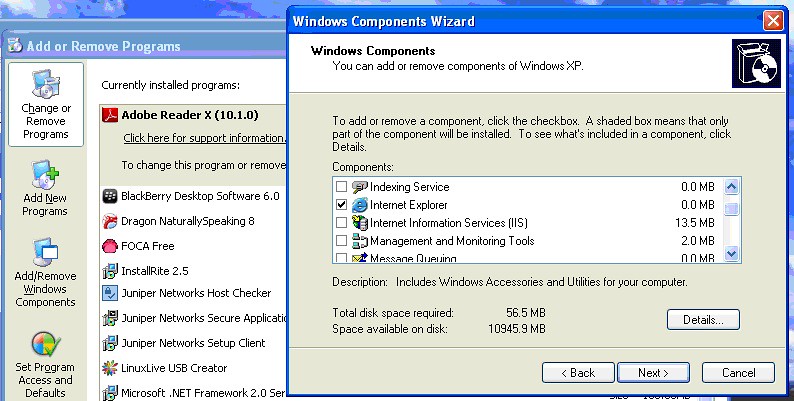
Once you have Windows installed, you’re going to need to install Internet Information Services (IIS). In Windows XP, you can install IIS by inserting the XP CD, bringing up the “Add / Remove Programs” interface and choosing the “Add/Remove Windows Components” button on the left-hand side of the screen.
This will invoke the “Windows Components Wizard”. In this wizard, you should check off the checkbox next to “Internet Information Services (IIS)” and click the “Next” button. This will walk you through installing IIS on Windows XP.
Once you’ve completed installing IIS, you should be able to open a web browser on the XP box and navigate to http://localhost and you should see web pages that look similar to these:
Congratulations! You’ve now got a web server answering on your Windows XP machine.
Now, the next thing we’ve got to do is make sure the Windows XP Firewall is configured to pass data through the firewall to the IIS server.
Windows XP Firewall
If you’re running a version of Windows XP that has the Windows Firewall as part of its application suite, then you’ll need to change its configuration (post IIS install) to allow Web Server traffic through the firewall. The easiest way to do this is by opening the “Windows Firewall” dialog from Windows XP’s “Control Panel”.
Clicking on the “Advanced” tab brings you to the “Network Connection Settings” setion.
Check the checkbox next to the network connection that is applicable (default is “Local Area Connection” in Virtual Machines, but this can vary from machine to machine) and click the “Settings” button.
By checking the checkbox next to “Web Server (HTTP)”, you’ll allow an exception through the firewall for all HTTP traffic. And for our purposes, HTTP (port 80) traffic is sufficient. Click “OK” and exit out of the “Windows Firewall” configuration screens.
Next, we’ll need to install ASP.NET on our Windows XP box.
Installing ASP.NET on Windows XP
There are a multitude of ways of installing ASP.NET on your Windows XP machine. The most modern technique is navigating a web browser to www.asp.net and installing the Microsoft Web Platform Installer. This will eventually get you ASP.NET installed, as well as some Visual Studio components. (NOTE: the web site states it only supports Windows XP SP3+, so if you’re running a lower version, this is not the way to go.)
If you want, please go ahead and follow the instructions on that web site to install the latest version of ASP.NET (at the time of this writing, the most current version available on their sites is 4.5).
However, since the end goal of this exercise is to build a vulnerable virtual machine, it is perfectly acceptable for us to do something a tad bit easier and maybe a little less secure than we would ordinarily like: you could install a version of ASP.NET that’s already on your Windows XP machine.
By opening a command prompt and navigating to the Microsoft .NET Windows directory, “C:\Windows\Microsoft.NET\Framework\v2.0.50727”, you will find two (2) executables that you can run from the command line, in order to install ASP.NET:
aspnet_regiis –i and aspnet_regiis –c
This will register and install an older version of ASP.NET on your machine. For this exercise, though, that is fine. We are not building a machine for the purpose of hosting a real web application (where we may want the latest and greatest software). We are trying to build a vulnerable machine and there’s no need for engineering this machine for greatness.
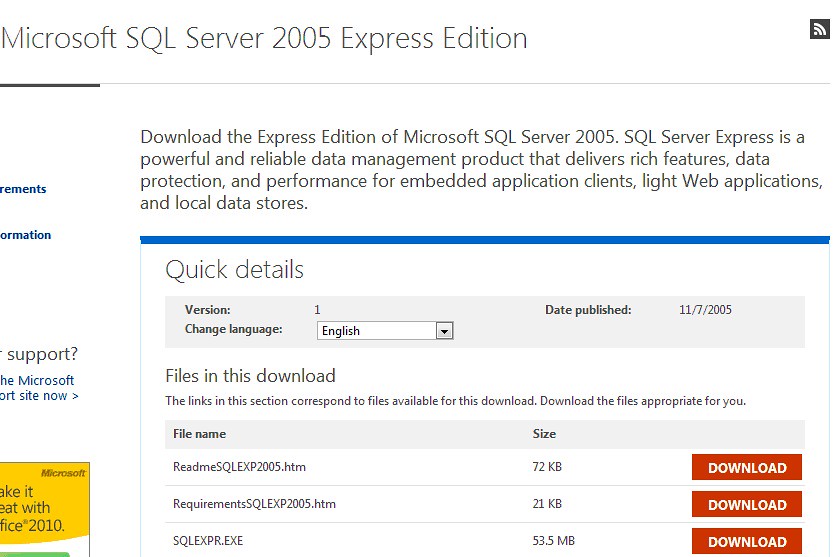
Installing SQL Express
Download SQL Server 2005 Express from http://www.microsoft.com/en-us/download/details.aspx?id=21844
You’ll want to get the SQLEXPR.EXE file and run that.
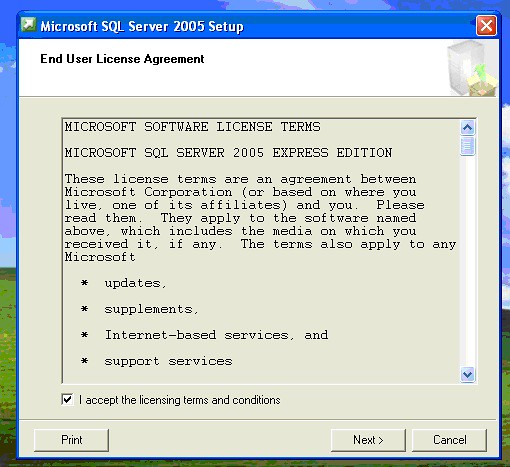
Accept the license agreement and walk through the install.
Once SQL Server Express is installed, you won’t have to do further configuration of it, in order to install dotnetnuke. Dotnetnuke will auto-create any databases it needs.
Installing dotnetnuke
Once you’ve taken care of the pre-requisites (as outlined above), you’ll be ready to install dotnetnuke. But take care! You DON’T want to install the latest version of dotnetnuke. You want to install an older version of it and the archives are a little hard to find.
So, navigate to http://dotnetnuke.codeplex.com/releases/view/20945 and download the “DotNetNuke_04.05.01_Install.zip” file located at http://dotnetnuke.codeplex.com/releases/view/20945#DownloadId=52880
This zip file contains all the files that make up DotNetNuke version 4.05.01, which is a version vulnerable to the remote file upload we’ll be exploring in later posts.
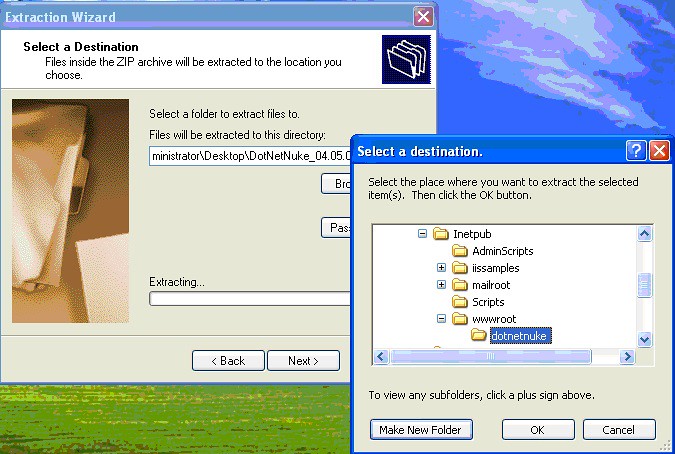
So, to begin, extract the contents of this zip file to a folder under the “wwwroot” folder located right below the “InetPub” folder on your machine.
Once you’ve extracted it, you will need to set up a few permissions first. In the Windows XP world, you need to locate the “C:\inetpub\wwwroot\dotnetnuke” folder (or if you renamed it, whatever you renamed it) and right-click on the folder and go to “Security”.
You need to add the ASPNET user account to the permissions list and give it “Modify” permissions (or you can give it the “Full Control” permissions – hell, it’s a vulnerable machine).
You should also take the time to go into the “Advanced” button, select the ASP.NET Machine Account, check the box next to “Replace permission entries on all child objects” and click the “OK” button.
Next you’ll want to tell IIS (the web server) that you want to serve web pages from the dotnetnuke folder.
Configuring IIS to serve DotNetNuke
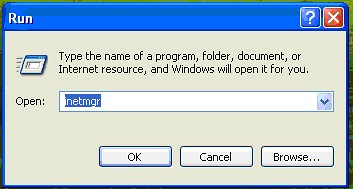
Run the IIS Manager console, by click on “Start”, then clicking on “Run” and typing in “inetmgr” and hitting enter.
