Previously, we discussed a quick short list of wireless chipsets to research in order to best handle packet injection. And packet injection, my friends, is what it's all about. Our main goal, when dealing with wireless, is being able to inject enough packets into the stream in order to generate the information we need to break the encryption key. We'll discuss this in depth later on. For now, we need to select an affordable card that can handle three main key elements of wireless sniffing:
- The cards need to be able to handle the spectrum of frequencies we want to monitor: 802.11B, 802.11G and 802.11N. There are other types of wireless in use today, but these are the three main types of wireless you find “out in the wild”.
- The cards must be able to be placed into “monitor mode”, the ability of a card to “listen” to a network, rather than just “speak” to it.
- The cards must be able to handle “packet injection”, the ability to inject packets, thus creating enough viable packets for us to crack WEP encryption
So, our short list of viable cards included:
- Atheros (AR5XXX, AR9XXX)
- Broadcom (B43XX Family)
- Intel Pro Wireless and Intel Wifi Link (Centrino)
- Ralink (RT2X00)
- Realtek (RTL8187)
If you were to purchase a brand-new laptop and were able to do a little research prior to purchase, you might find that your internal wireless card actually has one of those chipsets on board. The ASUS K52F that I use for writing, email and other boring technical activities has an atheros-based wireless card. What does this mean? Well, I can do any of the tips and tricks we'll discuss later on on my shiny ASUS laptop. For just starting out and just for learning, this is a fine thing. If you were lucky enough to purchase a new laptop for learning how to do Penetration Testing, then I would recommend you start out with a card like this. All the exercises we'll go through later will be just as applicable.
However, if you're putting together your Essential Toolkit, already have a laptop that doesn't have a wireless card or you're serious about doing wireless surveillance, you're eventually going to want to get a wireless card with one of these chipsets AND an external antenna connector. Why? Well, there are lots of applications for a wireless card with an external antenna. Some hackers have been able to hook them up to powerful antennae, potato chip cans, and even old satellite dishes (you know, for Satellite Dish Cable in your home) to gain some absolutely wonderful distance on their surveillance. You, too, will probably eventually want to tinker with applications like this. So I think it would be best to add a USB wireless card (with an external antenna connector) to your Essential Toolkit.
Let's discuss this a bit.
I've done quite a bit of research and the cards that I find give you the best bang for the buck is a pair of cards from a company called 'Alfa Network'. They have 2 cards that are inexpensive and use the Ralink chipset. There are two models that are most prevalent.
- Alfa AWUS036NEH – 1000mW USB Wifi Adapter (with threaded RP-SMA) Antenna Jack
- Alfa AWUS036H – 2000mW USB Wireless Adapter (with threaded RP-SMA) Antenna Jack
RP-SMA, for those of you who don't know, designates the kind of threaded adapter that you can screw on. For our purposes, this connector for the antenna is just fine. You can see it very clearly in the top right picture shown here:
So, you've got a the 36NEH which is slightly less powerful than the 36H. They both handle 802.11 B/G/and N, so you get the best coverage for wireless networks. And here's the kicker: the 2000mW version comes in at approximately $30 + shipping while the 1000mW version (which, frankly is just as useful as the 2000mW version) can be had for a stunningly low $20.