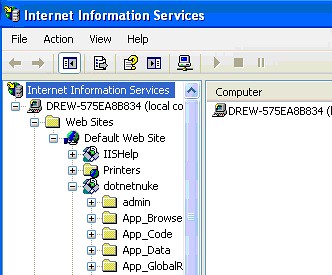
Open the plus sign next to Web Sites and “Default Web Site”.
Right-click on “Default Web Site” and select “New” and then “Virtual Directory”. Make sure to set up the Virtual Directory the same as the illustration below:
And be sure that you give the “Application Name” a name in the “Application Settings” section (we set ours to dotnetnuke above). You should then see a Virtual Directory called “dotnetnuke” under your IIS Manager.
Click “OK” and once completed, you should be able to open a web browser to http://localhost/dotnetnuke
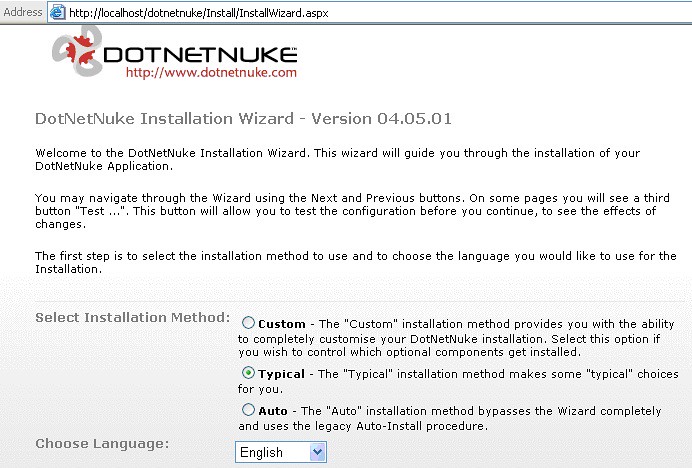
At this point, dotnetnuke will walk you through the installation wizard.
Configuring DotNetNuke
First, you’ll be presented with this screen. Select “Typical” and click “Next (in the bottom right-hand corner).
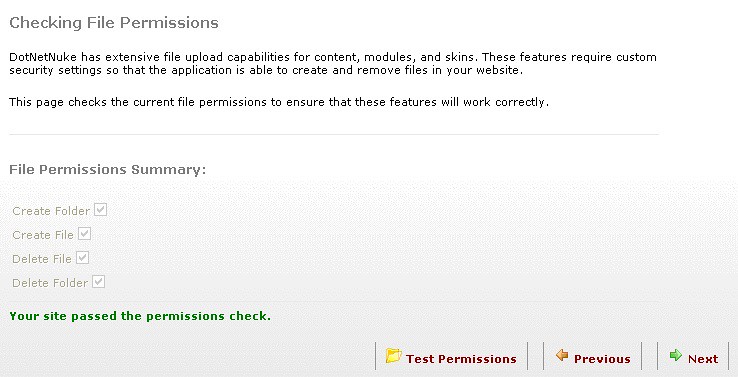
Then, the next screen will test that your permissions have been set up correctly. We did this a few steps back.
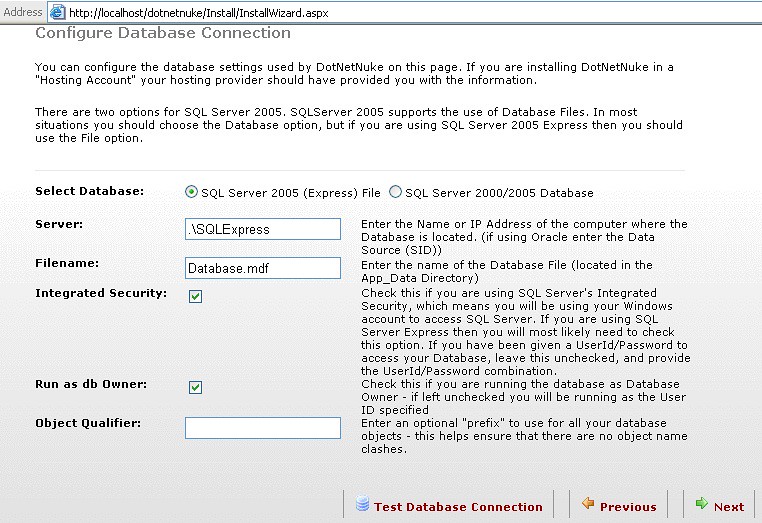
Click the “Test Permissions” link and when you get the green, click the “Next” link. At the next screen, you’ll set up your database. You won’t need to change anything from the screen below, if you installed SQL Server 2005 Express. If you didn’t, you can find other instructions here (http://www.dotnetnuke.com/Resources/Wiki/Page/Install_DotNetNuke.aspx) :
If you followed our SQL Express instructions above, then just take the defaults and click “Test Database Connection”. Once completed, click the “Next” button.
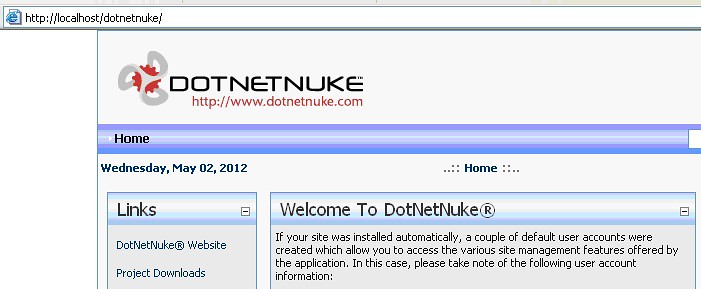
Once you see the following output, you’re all set. Select the link at the bottom right that brings you into the Application (dotnetnuke).
Congratulations! You’ve now installed dotnetnuke!
The last thing we need to do before exploitation is making sure the application answers external http requests. We’ll do that now.
Configuring DotNetNuke for External HTTP Requests
So, a little explanation before we move forward. DotNetNuke is now installed and if you were to browse from the XP machine, using http://localhost/dotnetnuke, you’ll be presented with the application. This is great. But one of the things we want to do is use our non-virtual host to launch attacks against the web application. We want to do this to give us a “real world” example of how to exploit remote file uploads. So, the last thing we need to do is make sure that when we open a web browser on our main (non-virtual) host, we can put in a URL with the IP address of our virtual machine and the web server responds.
Currently, this is not the case. So, we’ll need to set this up.
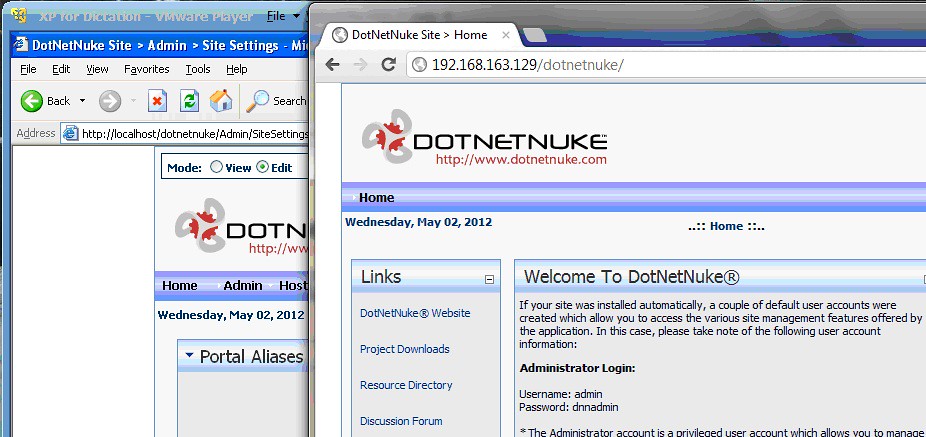
Do accomplish this, open a web browser on the XP machine and navigate to http://localhost/dotnetnuke. You’ll see the application.
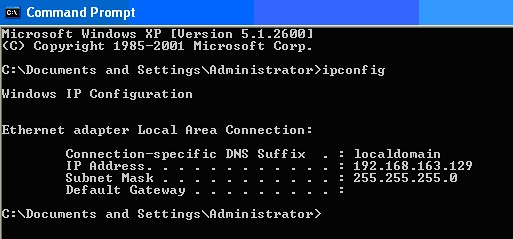
Next, open a command window (DOS box) and type in “ipconfig” and hit enter.
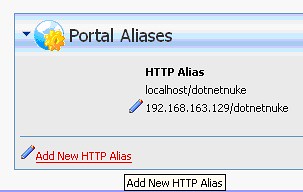
My NAT’d IP address is 192.168.163.129. When I’m on my host machine, I’ll be trying to access dotnetnuke by using http://192.168.163.129/dotnetnuke. However, we need to first tell DotNetNuke to answer to this IP address.
So, in the Web Browser, login using the username and password you were asked to set during setup. For instance, I log in as ‘host’ with my password.
Once logged into dotnetnuke, you need to navigate to the Portals page. Click the “Admin” menu, then select “Site Settings” from the “Admin” menu:
In the “Portal Alias” section of the page, click the “Add New HTTP Alias” link to create an alias for the Portal.
Here, you’ll want to put the IP address of your virtual machine and “/dotnetnuke” after, like so:
Click “Add New Alias” and you will have now enabled DotNetNuke to answer an external HTTP request, using the external non-virtual host.
To prove this out, get on your non-virtual host, open a web browser and point it to the Portal Alias you just created.
That’s it!
Congratulations!
You’ve now got a virtual Windows XP host, serving dotnetnuke externally to your non-virtual host machine.
Conclusion
Next Tutorial, we’ll start to exploit this bad boy a bit.
Stay tuned!













This comment has been removed by a blog administrator.
ReplyDelete★ COMPOSITE HACKS★
DeleteAn assumption that I'd have to know how to code to be able to hack was made years back, Though Coding and Programming Is Involved But, Hacking isn't limited to codes, Throughout my daily life, I tend to experience the most complex, uncommon, yet positive solutions to common problems. It's rooted in how I think. I couldn't turn it off if I tried. It's a part of my character that I was born with, not something I learned at school or from books. I sometimes wish that weren't the case. That it was something I could teach. That it was something I could give lessons in, without having to start from scratch in an entire way of thinking that few people would have patience for.
Hacking is not related to specific programming language. Hacking is the idea and mindset And Ability for you to Use various Hack Tools to Break into the Vunurebilities of the Target. For example you can create a key logger program either with C# or python and make it as background process to collect user input. You can Also Hack Into a Target's Electronic Devices Easily With Various Special Hack Tools.
Hacking Has Been My Job For over 20 years now of which i Have been making So Much Money From. Some Years Back I Created A Hack Team called COMPOSITE HACKS.
COMPOSITE HACKS is a Team Of Professional HACKERS , a product of the coming together of Legit Hackers from the Dark-Web (pentaguard, CyberBerkut, White Hack and Black Hat,) whose system is a very strong and decentralized command structure that operates on ideas and directives.
.
★ OUR HACKING CAPABILITIES:
We Offer Varieties Of LEGIT Hacking Services With the Help Of Our Root HackTools, Special HackTools and Our Technical Hacking Strategies.
- Below is a List Of Services we Render Often:
★Penetration Testing
★ Phishing
★ Jail Breaking.
★ Phone Hack: Giving you access to the Target's Call Log, messages, chats and all social media Apps .
★Retrieval Of Lost Files
★ Location Tracking.
★ Clearing Of Criminal Records.
★ Hacking Of Server, Database And website e.g Facebook, twitter, Instagram Snapchat etc
★ SOME OTHER SPECIAL SERVICES WE OFFER:
★ Bank Accounts Loading ( Only USA Banks)
★ Credit Cards Loading (Only USA CC's)
★ One Vanilla Cards Loading ($100 cards and above)
★ Sales Of HACKED/PROGRAMMED ATM Cards & CC's ( For All Countries.)
★ You can also contact us for other Cyber Attacks And Hijackings, we do almost All.
★Contact Us for Your Desired Service Via: compositehacks@gmail.com
★We Treat Every Request With Utmost Confidentiality★
I am here to testify about how total company change my life,it was like this,i read about online trade and investment,when searching on how to trade with legit company,i ment a review which said i can invest in oil and gas company,where i can invest $5000 USD into oil and gast ,which i did after reaching total company,out end of my trade,i make a profit worth $65,0000 USD after investing with now through out thirty one days ,it real great i ment this company which change my life,i said to myself,it is better to share this on topix and forum,so that financial problem can reduce,what have your government offer to reduce financial problem,it is better you help yourself,because the system of the countries are not after our dealy bread,you can invest and get rich too,email total company at: total.company@aol.com
DeleteNeed The To Hire A Hacker❓ Then contact PYTHONAX✅
DeleteThe really amazing deal about contacting PYTHONAX is that the Hack done by us can’t get traced to you, as every Hacking job we do is strongly protected by our Firewall. It’s like saying if anyone tries to trace the Hack, it will lead them to us and we block whatever actions they are doing.
We have been Invisible to Authorities for almost a decade now and if you google PYTHONAX, not really about us comes out, you can only see comments made by us or about us.
Another Amazing thing to you benefit from Hiring our Hackers is that you get a Legit and the best Hacking service, As we provide you with Professional Hackers who have their Hacking Areas of specialization.
We perform every Hack there is, using special Hacking tools we get from the dark web.
Some list of Hacking Services we provide are-:
▪️Phone Hacking & Cloning ✅
▪️Computer Hacking ✅
▪️Emails & Social Media Account Hacking✅
▪️Recovering Deleted Files✅
▪️Tracking & Finding People ✅
▪️Hunting Down Scammers✅
▪️Hack detecting ✅
▪️Stealing/Copying Files & Documents From Restricted Networks and Servers ✅
▪️Bitcoin Multiplication✅
▪️Binary Option Money Recovery ✅
▪️Forex Trading Money Recovery✅
▪️IQ Option Money Recovery✅
And lots more......
Whatever Hacking service you require, just give us an Email to the Emails Address provided below.
pythonaxhacks@gmail.com
pythonaxservices@gmail.com
2020 © PYTHONAX.
Hey Guys !
DeleteUSA Fresh & Verified SSN Leads AVAILABLE with best connectivity
All Leads have genuine & valid information
**HEADERS IN LEADS**
First Name | Last Name | SSN | Dob | DL Number |Address | State | City | Zip | Phone Number | Account Number | Bank Name
*Price for SSN lead $2
*You can ask for sample before any deal
*If anyone buy in bulk, we can negotiate
*Sampling is just for serious buyers
==>ACTIVE & FRESH CC FULLZ ALSO AVAILABLE<==
->$5 PER EACH
->Hope for the long term deal
->Interested buyers will be welcome
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Hello Everyone !
DeleteUSA SSN Leads/Fullz available, along with Driving License/ID Number with good connectivity.
All SSN's are Tested & Verified.
**DETAILS IN LEADS/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL
->EMPLOYEE DETAILS
*Price for SSN lead $2
*You can ask for sample before any deal
*If you buy in bulk, will give you discount
*Sampling is just for serious buyers
->Hope for the long term business
->You can buy for your specific states too
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
**SELLING SSN+DOB FULLZ**
DeleteCONTACT 24/7
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
>>1$ each without DL/ID number
>>2$ each with DL
>>5$ each for premium (also included relative info)
Price will be reduce in Bulk order
FORMAT OF LEADS/FULLZ/PROS
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->COMPLETE ADDRESS
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYMENT DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>All Leads are Spammed & Verified.
>Fresh spammed data of USA Credit Bureau
>Good credit Scores, 700 minimum scores
>Invalid info found, will be replaced.
>Payment mode BTC, ETH, LTC, PayPal, USDT & PERFECT MONEY
''OTHER GADGETS PROVIDING''
>SSN+DOB Fullz
>CC with CVV
>Photo ID's
>Dead Fullz
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>HQ Emails with passwords
Contact 24/7
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Verified & Updated FULLZ|PROS|INFO|LEADS
DeleteUSA UK CANADA All States Available
Fresh Database & Never used before
Available in bulk quantity
SSN DOB DL ADDRESS EMPLOYEE & BANK INFO USA
SIN DOB ADDRESS MMN CANADA
NIN DOB DL ADDRESS SORTCODE UK
High Credit Scores Fullz
Young Age Fullz
Business EIN Company Fullz
CC with CVV
Dumps with Pin Track 101 & 202
Real|Original ID|DL Front Back & Selfie with SSN
Passport Photos with Selfie
Fullz with expiry dates
UberEats|Doordash Fullz with KYC Stuff
Bulk Quantity available
Old Age Fullz
Premium Leads|Info|Pros
You can asked for specific info like Cities|States|Zip|Gender|Age
Hacking Spamming Carding Tools & Tutorials available as well
For Order & Details feel free to ping us
(at)leadsupplier , (at)killhacks Tel. gram
(at)killhacks , 752822040 I C Q
hacksp007 (at) DNMX . org E mail
(at)peeterhacks Skype
SSN DOB DL ADDRESS MMN FULLZ USA
DeleteSIN DOB DL ADDRESS MMN CANADA
NIN DOB DL ADDRESS SORT CODE UK
FULLZ AVAILABLE UK USA CA DL SCAN PROS MVR TELEGRAM:KILLHACKS
Fresh Fullz available in bulk quantity
Recent spammed & verified fullz
Guaranteed stuff with full replacement offer
= Telegram > @ leadsupplier | @ killhacks
= Whats App > +1.. 727.. 788... 6129..
= Skype > @ peeterhacks
= E mail > cyber.zoneunivese at g>mail . com
DL Scan front back with selfie & SSN
DL Fullz with MVR
DL Fullz with issue & Expiry dates
SSN DOB DL ADDRESS Bank & Employee info Fullz
DL fullz EIN & Front back scan
UK NIN dob dl address sort code info fullz
UK DL Scan Front Back with Selfie
UK CC's with CVV's & billing address
Canada SIN DOB DL ADDRESS MMN info Fullz
Canada DL Scan Front back with selfie
Canadian CC's with CVV's address
USA UK CANADA Young & Old Age Fullz
High credit scores Pros USA UK CA (700+ Scores)
Business EIN USA Company Pros Fullz
Passport Photos with selfie
Fullz for Loan & Credit applying & KYC Stuff
Tools for Hacking|Spammming|Carding|Scripting
SMTP|RDP
C-panels
Shells
Web-mailers
Bulk SMS Sender
Email Blaster
Carding & Cash out Methods with video tutorials
Scam pages & Scam Page Scripting
Spamming Complete Package with all Tools & Tutorials with 100k Email Leads
Fresh tools available
No sampling for CC's & Tools
Tutorials will be provided if you want
Contact us for more stuff & Fullz info
Hello Everyone
DeleteHere we come with updated & Fresh spammed FULLZ
Fullz of USA UK Canada in Bulk quantity
New Year sale offers|Christmass offer for Bulk buyers
SSN DOB DL
SIN DOB ADDRESS MMN
NIN DOB DL ADDRESS Sort Code
Contact us here anytime
What's App = +1... 727.... 788.. 6129...