You can pick up either of these cards through a number of places, if you use Google's Shopping site. Amazon carries them and a few others. However, I picked up my AWUS036NEH at Data Alliance (http://www.data-alliance.net/-strse-61/alfa-500mW-USB-Wireless/Detail.bok) but you could also pick up the 2000mW version from them here: http://www.data-alliance.net/-strse-158/Alfa-AWUS036NH-2000mW-1000mW/Detail.bok
The reason I decided to spend the $20 on an external USB wireless card is because of the ease of use when it comes to getting things working in BackTrack. Here's my $20 Alfa AWUS036NEH:
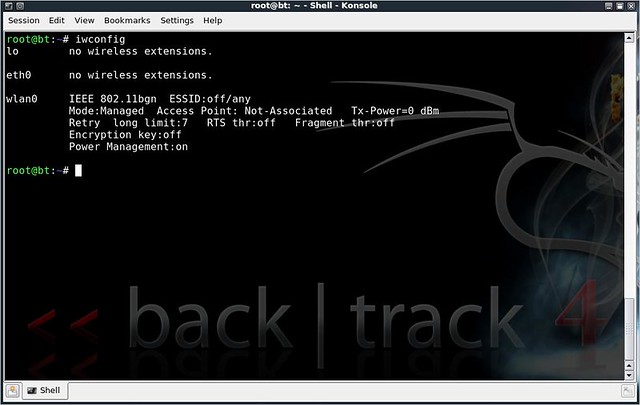
The Ralink chipset in the AWUS036NEH works just this easy:
Once that is run, if the right driver is loaded and all is well, you will see a message saying '(monitor mode enabled on mon0)' or something close to that. If you see monitor mode is enabled, you have the right card, the right drivers and everything's set for you to work wireless magic later on. If you don't see that, then you might need to do a little googling and find exactly what card, what chipset you have and see if there are any known issues with that card in the BackTrack forums.
For more information, you can check out the aircrack-ng website. They maintain a compatibility list that details wireless cards, chipsets and the like. You can find that compatibility list here: http://www.aircrack-ng.org/doku.php?id=compatibility_drivers . By perusing that list and doing a little bit of research, you may be able to find another card that best suits your needs. For me and for the lessons we'll be covering, I find the $20 Alfa card to be a best buy.
Just make sure, that if you decided to go with an external USB wireless card, you should always get one with an external antenna. This lets you have the most flexibility in your wireless sniffing. Once you get deeper into wireless sniffing and cracking, you'll be most disappointed by NOT having an external antenna.
Next up, we'll discuss the few small items we want to include in our Essential Toolkit and wrap up making our kit. Then we'll start to work out our penetration testing methodology.





Hello I have k54 L Asus laptop and of course it came with an Atheros wireless card which quite frankly seems to have trouble finding the occasional errant signal. My question is will it have the flexibility you described earlier my card is an AR9285. Thank you Ozzy
ReplyDeleteOzzy:
DeleteI have an Asus K52, which is similar in spec. I would say that if you're looking to learn the Aircrack suite in BackTrack, your built-in Atheros card will work with the utilities just fine. You'll learn everything you need to about cracking wifi.
However, I've found the internal card is limited in the distance you can cover (meaning, you can't consistently grab packets from APs if their too far away). However, if you're standing up a wifi AP in your house for playing around with in a lab environment, you're going to be fine.
GET YOUR BLANK ATM CARD AND BE RICH FOREVER EMAIL: DICKSONBLANKATMHACKER@GMAIL.COM
DeleteAlicia Orlando by name from USA.. i am here to share this message of greatness to only those who will seize the opportunity life will offer to become somebody great and actualize their dreams.so happy I got mine from Mr Dickson. My blank ATM card can withdraw 5000 dollars daily. I got it from Him last week and now I have 50000 dollars monthly. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr.Dickson because i met two people before him and they took my money not knowing that they were scams. But am happy now. Mr Dickson sent the card through UPS Express Delivery Shipment, and i got it in 4 days. Get your own card from him now he is not like other scammer pretending to have the ATM card,he is giving it out to help people even if it is illegal but it helps a lot and no one ever gets caught.Start living your big dreams, living that large and comfortable life that you always wised for, contact email: dicksonblankatmhacker@gmail.com cell whatsapp/ +12048178403 and make your purchase immediately.
GET YOUR BLANK ATM CARD AND BE RICH FOREVER EMAIL: DICKSONBLANKATMHACKER@GMAIL.COM
DeleteAlicia Orlando by name from USA.. i am here to share this message of greatness to only those who will seize the opportunity life will offer to become somebody great and actualize their dreams.so happy I got mine from Mr Dickson. My blank ATM card can withdraw 5000 dollars daily. I got it from Him last week and now I have 50000 dollars monthly. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr.Dickson because i met two people before him and they took my money not knowing that they were scams. But am happy now. Mr Dickson sent the card through UPS Express Delivery Shipment, and i got it in 4 days. Get your own card from him now he is not like other scammer pretending to have the ATM card,he is giving it out to help people even if it is illegal but it helps a lot and no one ever gets caught.Start living your big dreams, living that large and comfortable life that you always wised for, contact email: dicksonblankatmhacker@gmail.com cell whatsapp/ +12048178403 and make your purchase immediately.