Tele Gram = @ killhacks & @ leadsupplier
Skype = @ peeterhacks
E mail = dghcks2 t g mail dot com
USA SSN DOB DL ADDRESS Fullz
Real DL Photos Front Back with SSN
Business EIN Company Pros Fullz
Young & Old Age fullz (2000+ & 1960 below)
DL fullz with issue & expiry Dates
Fullz with MMN CC CVV
Dead Fullz|Live Fullz|Sweepstakes
You guy's can get specific info fullz as well
Age|Gender|City|State|Zip specific
UberEats & Doordash KYC info Pros Fullz
UK NIN DOB DL ADDRESS
NIN DOB ADDRESS Sort Code
UK Real DL Front Back with Selfie
Canada SIN DOB ADDRESS MMN Phone Email
All States available
Canada DL Front Back with Selfie
All stuff will br fresh & Valid guaranteed
No sampling for low quantity
Available everytime
Ping Us for fresh info Fast
ID's|DL Photos limited fresh stock available
#USAFULLZ #UKFULLZ #CANADAFULLZ #SSNFULLZ #NINFULLZ #SINFULLZ
#DLPHOTOSSCAN #USAUKCANADAINFO #DLDOCS #CCCVVSELL #DUMPSCVV
#PROSFULLZUSA #SSNDOBDL #SINDOBMMN #NINDOBSORTCODE
What's App = +1... 727.... 788.. 6129...
Tele Gram = @ killhacks & @ leadsupplier
Skype = @ peeterhacks
E mail = dghacks2 at g mail dot com
This comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteI came onto your blog while focusing just slightly submits. Thanks a lot for sharing. Keep blogging.
ReplyDeleteI really liked this part of the article, with a nice and interesting topics have helped a lot of people who do not challenge things people should know... you need more publicize this so many people who know about it are rare for people to know this, Success for you.
ReplyDeleteThis is Great Wonderful Screenshot Awesome Thanks for sharing..
ReplyDeleteThanks for Sharing That... Sucses for You
ReplyDeletecaranddriver
INSTEAD OF GETTING A LOAN, CHECK OUT THE BLANK ATM CARD IN LESS THAN 24hours {blankatmhaker@gmail.com}
ReplyDeleteAm Mark Oscar,I want to testify about Jack Robert blank ATM cards which can withdraw money from any ATM machines around the world. I was very poor before and have no hope then I saw so many testimony about how Jack Robert send them the ATM blank card and use it to collect money in any ATM machine and become rich. I also email him and he sent me the blank card. I have use it to get 70,000 dollars. withdraw the maximum of $5,000 daily. Jack Robert is giving out the card just to help the poor. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email Him on how to get it now via: blankatmhaker@gmail.com or call/Text on +1(406) 350-4986
✅BINARY SCAM RECOVERY
Delete❌ Binary Option, Forex and their likes are a means of making money but it’s more like gambling. There are no sure means to guarantee that a person could make profit with them and that’s why it can also be reasoned to be scam. Let’s not forget that some individuals even give you 💯 % guarantee of making profits and end up running away with your money. The internet today is full of Binary Option Recovery Scam, you see so much testimonies been shared about how a firm or Company helped them recover what they lost to Binary Options. But believe it, it’s just a way to lure more people and end up scamming them.
❌ You might have also come across some individuals that say they will give you guarantee on successful trades but they only end up as SCAMMERS as well. You here them say stuffs like 200% guaranteed in just 2 weeks and when you go into trade with them, they start telling you to pay profits percentage before you can get your income. These are all liars please avoid them. But if you have been a victim of this guys, then you should contact PYTHONAX now‼️
✳️The big Question is “Can someone Recover their money lost to Binary Option and Scam⁉️
I will say yes, and will tell you how.
The only way to Recovery your money back is by hiring HACKERS to help you break into the Firms Database Security System using the information you provide them with, Extract your file and get back your money. It seems like a really impossible thing to do, I will tell you, it should be impossible, but with the use of specially designed softwares known to HACKERS and Authorities (such as The FBI, CIA e.t.c) it is possible and the only way to recover your money.
✅ PYTHONAX are a group of hackers who use their hacking skill to hunt down SCAMMERS and help individuals recovery their money from Internet SCAMMERS.
We just need the contact details of the SCAMMERS and Paymnet Info and within 4-8 hours your money will be return to you.
✳️ You can contact us via the emails below-:
PYTHONAXSERVICES@GMAIL.COM
We also provide Legit Hacking Services such as-:
🔸Phone Hacking/Cloning
🔸Email Hacking & Password Recovery
🔸Social Media Hacking & Passowrd Recovery
🔸Deleted Files Recovery 🔸Mobil Tracking
🔸Virus detection & Elimination.
Email-: PYTHONAXHACKS@GMAIL.COM
Pythonax.
2020 © All Right Reserved.
★COMPOSITE HACKS★
ReplyDelete🔍🔍Are you Seeking for the Best Legit Professional Hackers online??❓💻💻💻
Congratulations Your search ends right here with us. 🔍🔍🔍🔍
🏅COMPOSITE HACKS is a vibrant squad of dedicated online hackers maintaining the highest standards and unparalleled professionalism in every aspect.
We Are One Of The Leading Hack Teams in The United States🇺🇸🇺🇸 With So many Accolades From The IT Companies🏆🏅🥇. In this online world there is no Electronic Device we cannot hack. Having years of experience in serving Clients with Professional Hacking services, we have mastered them all. You might get scammed for wrong hacking services or by fake hackers on the Internet. Don't get fooled by scamers that are advertising false professional hacking services via False Testimonies, and sort of Fake Write Ups.❌❌❌❌
* COMPOSITE HACKS is the Answers to your prayers. We Can help you to recover the password of your email, Facebook or any other accounts, Facebook Hack, Phone Hack (Which enables you to monitor your kids/wife/husband/boyfriend/girlfriend, by gaining access to everything they are doing on their phone without their notice), You Wanna Hack A Website or Database? You wanna Clear your Criminal Records?? Our Team accepts all types of hacking orders and delivers assured results to alleviate your agonies and anxieties. Our main areas of expertise include but is never confined to:
✅Website hacking 💻,✅Facebook and social media hacking📲, ✅Database hacking, Email hacking⌨️, ✅Phone and Gadget Hacking📲💻,✅Clearing Of Criminal Records❌ ✅Location Tracking✅ Credit Card Loading✅ and many More✅
🏅We have a trained team of seasoned professionals under various skillsets when it comes to online hacking services. Our company in fact houses a separate group of specialists who are productively focussed and established authorities in different platforms. They hail from a proven track record and have cracked even the toughest of barriers to intrude and capture or recapture all relevant data needed by our Clients. 📲💻
🏅 COMPOSITE HACKS understands your requirements to hire a professional hacker and can perceive what actually threatens you and risk your business⚔️, relationships or even life👌🏽. We are 100% trusted professional hacking Organization and keep your deal entirely confidential💯. We are aware of the hazards involved. Our team under no circumstances disclose information to any third party❌❌. The core values adhered by our firm is based on trust and faith. Our expert hacking online Organization supports you on time and reply to any query related to the unique services we offer. 💯
🏅COMPOSITE HACKS is available for customer care 24/7, all day and night. We understand that your request might be urgent, so we have a separate team of allocated hackers who interact with our Clients round the clock⏰. You are with the right people so just get started.💯✅
✅CONTACT US TODAY VIA:✅
📲 compositehacks@gmail.com 📲
I really liked this part of the article, with a nice and interesting topics have helped a lot of people who do not challenge things people should know... you need more publicize this so many people who know about it are rare for people to know this, Success for you. https://topacademictutors.com/write-my-essay/
ReplyDeleteIf you need help you can read this.
ReplyDeleteI had just realised I had made a mistakes at my place of work and these mistakes will get me fired but then my friend introduced me to an organisation of computer geniuses Softtechgeeks@gmail.com that saved my job.
They hacked into the company's data base and helped me correct my mistakes the fun part was that they covered there tracks so well no one knew they were ever in the data base.
I really liked this part of the article, with a nice and interesting topics have helped a lot of people who do not challenge things people should know... you need more publicize this so many people who know about it are rare for people to know this, Success for you. https://liveassignmenthelp.com https://topacademictutors.com/write-essay-for-money/
ReplyDeleteOur diligent team at Tech Support Dubai attends global clients and creates amazing logos to enhance your business across the world. They will assist you with creating a perfect logo for your brand. logo design services dubai
ReplyDeleteThis is amazing guide to Virtual Machine to run multiple windows at same time. I have used the VMware on Mac to run virtual windows. In case any issue visit us MacBook Repair Dubai
ReplyDeleteCLASSIC CYBER HACKS
ReplyDeleteHow well are you prepared for a Cyber incident or Breach?, Is your Data safe?
Strengthen your Cybersecurity stance by contacting CLASSIC CYBER HACKS for a Perfect, Unique, Classic and Professional Job in Securing your Network against all sort of Breache, for we are Specially equipped with the Best hands to getting your Cyber Hack needs met
We specialize in All type of cyber Jobs such as:
#TRACKING of GPS location, cars, Computers, Phones (Apple, windows and Android), e.t.c.
We also track E-mail account, Social media such as Facebook, Twitter, Skype, Whatsapp, e.t.c.
#RECOVERY of Passwords for E-mail address, Phones, Computers, Social media Accounts, Documents e.t.c,.
NOTE: we also help Scammed persons recover their money.
#INSTALLATION of Spy ware so as to spy into someone else's computer, phone or E-mail address and also Installation of Spy ware software on your individual O.S to know if your Gadget is being hacked into..
We also Create and Install VIRUS into any desired computer gadget.