Good day to all viewer online..Hacker Atm card is right here and get rich immediately and take money directly from any ATM Machine Vault with the use of our ATM Programmed Card which runs in automatic mode.This is an opportunity you all have been waiting for. Get the new programmed ATM BLANK CARD that can hack any ATM MACHINE and withdraw money from any where in the world. it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr Dickson because i met two people before me and they took my money not knowing that they were scams. But am happy now.Mr Dickson sent the card through DHL and i got it in 24hours. Get your own card from Mr Dickson now he is not like other scammer pretending to have the ATM card,Mr Dickson is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Mr Dickson because he changed my story all of a sudden . The card works in all countries except,his whatsapp number +12048178403 or email him:dicksonblankatmhacker@gmail.com
DeleteGood day to all viewer online..Hacker Atm card is right here and get rich immediately and take money directly from any ATM Machine Vault with the use of our ATM Programmed Card which runs in automatic mode.This is an opportunity you all have been waiting for. Get the new programmed ATM BLANK CARD that can hack any ATM MACHINE and withdraw money from any where in the world. it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr Dickson because i met two people before me and they took my money not knowing that they were scams. But am happy now.Mr Dickson sent the card through DHL and i got it in 24hours. Get your own card from Mr Dickson now he is not like other scammer pretending to have the ATM card,Mr Dickson is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Mr Dickson because he changed my story all of a sudden . The card works in all countries except,or his email: dicksonblankatmhacker@gmail.com
DeleteIf Truly you Are In Need Of A PROFESSIONAL HACKER Who Will Get Your Job Done Efficiently With Swift Response, You Have Met the Right Person.
DeleteANONYMITY:
I don't care who you are. The reason why I am hired is to simply get the job done.
I engage in"silent" attacks so the target remains unaware of the hack.
MY HACKING CAPABILITIES:
No job is too small, no job is too difficult. There are series of people who needs to crack their target email I.D for many reasons such as husband cheating on wife, girlfriend cheating on boyfriend or vice versa. Or important information needed to be dumped from the target email address or for whatsoever reason you want to hack your target email (gmail, hotmail, outlook, yahoomail,). Or if you want to hack a private domain email account(business email), Facebook, Twitter, contact me.
Frankly speaking, I always give a 100% guarantee on any job I am been asked to do, because I have always been successful in all my job for the past 10years and my clients can testify to that . To hack anything needs time though, but I can provide a swift response to your job depending on how fast and urgent you need. Time also depends on what exactly you want to hack and how serious you are. Enough time with social engineering is required for hacking. So if you want to bind me in a short time, then just don't contact me because I can't hack within one hour,*sorry*. Basically, time depends on your luck. If its good luck, then it is possible to hack within one hour but, if its in the other way round, it would take few hours. I have seen FAKE HACKERS claiming they can hack in 1hr , but there is no REAL HACKER who can say this (AVOID THEM).
If your target account is Facebook, MySpace, Twitter, sexual accounts or other social accounts etc, or you want to hack into someones smartphone so you can monitor their calls, read their messages, chats, and social account activities without their notice, feel free to contact me and we would have a nice deal! I will explain to you how I am going to get the job done.
HACKING A WEBSITE
Perhaps, many people want to hack their target website for their personal reasons. I am enough experienced and skilled in hacking websites and getting access to database and I am providing the web hacking services. It may be for database access, database dump, getting access to a specific information, defacing, maybe for political reasons or competitor company etc. I dont care what type of site you will give me to pen test. Is it high profile or low profile or medium profile, I will do my possible best (just be sure that you are not going to make it a real crime otherwise I will ignore you).
PAYMENT:
PLEASE, think how much you will be paying for your job and don't waste time offering 100$ or 200$ (because we will require higher than that, depending on what you want to hack and the hack tool we are going to use.
I accept various secure payment methods that maintains your anonymity. However, bank direct deposits and/or transfers are not accepted due to federal tracking laws.
You can contact me for any other type of "hijacking and attacks". I do almost everything.
Compositehacks@gmail.com
PLEASE READ!!!! Hello Guys,This is a Life Time transformation !!!Am so happy I got mine from Elizabeth. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $8,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Elizabeth because i met two people before her and they took my money not knowing that they were scams. But am happy now. Elizabeth sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Elizabeth because she changed my story all of a sudden . The card works in all countries except Philippines, Mali and Nigeria. Elizabeth's email address is elizabethcole232@yahoo.com
Delete
DeleteATM CARD
I Lost my Money to scammers but not anymore
Well, who would have believed this. When I saw a comment
by one Allison babara, I thought it was one of the Scammers
ways to convince someone. Looking at his comment, I saw
an element of doubt since he was telling stories. Well I did it
50/50 which means I can’t lose my money to any scammer
again. I contacted the email on the testimony of Allison?
Babara (securehackers01@gmail.com) and I was
replied immediately. I was shocked but I didn’t lose my stand.
I asked them to give me proof to be sure they are not
scammers like others that I have met before and they sent me
a proof. Then I requested to get my card which they sent to
me in Germany in just 3 days. Am happy now because I have?
recovered my cash I lost to scammers. My first withdrawal?
was $10,000 and I couldn’t believe my eyes until I confirmed?
their word which says that I can withdraw up $63,000 in a
month. secureblankatmSolution? are real because I got my?
card in just 3 days when I requested for one. Contact their
mail (securehackers01@gmail.com ) for yours. They
didn’t scam me.
Morris mabel is my name and if you are scared, please reach
me through my mail dasinator02@gmail.com
INSTEAD OF GETTING A LOAN, CHECK OUT THE BLANK ATM CARD IN LESS THAN 24hours {blankatmhaker@gmail.com}
DeleteAm Mark Oscar,I want to testify about Jack Robert blank ATM cards which can withdraw money from any ATM machines around the world. I was very poor before and have no hope then I saw so many testimony about how Jack Robert send them the ATM blank card and use it to collect money in any ATM machine and become rich. I also email him and he sent me the blank card. I have use it to get 70,000 dollars. withdraw the maximum of $5,000 daily. Jack Robert is giving out the card just to help the poor. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email Him on how to get it now via: blankatmhaker@gmail.com or call/Text on +1(406) 350-4986
◾ "PROTOCOL SHIELDERS" ◾
DeleteHello,
I am COREY RODRIGUEZ by name, THE CEO of protocol & cyber-sheild hackers.
In this message, we will explain how you can almost avoid SCAMMERS and stay safe, plus how our organisation works.
Read it carefully!!
Its reading will not take more than 10mins.
We kindly URGE you to not respond without have read the entire text. Those who mail without have read everything, ask questions that are answered here!!
WARNING:
MOST HACKERS YOU SEE HERE ARE FAKES
AND INCONGUROUS!!.
It tears me up when we receive bitter emails for Jobs with complains from most clients with hacking issues about past SCAMs by uncertified fake hackers like most you see here, which is disappointingly inadequate, leaving their mess for us to deal with eventually (WE DON'T MEAN TO BRAG ABOUT THAT).
HOW WOULD YOU KNOW??
You won't know until you fall a Victim but can be attentive to potential danger, error or harm if you take note of these:
1, you see uncertified email accounts carrying numberings like
"iamhacklord1232@(gmail,yahoo or hotmail.com"
pls flee from them, BIG SCAMMERS.
They take your money and never do your job!!
2, you see posts like "do you need to spy on spouse?"
All fake! , just a way to lure you toward getting ripped OFF!.
3, posting fake testimonies and comments to trick you into feeling save and secured.
Pls endeavour to ignore!!
4,beware as we urge you not to make respond to any "IVAN HONG" (impersonating with our post pretending to work for us) with this exact post.
◾VERY IMPORTANT ◾
For years now, We've helped organisations secure data base, so many sites has been hacked for different reasons of Job kinds.
"CLEAR CRIMINAL RECORDS" & "iPhone HACK" of
and in short timing hacked petty cyber sites accounts like Skype, Fb, WhatsApp,Tinder,Twitter!!, FLIPPED MONEY, LOAD CCs and vice versa but these are significant experiences a good and effectively recognized organisation
must firmly ascertain.