#CRACKING into Websites, CCTV Survelance camera, Data base etc, of both Private and Govt organization, such as Schools, Hospitals, Court houses, The FBI, NSA e.t.c
NOTE: We specialize in clearing of CRIMINAL RECORDS of diverse types.
* We assure you that your Job will be attended to with care and efficiency as it will be handled with the Best professional hands in Cyber Hack business.
#We also have a forum where you can get yourself equipped with Advanced hacking Knowledge
And Also, if you're Good with Hacking and you think you can Join our Team of SOPHISTICATED HACKERS, you're welcome as well...
CLASSIC CYBER HACKS gives you the Best service in the Hacking world.
* We're Classic Hacks *
Write us on:
*Classiccyberhacks@gmail.com
*Classiccybernotch@gmail.com
Signed,
Collins .A.
https://topacademictutors.com/cheap-research-papers/ https://topacademictutors.com/do-my-homework/
ReplyDeleteThe secret of a happy marriage is finding the right person. You know they’re right if you love to be with them all the time happy wedding anniversary message
ReplyDeleteAwesome post.
ReplyDeleteESET NOD32 Customer Service Number
HP Printer Support is a leading company and a renowned brand in the world for printers, scanning devices and printing supplies. This includes Inkjet printers, LaserJet, office jet and related products. Epson Printer Support to individual consumers, to small and medium businesses and large enterprises. However if you look for HP technical support, Printer Support offers.
ReplyDeleteCanon Printer Support |
Brother Printer Support |
Lexmark Printer Support |
Dell Printer Support |
garmin.com/express
Printer support Today in this world of technology, there are many companies which are booming up because of the software as well as hardware services which they offer. Browser Support This has become one of the leading forms of business as computers have entered every nook and corner in today’s world. The competition is also too high, that only those companies which excel in the service provided can survive.
ReplyDeleteGarmin Connect Sign in
Netgear Router Support Number
Support for Quickbooks
Pogo Game Support Number |
garmin.com/express
WOW! IT WAS VERY NICE POST. Coinabase support phone number +1-888-840-3277 The gathering of the inside and out arranged experts are accessible 24*7 to empower you to decide your issues. With the best features, it moreover gives all of you out security while using the organizations and at the events when you are frustrated about any component, similarly causes you out. Any sort of perplexity that inspires an emotional response will be cleared by the pros. In case you have any particular issue, the readied and master experts are there to help you. Coinbase customer organization locks in towards giving their customers the most suitable courses of action and make the customers satisfied after the call. more info visit here: https://www.numbersonweb.com/crypto-wallets/coinbase-support-number/
ReplyDeleteIf you are facing any issues regarding Binance, We are one of the leading
ReplyDeleteBinance support service providers globally. At whatever point you cause hurt while trading on Binance, you may approach Binance Support Phone Number +1-888-840-3277 which is continually handy reliably. The gathering of specialists are continually helpful and have fixes related to the all of the request and burdens that keeps the method for customers. Acknowledge trouble free trading on Binance and if, any issue exists, you can connect with them at whatever point and discard your issues.more data visit here: https://www.numbersonweb.com/crypto-exchanges/binance-support-number/
Fix issues of Binance, Exchange, account rekated and other periphery with the help of Binance Support Number. Blockchain which is clear by the open is broadly utilized by digital forms of money. It is a sort of installment rail and the utilization of private blockchains is done significantly for business purposes. The advertising of such blockchains with no security is alluded to as a Snake oil by Computer world. For any data related with Blockchain, don't hesitate to connect with us by means of Blockchain support phone number. +1-888-840-3277 To put in basic terms, Blockchain is an appropriated record framework which is decentralized. The Blockchain is a new and progressive advance on the planet brimming with innovation. more data visit here: https://www.numbersonweb.com/crypto-wallets/blockchain-support-number/
ReplyDeleteI might not be your “little man” anymore, but you still have all my love
ReplyDeletemotherdayquotesi.com
happy mothers day 2019
happy mother day quotes
Hi, I am an android app developer. I have developed a dating app crazy krush in order to revolutionize the online dating way today teenagers are doing.
ReplyDeletenice post.
ReplyDeletebest Attitude status
AWesome post.
ReplyDeleteBest Attitude Status
This is really awesome, am so glad to read this informative article.
ReplyDeleteThanks for sharing.
Custom Packaging Boxes USA
Hi, this is ludo is a classic board game with unlimited video calling and audio chat features
ReplyDeleteThe first step in custom dissertation writing is the choice of topic. The topic that is chosen by the writer determines the quality of the paper. Contact our research papers 247 company today!
ReplyDeleteHi I am Amy Jones .We provide toll free Amazon Support +1-855-424-9807 to complete help for solving all quarries related to Amazon. Our Support teams are accessible 24X7. Get more information so visit our sites:-
ReplyDeleteAmazon Support Number
ReplyDeleteIf you are having any problems related to AOL Email, then you can Get the instant solution of your AOL issues from the AOL Technical Support team by using AOL Customer Service Number.
AOL Tech Support Phone Number
OUR WEBSITE: http://www.deepsecret.net
ReplyDeleteOUR EMAIL ADDRESS: contact@deepsecret.net
Hi. We are a group of hackers called Deep Secret and we offer hacking services for everyone. Some of our services are:
- Cell phone hacking
- Calls and messages hack
- Get any password from any Email Address.
- Get any password from any Facebook, Twitter or Instagram account.
- Cell phone hacking (whatsapp, viber, line, wechat, etc)
- Grades changes (institutes and universities)
- Websites hacking, pentesting.
- IP addresses and people tracking.
- Hacking courses and classes.
Our services are the best on the market and 100% secure and discreet guaranteed. We also offer proof before payment.
Just write us and ask for your desired service:
OUR WEBSITE: http://www.deepsecret.net
OUR EMAIL ADDRESS: contact@deepsecret.net
OUR WEBSITE: http://www.deepsecret.net
OUR EMAIL ADDRESS: contact@deepsecret.net
Hi. We are a group of hackers called Deep Secret and we offer hacking services for everyone. Some of our services are:
- Cell phone hacking
- Calls and messages hack
- Get any password from any Email Address.
- Get any password from any Facebook, Twitter or Instagram account.
- Cell phone hacking (whatsapp, viber, line, wechat, etc)
- Grades changes (institutes and universities)
- Websites hacking, pentesting.
- IP addresses and people tracking.
- Hacking courses and classes.
Our services are the best on the market and 100% secure and discreet guaranteed. We also offer proof before payment.
Just write us and ask for your desired service:
OUR WEBSITE: http://www.deepsecret.net
OUR EMAIL ADDRESS: contact@deepsecret.net
OUR WEBSITE: http://www.deepsecret.net
OUR EMAIL ADDRESS: contact@deepsecret.net
Hi. We are a group of hackers called Deep Secret and we offer hacking services for everyone. Some of our services are:
- Cell phone hacking
- Calls and messages hack
- Get any password from any Email Address.
- Get any password from any Facebook, Twitter or Instagram account.
- Cell phone hacking (whatsapp, viber, line, wechat, etc)
- Grades changes (institutes and universities)
- Websites hacking, pentesting.
- IP addresses and people tracking.
- Hacking courses and classes.
Our services are the best on the market and 100% secure and discreet guaranteed. We also offer proof before payment.
Just write us and ask for your desired service:
OUR WEBSITE: http://www.deepsecret.net
OUR EMAIL ADDRESS: contact@deepsecret.net
I am here to testify about how total company change my life,it was like this,i read about online trade and investment,when searching on how to trade with legit company,i ment a review which said i can invest in oil and gas company,where i can invest $5000 USD into oil and gast ,which i did after reaching total company,out end of my trade,i make a profit worth $65,0000 USD after investing with now through out thirty one days ,it real great i ment this company which change my life,i said to myself,it is better to share this on topix and forum,so that financial problem can reduce,what have your government offer to reduce financial problem,it is better you help yourself,because the system of the countries are not after our dealy bread,you can invest and get rich too,email total company at: total.company@aol.com
ReplyDeleteIt is anything but difficult to discover these boxes, and any customization can be initiated in accordance with the inventiveness and originality of the customer’s item.
ReplyDeleteIf You Amazon prime Support Service needed to the most competitive online you can also avail our live chat or email service mode for the better experience. you can also visit our site and call on this number Support number+1-855-424-9807 or more visit go on
ReplyDeleteAmazon Customer Service
Nice Blog ...
ReplyDeleteAmazon Customer Service
Amazon Customer Service Number
Amazon Support Number
Nice blog! I am glad you share this blog with us. If you are looking for Amazon support team because of the issues you are facing you can contact them at any time.
ReplyDeleteAmazon support number
Amazon phone number
Amazon customer service number
Amazon support phone number
Amazon customer support number
If you want to rank your website then two things need to keep in mind first one is content and the second one is SEO. After put content SEO is the most important things for any website. It can help you to reach the targeted audience. So our suggestion to choose some best SEO company in kolkata who properly read your website and doing SEO.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteAquarium always needs good Aquarium Lighting, because it also provides energy to photosynthetic plants and animals. So make your aquarium lighting perfect so that you fish make healthy.
ReplyDeleteOne Search Point organized the customer service system that can be easy to accessed through Coinbase customer support number +1-855-504-2315. Our professional available 24/7 to help their users resolve the query
ReplyDeletehttps://www.onesearchpoint.com/coinbase
https://coinbasesupportnumberservice.blogspot
We are a team of expert that offer you Binance support services which be the best subsititute for you to deal with your uphold sign in and other related issues. Our professionals at uphold phone number… deal with any of account related issue like password recovery forget password . our Binance Support Number +1-888-330-0764 team is at your service 24*7
ReplyDeletehttps://binanceexchange-support-number.blogspot.com
Binance Support Number
https://www.onesearchpoint.com/binance-support-number
https://binancesupportus.blogspot.com
Google Pay claims to transfer your money to friends and family account more easily and fast than through your bank by using the internet. When you send money to a friend or family facing error call us toll-free https://www.onesearchpoint.com/googlepay-customer-service
ReplyDeletehttps://www.onesearchpoint.com/googlepay-customer-service
https://www.onesearchpoint.com/binance-support-number
https://binanceexchange-support-number.blogspot.com
https://coinbasesupportnumberservice.blogspot.com
Would you like to introduce Dell printer mistake freeway or you are not proficient to introduce your Dell printer at that point Don't inconvenience here you can get straightforward strides to introduce your Dell printer without CD. You can contact Dell Printer Support Phone Number +1-833-260-7367 get the best online help for Dell printer issues like printer establishment, printer not working, printer not printing, printer not reacting and a lot more issues identified with Dell Printer. You may likewise visit at their official site address to discover more
ReplyDeleteDell Printer Support Phone Number
https://www.onesearchpoint.com/dell-printer-support-phone-number
Dell Printer Support Phone Number
Dell is a worldwide organization, Dell produces a wast scope of electronic gadgets and has a colossal scope of business auxiliaries over the world. Dell has been rendering some inventive, high-caliber, and adaptable printers just to finish clients' printing, checking, faxing, photocopying needs in only one gadget. Besides, In the Dell Printed confronting some specialized glitches you should contact with the experts who might give total answers for the issue and they would likewise help the clients through Dell Printer Support Phone Number +1-833-260-7367
ReplyDeleteDell Printer Support Phone Number
https://www.onesearchpoint.com/dell-printer-support-phone-number
Dell Printer Support Phone Number
Dell Printer support team is extraordinary compared to other client support group which help you in settling numerous types of Dell printer issues. In this way, at whatever point your Dell printer is causing any issues, you simply need to whip out your phone and dial the Dell Printer Customer Support Number +1-833-260-7367. The group will quickly come into salvage and help you in investigating issues. In addition, the group will give you all day, every day administration possibly to determine your issues when you get them. The group comprises of prepared masters who help you in distinguishing and redressing the issue.
ReplyDeleteDell Printer Support Phone Number
https://www.onesearchpoint.com/dell-printer-support-phone-number
Dell Printer Support Phone Number
I am very happy to see this post because it is very useful for me, because there is so much information in it. I always like to read quality and I'm happy that I got this thing in your post. Thanks for sharing the best article post.
ReplyDeleteZelle Support Number
ReplyDeleteWe have the best knowledge in all the academic disciplines. If you are an university student and need assistance in completing your dissertation then worry no more and get dissertation writing proposal from the professional writers of My Assignment Help
Staggering post to Improve a lot of experience, Command on the most suitable economics assignment help online different assignment support with most university students. 10% OFF On every separate. economics assignment help online
ReplyDelete
ReplyDeleteWhat a fantastic post! This is so full of useful information I can't wait to dig deep and start utilizing the resources you have given me.Your exuberance is refreshing.NetSuite Partners in India
NuVista Technologies is the preferred Consulting and Implementation Partner of NetSuite. Specializes in NetSuite Implementation, Integration, Consulting and Managed Services. Nuvista Headquartered in Singapore and India, also has Portfolio across Singapore, India, UAE, and Africa.
NetSuite Partners in India
moving companies
ReplyDeletelong distance moving quotes online
moving labor services
moving cost calculator
moving guides
auto transport service
storage units near me
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com
Hey Guys !
ReplyDeleteUSA Fresh & Verified SSN Leads AVAILABLE with best connectivity
All Leads have genuine & valid information
**HEADERS IN LEADS**
First Name | Last Name | SSN | Dob | DL Number |Address | State | City | Zip | Phone Number | Account Number | Bank Name
*Price for SSN lead $2
*You can ask for sample before any deal
*If anyone buy in bulk, we can negotiate
*Sampling is just for serious buyers
==>ACTIVE & FRESH CC FULLZ ALSO AVAILABLE<==
->$5 PER EACH
->Hope for the long term deal
->Interested buyers will be welcome
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Corporate gifts Singapore by FOTO88.com.sg - customized corporate gift leader in Singapore. Visit us and find innovative corporate gift ideas for your clients.
ReplyDeleteI want to tell you that I am new to weblog and definitely like this blog site. It is very possible that I am going to bookmark your blog. You have amazing stories. Thanks for sharing the best article post. Coronavirus Updates India COVID Tally Crosses 16 Lakh and the 55079 Positive Cases
ReplyDeleteHello everyone, Are you into trading or just wish to give it a try, please becareful on the platform you choose to invest on and the manager you choose to manage your account because that’s where failure starts from be wise. After reading so much comment i had to give trading tips a try, I have to come to the conclusion that binary options pays massively but the masses has refused to show us the right way to earn That’s why I have to give trading tips the accolades because they have been so helpful to traders . For a free masterclass strategy kindly contact (paytondyian699@gmail.com) for a free masterclass strategy. He'll give you a free tutors on how you can earn and recover your losses in trading for free..
ReplyDeleteHello Everyone !
ReplyDeleteUSA SSN Leads/Fullz available, along with Driving License/ID Number with good connectivity.
All SSN's are Tested & Verified.
**DETAILS IN LEADS/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL
->EMPLOYEE DETAILS
*Price for SSN lead $2
*You can ask for sample before any deal
*If you buy in bulk, will give you discount
*Sampling is just for serious buyers
->Hope for the long term business
->You can buy for your specific states too
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Best HypospadiasTreatment in Delhi
ReplyDeleteHypospadiasTreatment in Delhi
Best HypospadiasTreatment in Delhi
Best IVF Treatment Hospital in Noida
We offer custom boxes that give you full liberty of customizing the entire packaging at every step. Packaging is the first thing a customer notices. It has to be spot on to appeal to the customers. The visual appeal ticks a customer before they could actually choose a product. Packaging is the first impression we are committed to make that leaves a lasting impact on the customers.
ReplyDeleteSmall Cardboard Boxes
Soap Boxes
Slider Boxes
Nail Polish Boxes
Lipstick Boxes
Pillow Boxes
Custom Lip Balm Boxes
Hello Everyone, I'm Mike Gary from pheonix Arizona USA. Congrats to everyone who Benefited from the Investment I shared I still want more people to benefit Ask me how And I will show you how to make good profits
ReplyDelete$500 ------ $2,500
$1,000 ------ $5,000
$2,000 ----- $10,000
$3,000 ----- $15,000
$4,000 ---- $20,000
$5,000 ---- $25,000
The signal is high for now
Start up investment and earn directly to your wallet or Bank account after 24hours of trading sure profits without no delay make a choice from the list.
Legit trading100%guaranteed
You can kindly inbox me if interested. no risk
involved 100% safe Interested just write me on
WhatsApp +1 (520) 367-0578
At this time I am ready to do my breakfast, when having my breakfast coming again to read additional news.
ReplyDeleteExcellent article. I definitely love this website. Stick with it!
ReplyDeleteI Want to use this medium to appreciate an online ghost hacker, after being ripped off my money he helped me find my cheating lover and helped me hacked his WHATSAPP, GMAIL, kik and all his social media platforms and i got to know that he has being cheating on me and in less than 24 hours he helped me out with everything, hacking setting is trust worthy, contact him via: hackingsetting50@gmail.com
ReplyDeleteSelling USA FRESH SPAMMED SSN Leads/Fullz, along with Driving License/ID Number with EXCELLENT connectivity.
ReplyDelete**PRICE**
>>2$ FOR EACH LEAD/FULLZ/PROFILE
>>5$ FOR EACH PREMIUM LEAD/FULLZ/PROFILE
**DETAILS IN EACH LEAD/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYEE DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>All Leads are Tested & Verified.
>Invalid info found, will be replaced.
>Serious buyers will be welcome & I will give discounts for bulk orders.
>Fresh spammed data of USA Credit Bureau
>Good credit Scores, 700 minimum scores
>Bulk order will be preferable
>Minimum order 20 leads/fullz
>Hope for the long term business
>You can asked for samples, specific states & zips (if needed)
>Payment mode BTC, PAYPAL & PERFECT MONEY
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
''OTHER GADGETS PROVIDING''
>Dead Fullz
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>USA emails with passwords (bulk order preferable)
**Contact 24/7**
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
**SELLING SSN+DOB FULLZ**
ReplyDeleteCONTACT 24/7
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
>>1$ each without DL/ID number
>>2$ each with DL
>>5$ each for premium (also included relative info)
Price will be reduce in Bulk order
FORMAT OF LEADS/FULLZ/PROS
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->COMPLETE ADDRESS
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYMENT DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>All Leads are Spammed & Verified.
>Fresh spammed data of USA Credit Bureau
>Good credit Scores, 700 minimum scores
>Invalid info found, will be replaced.
>Payment mode BTC, ETH, LTC, PayPal, USDT & PERFECT MONEY
''OTHER GADGETS PROVIDING''
>SSN+DOB Fullz
>CC with CVV
>Photo ID's
>Dead Fullz
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>HQ Emails with passwords
Contact 24/7
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
I appreciate Fred for making me realise the truth to a certified hacker who knows a lot about what his doing. I strongly recommend you hire him because his the best out there and always delivers. I have referred over 10 people to him and all had positive results. He can help you hack into any devices, social networks including – Facebook, Hangout, iMessages, Twitter accounts, Snap chat , Instagram, Whatsapp, wechat, text messages ,smartphones cloning,tracking emails and also any other social media messenger or sites. It’s advisable to hire a professional hacker.Thank me later. Contact him here. fredvalcyberghost@gmail.com and you can text or call him on +1- (423)641 1452 or on WhatsApp +1 (470) 777-2098
ReplyDeleteBuena información
ReplyDeleteSMO and SMM
ReplyDeleteIndependant Call Girls in Delhi
Brother Printer Troubleshooting
Icloud SMTP Server Setup
Avast Antivirus Help
Delhi Escort Services
Roku Tech Support for Technical Problems
It¦s really a nice and useful piece of information. I¦m glad that you just shared this helpful information with us. Please keep us informed like this. Thank you for sharing. 바카라사이트
ReplyDeleteRight away I am ready to do my breakfast, later than having my
ReplyDeletebreakfast coming again to read additional news. 토토사이트
SSN FULLZ AVAILABLE
ReplyDeleteFresh & valid spammed USA SSN+Dob Leads with DL available in bulk.
>>1$ each SSN+DOB
>>3$ each with SSN+DOB+DL
>>5$ each for premium fullz (700+ credit score with replacement guarantee)
Prices are negotiable in bulk order
Serious buyer contact me no time wasters please
Bulk order will be preferable
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
OTHER STUFF YOU CAN GET
SSN+DOB Fullz
CC's with CVV's (vbv & non-vbv)
USA Photo ID'S (Front & back)
All type of tutorials available
(Carding, spamming, hacking, scam page, Cash outs, dumps cash outs)
SQL Injector
Premium Accounts (Netflix, Pornhub, etc)
Paypal Logins
Bitcoin Cracker
SMTP Linux Root
DUMPS with pins track 1 and 2
WU & Bank transfers
Socks, rdp's, vpn
Php mailer
Server I.P's
HQ Emails with passwords
All types of tools & tutorials.. & much more
Looking for long term business
For trust full vendor, feel free to contact
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
hi
ReplyDeletethat I bookmark your blog and will often come back at some point.
ReplyDeleteAlso visit my website :
토토
Usually I never comment on blogs but your article is so convincing that I never stop myself to say something about it. You’re doing a great job Man, Keep it up 카지노사이트
ReplyDelete토토사이트 Have you ever considered writing an e-book or guest authoring on other sites? I have a blog centered on the same information you discuss and would love to have you share some stories/information. I know my audience would enjoy your work. If you are even remotely interested, feel free to send me an e-mail
ReplyDelete==>Contact 24/7<==
ReplyDelete**Telegram > @leadsupplier
**ICQ > 752822040
**Skype > Peeterhacks
**Wickr me > peeterhacks
**SSN FULLZ WITH HIGH CREDIT SCORES AVAILABLE**
>For tax filling/return
>SSN dob DL all info included
>For SBA & PUA filling
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING CARDING CASHOUTS CLONING**
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*SSN Fullz All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA AVAILABLE
SSN+DOB
SSN+DOB+DL
High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid info found, will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS Available For:
(Carding, spamming, hacking, scripting, scam page, Cash outs, dumps cash outs)
=>Ethical Hacking Tools & Tutorials
=>Kali linux
=>Facebook & Google hacking
=>Bitcoin Hacking
=>Bitcoin Flasher
=>SQL Injector
=>Bitcoin flasher
=>Viruses
=>Keylogger & Keystroke Logger
=>Logins Premium (Netflix, coinbase, FedEx, PayPal, Amazon, Banks etc)
=>Bulk SMS Sender
=>Bitcoin Cracker
=>SMTP Linux Root
=>DUMPS track 1 and 2 with & without pin
=>Smtp's, Safe Socks, rdp's, VPN, Viruses
=>Cpanel
=>PHP mailer
=>Server I.P's & Proxies
=>HQ Emails Combo (Gmail, yahoo, Hotmail, MSN, AOL, etc)
->Serious buyers are always welcome
->Big discount in bulk order
->Discounted Offers will give time to time
->Hope we do a great business together
==>Contact 24/7<==
**Telegram > @leadsupplier
**ICQ > 752822040
**Skype > Peeterhacks
**Wickr me > peeterhacks
I really like it when people come together and share ideas. Great website, keep it up! 경마
ReplyDeleteThanks for sharing this knowledgeable post. What an excellent post and outstanding article. Thanks for your awesome topic. Really I got very valuable information here. If you want to Recover Roadrunner Email Password please contact roadrunner support team for solution.
ReplyDeleteMmorpg oyunları
ReplyDeleteInstagram takipçi satın al
TİKTOK JETON HİLESİ
Tiktok jeton hilesi
Saç ekim antalya
instagram takipçi satın al
Instagram takipçi satın al
metin2 pvp serverlar
İNSTAGRAM TAKİPCİ SATİN AL
ReplyDeleteThanks for your Post! Please Visit Here:
subgiks
healthmagazineus
smm panel
ReplyDeleteSmm Panel
İş ilanları
İnstagram Takipçi Satın Al
Https://www.hirdavatciburada.com/
BEYAZESYATEKNİKSERVİSİ.COM.TR
SERVİS
tiktok jeton hilesi
çekmeköy lg klima servisi
ReplyDeletetuzla toshiba klima servisi
tuzla beko klima servisi
maltepe samsung klima servisi
tuzla mitsubishi klima servisi
çekmeköy vestel klima servisi
ataşehir vestel klima servisi
çekmeköy bosch klima servisi
ataşehir bosch klima servisi
Thanks for sharing. BEglobalus offers the Web Development Services in Michigan. You can quickly boost online traffic and attract more customers with proper assistance.
ReplyDeleteICQ 752822040 / @killhacks
ReplyDeleteEmail hacksp007 @dnmx.org
Telegram @leadsupplier / @killhacks
What's App +92 317 272 1122
Fresh Fullz SSN DOB DL & High Credit
UK\US\CANADA fullz with SSN/SIN
Fresh CC's with cvv & ssn info
Dumps with/without pin (track 101 & 202)
EIN Compny Fullz
SBA/PUA/UI/Tax retrun Fresh fullz
Office 365 Leads & Logins
Combos/I.p's/Proxies
H-acking|Spamming|Carding Tools & Tutorials
Cash out Methods, Loan Methods
SMTP|RDP|SHELLS|C-PANELS|WEB-MAILERS
SQLI Injector/Python
Server Penetration/Scam Pages
Kali Linux Full Tuts
SMTP Linux root/Scam Page Scripting
Many other Tools & Tuts we can provide
Fullz/Pros will be Fresh, Valid & Legit
Payment Mode BTC|USDT|Perfect Money|ETH
CRYPTOCURRENCY INVESTMENT
ReplyDeleteRecording the success in Cryptocurrency, Bitcoin is not just buying and holding till when bitcoin sky-rocks, this has been longed abolished by intelligent traders ,mostly now that bitcoin bull is still controlling the market after successfully defended the $20,000 support level once again and this is likely to trigger a possible move towards $40,000 resistance area However , it's is best advice you find a working strategy by hub/daily signals that works well in other to accumulate and grow a very strong portfolio ahead. I have been trading with Mr Bernie doran daily signals and strategy, on his platform, and his guidance makes trading less stressful and more profit despite the recent fluctuations. I was able to easily increase my portfolio in just 3weeks of trading with his daily signals, growing my 0.9 BTC to 2.9BTC. Mr Bernie’s daily signals are very accurate and yields a great positive return on investment. I really enjoy trading with him and I'm still trading with him, He is available to give assistance to anyone who love crypto trading and beginners in bitcoin investment , I would suggest you contact him on WhatsApp : + 1424(285)-0682 , Gmail : BERNIEDORANSIGNALS@GMAIL.COM for inquiries , Bitcoin is taking over the world
⬆️🇺🇸🇺🇸🇺🇸⬆️
⬆️🇺🇸🇺🇸🇺🇸⬆️
⬆️🇺🇸🇺🇸🇺🇸⬆️
yurtdışı kargo
ReplyDeleteresimli magnet
instagram takipçi satın al
yurtdışı kargo
sms onay
dijital kartvizit
dijital kartvizit
https://nobetci-eczane.org/
U8DVRV
salt likit
ReplyDeletesalt likit
dr mood likit
big boss likit
dl likit
dark likit
NZ0
Hollanda yurtdışı kargo
ReplyDeleteİrlanda yurtdışı kargo
İspanya yurtdışı kargo
İtalya yurtdışı kargo
Letonya yurtdışı kargo
O22
Witness the artistry of R&M Healing Buddha as it crafts new horizons of global wellness, intertwining diverse energy healing modalities to sculpt a tapestry of well-being.
ReplyDeletehealingbuddha
Portekiz yurtdışı kargo
ReplyDeleteRomanya yurtdışı kargo
Slovakya yurtdışı kargo
Slovenya yurtdışı kargo
İngiltere yurtdışı kargo
ETR38S
salt likit
ReplyDeletesalt likit
P48MH
salt likit
ReplyDeletesalt likit
dr mood likit
big boss likit
dl likit
dark likit
1YZR8
We bring you stories of those who challenge norms, create impact, and leave a lasting legacy.
ReplyDeletetheglobalhues
Verified & Updated FULLZ|PROS|INFO|LEADS
ReplyDeleteUSA UK CANADA All States Available
Fresh Database & Never used before
Available in bulk quantity
SSN DOB DL ADDRESS EMPLOYEE & BANK INFO USA
SIN DOB ADDRESS MMN CANADA
NIN DOB DL ADDRESS SORTCODE UK
High Credit Scores Fullz
Young Age Fullz
Business EIN Company Fullz
CC with CVV
Dumps with Pin Track 101 & 202
Real|Original ID|DL Front Back & Selfie with SSN
Passport Photos with Selfie
Fullz with expiry dates
UberEats|Doordash Fullz with KYC Stuff
Bulk Quantity available
Old Age Fullz
Premium Leads|Info|Pros
You can asked for specific info like Cities|States|Zip|Gender|Age
Hacking Spamming Carding Tools & Tutorials available as well
For Order & Details feel free to ping us
(at)leadsupplier , (at)killhacks Tel. gram
(at)killhacks , 752822040 I C Q
hacksp007 (at) DNMX . org E mail
(at)peeterhacks Skype
747 Media House is your trusted partner for exceptional Link Building Services, designed to elevate your digital presence. Our expert team utilizes cutting-edge techniques to acquire high-quality backlinks, significantly enhancing your website’s authority and search engine rankings. With 747 Media House, expect a substantial increase in organic traffic, improved brand visibility, and sustainable growth. Partner with us to achieve outstanding online success and maximize your business potential. Experience the difference with 747 Media House, the leader in delivering top-tier link building solutions.
ReplyDeleteSSN DOB DL ADDRESS MMN FULLZ USA
ReplyDeleteSIN DOB DL ADDRESS MMN CANADA
NIN DOB DL ADDRESS SORT CODE UK
FULLZ AVAILABLE UK USA CA DL SCAN PROS MVR TELEGRAM:KILLHACKS
Fresh Fullz available in bulk quantity
Recent spammed & verified fullz
Guaranteed stuff with full replacement offer
= Telegram > @ leadsupplier | @ killhacks
= Whats App > +1.. 727.. 788... 6129..
= Skype > @ peeterhacks
= E mail > cyber.zoneunivese at g>mail . com
DL Scan front back with selfie & SSN
DL Fullz with MVR
DL Fullz with issue & Expiry dates
SSN DOB DL ADDRESS Bank & Employee info Fullz
DL fullz EIN & Front back scan
UK NIN dob dl address sort code info fullz
UK DL Scan Front Back with Selfie
UK CC's with CVV's & billing address
Canada SIN DOB DL ADDRESS MMN info Fullz
Canada DL Scan Front back with selfie
Canadian CC's with CVV's address
USA UK CANADA Young & Old Age Fullz
High credit scores Pros USA UK CA (700+ Scores)
Business EIN USA Company Pros Fullz
Passport Photos with selfie
Fullz for Loan & Credit applying & KYC Stuff
Tools for Hacking|Spammming|Carding|Scripting
SMTP|RDP
C-panels
Shells
Web-mailers
Bulk SMS Sender
Email Blaster
Carding & Cash out Methods with video tutorials
Scam pages & Scam Page Scripting
Spamming Complete Package with all Tools & Tutorials with 100k Email Leads
Fresh tools available
No sampling for CC's & Tools
Tutorials will be provided if you want
Contact us for more stuff & Fullz info
🚨🚨 YOU EVER GOT SCAMMED, THEN YOU SHOULD READ THIS 🚨🚨🚨
ReplyDeleteYou could probably get your money back, and I said probably, This is because most scammers don't move the money to a bank account, most scammers move it to a crypto currency wallet or a local money saving platforms, this way they stay undetected and noticed by authorities.
What you have to keep in mind is, this crypto wallet can be reported or hacked into, and this is what we do.
WHO ARE WE⁉️ YOU MIGHT ASK❗❕❗❕
We are ⭐PYTHONAX⭐ a group of skilled and experienced internet and computer experts. We have refocused our work force into tracking down scammers and helping victims of scam recover their money, or what's left of it. Using our experience in transactions tracking and jail breaking, we can now guarantee scam victims an opportunity to recover their money.
There are so many ways to get scammed in the world we live in today, majority of this scams are internet based scam, one of the major disadvantages of the internet. Here are examples of scams we have dealt with and can help such victims to this scams as well-:
❌Cryptocurrency investments scammed victims.
❌Forex/Binary Option investments scam victims.
❌Buying and Selling scam victims.
❌Dating & Romance scam victims.
❌Loans scams victims.
❌Housing & Estate Investments Scam victims. E.t.c.
How services are simple and and a breakdown of each steps of the process we will take to help you get your money back would be explained and told to you, what we do isn't illegal, we try and follow the rules and make sure you aren't involved in any crime. You can choose to remain anonymous, your personal info wouldn't be required of you, all we need are infos regarding the scam, infos like-:
1️⃣ Total Amount of what you were scammed.
2️⃣ The type of scam you were involved in.
3️⃣ The means of Communication you used in communicating with the scammers. Eg, emails, numbers or social media handles......
4️⃣ Details of which you used to make payments and transactions ID.
Do not feel shy or ashamed or stupid, this scammers are really good at what they do, they make everything look so real and convince and very very real like the actual real stuff.
Use this emails below to contact us-:
PYTHONAXHELP@PROTONMAIL.COM
PYTHONAXSERVICES@PROTONMAIL.COM
We assure you of no form of judgmets or guilt, we are professionals and only want to help.
Hello Everyone
ReplyDeleteHere we come with updated & Fresh spammed FULLZ
Fullz of USA UK Canada in Bulk quantity
New Year sale offers|Christmass offer for Bulk buyers
SSN DOB DL
SIN DOB ADDRESS MMN
NIN DOB DL ADDRESS Sort Code
Contact us here anytime
What's App = +1... 727.... 788.. 6129...
Tele Gram = @ killhacks & @ leadsupplier
Skype = @ peeterhacks
E mail = dghcks2 t g mail dot com
USA SSN DOB DL ADDRESS Fullz
Real DL Photos Front Back with SSN
Business EIN Company Pros Fullz
Young & Old Age fullz (2000+ & 1960 below)
DL fullz with issue & expiry Dates
Fullz with MMN CC CVV
Dead Fullz|Live Fullz|Sweepstakes
You guy's can get specific info fullz as well
Age|Gender|City|State|Zip specific
UberEats & Doordash KYC info Pros Fullz
UK NIN DOB DL ADDRESS
NIN DOB ADDRESS Sort Code
UK Real DL Front Back with Selfie
Canada SIN DOB ADDRESS MMN Phone Email
All States available
Canada DL Front Back with Selfie
All stuff will br fresh & Valid guaranteed
No sampling for low quantity
Available everytime
Ping Us for fresh info Fast
ID's|DL Photos limited fresh stock available
#USAFULLZ #UKFULLZ #CANADAFULLZ #SSNFULLZ #NINFULLZ #SINFULLZ
#DLPHOTOSSCAN #USAUKCANADAINFO #DLDOCS #CCCVVSELL #DUMPSCVV
#PROSFULLZUSA #SSNDOBDL #SINDOBMMN #NINDOBSORTCODE
What's App = +1... 727.... 788.. 6129...
Tele Gram = @ killhacks & @ leadsupplier
Skype = @ peeterhacks
E mail = dghacks2 at g mail dot com
You’re such an amazing hacker verifiedprohackers@gmail.com thank you for being able to hack into my late husband MacBook Pro. This meant a lot to me because have been worried on how to get his passwords ever since he passed away but you verifiedprohackers@gmail.com made it possible for me. Thank you so much.
ReplyDeleteA Funding Account with FundedFirm presents traders with an excellent opportunity to scale their trading activities by leveraging firm-provided capital, offering a transparent, trader-friendly environment that prioritizes success and flexibility. This prop trading firm allows traders to access up to $100,000 in trading capital with no restrictions on trading styles such as scalping or news trading, thanks to its flexible rules and no imposed maximum or minimum evaluation days, alleviating pressure during the evaluation phase. Traders benefit from high profit-sharing potential, with payouts starting at 90% and scaling up to 100%, combined with rapid payout processing, often within 24 hours, which is among the fastest in the industry. The platform supports MetaTrader 5, providing advanced trading tools, seamless execution, and high leverage of up to 1:100, making it suitable for both novice and experienced traders. Multiple payment options, including UPI, cater particularly to Indian traders, enhancing convenience. Overall, a funding account with FundedFirm empowers traders to grow their skills and profits in a risk-managed, supportive environment, making it one of the most attractive prop trading options in 2025.
ReplyDeleteFRESH 2026 DATABASE
ReplyDeleteUSA DATABASE
UK DATABASE
CANADA DATABASE
TOOLS & TUTORIALS
TELE/GRAM...@Malisa72
>US cc Fullz
>Email leads with Password
>HACKING & CARDING TUTORIALS
>SMTP LINUX
>Spamming Tutorial
>SERVER I.Ps
>EMAIL COMBO
>DUMPS TUTORIAL
>BTC FLASHER
>Dumps track 1 & 2 with pin and without pin
>KEYLOGGER COMP&MOB
>EMAIL BOMBER
>SQLI INJECTOR
>HACKING TUTORIAL
>GMAIL HACKING TUTORIAL
>PENETRATION TESTING TUTORIAL
>PayPal Cracker
>BTC Cracker
>BLUE PRINTS BLOCKCHAIN
>ONION LINKS AND TOR BROWSER (LATEST VERSION)
>DARK HORSE TROJAN
>NETFLIX CHECKER
>IP ROUTING
>KEYSTROKE LOGGER
>WESTERN UNION LOGINs
>ALI BABA IPs
>KEYLOGGER
>SHELL SCRIPTING
Superior quality and reliable connectivity
Every leads are carefully inspected
offer full support with client
payment method(BTC,ETH,USDT,LTC&PAYPAL)