◾OUR "AIMS" HERE ◾
Are:
1◾to assign a qualified agent of specific rank to particularly any sort of cyber issues you intend dealing with in short and accurate timing.
2◾ to screen in real hackers (gurus only) in need of job with or without a degree, to speed up the availability of time given to for Job contracts.!!
Thus an online binary decoding exam will be set for those who seeks employment under the teams Establishment.
write us on:
◾Protocolhacks@gmail.com or
◾Cybershieldnotch@gmail.com
◾Cybershieldnotch@protonmail.com,
COREY ROD,
SIGNED...!
Thank you!!!
SKype <<--<- rushr00t000
DeleteHangout <<--<- hackitbackd00r@gmail.com
Yahoo mail hackitbackdoor@gmail.com <<--<-
Reseller Bank login & westerunion bug + credit card + leads
-i serve all service is depend condition on demand looking a serious buyers
-I spam as clients demand or sell stolen data in bulk we dont sell one or two accounts
-must pay for tools or arrive after 3 days into your gmail get step by step
-also teach spamming carding or logins and tools reseller and google know us anonymously
--+++-----------+++--
Prepaid gift card or credit card
-balance minimum - maximum prize %30 to 40%
-2000$-5000$ 30$ random 50$ fullz
-dob ssn mmn gov id including all deatils
-For any multiple countrys bins we spam as demand
--+++-----------+++--
westerunion bug transfer fees
-1000$ in 200$
-2000$ in 400$
-3000$ in 300$
--+++-----------+++--
spamming tools
-random cpnal 6$
-cpnal http secure 25$
-shell 15$
-random shell 5$
-random smtp 12$
-unlimted blast smtp 35$
-mailer 4$
-unlimted blast mailer 25$
-webmailer 5$
-unlimted blast webmailer 15$
-simple scam-page 30$
-Latter 10$
-script scam-page any bank or cc 70$
-ceo or cfo leads bulk 50k 30$
--+++-----------+++--
carding tools
-rdp 40$
-vip72 45$ unlimted
-socks 35$
--+++-----------+++--
Virus Builder crupter
-keyloger 40$
-stealer 50$
-zeus trojan 80$
-rat 60$
-slinet crupter 70$
-builder 30$
-privet virus hosting one month 50$
--+++-----------+++--
reseller R00ts vps Host
-whm script Crack 250$
-whm cpnal unlimted 6 month 150$
-scanner r00t unlimted 3 month 60$
-whm linux r00ts 140$
-normal r00t 40$ to 70$ limited Bandwidth
-rdp vps 120$ limited Bandwidth 10 country
-smtp server 110$ unlimted 1 year
--+++-----------+++--
linux privet scanners
SSH Brute Force scaner: 200$ (windows based) (ssh roots or required for run)
smtp scanner : 350$ (linux bassed) (ssh/root required for run )
rdp scnnaer : 400$ (linux bassed) (ssh/root required for run)
Smtp+rdp multi scanner : 600$ (linux bassed) (ssh/root required for run)
cpanel scanner : 500$ (linux bassed) (ssh/root + 10 cpanel or shell required for run)
root scanner : 800$ (linux bassed) (ssh/root required for run)
--+++-----------+++--
Scanner windows based
-any crack softwere or script 300$
-valn sql injection 3pack solution 140$
-http port scanner 150$
-smtp port scanner 140$
-ftp scanner 120$
-user pass bruter 150$
--+++-----------+++--
contact us--
SKype <<--<- rushr00t000
Hangout <<--<- hackitbackd00r@gmail.com
Yahoo mail hackitbackdoor@gmail.com <<--<-
Hello Everyone,
DeleteMy name is Nicholas Shields, The CEO of COMPOSITE HACKS. I am here to Let you know how you can know if your spouse is cheating on you.
If probably you’ve been have an atom of doubt about your spouse based on his/her late behaviors, you can catch him/her Red Handed‼️
HOW??
🏅COMPOSITE HACKS⚔️ is a vibrant squad of dedicated online hackers maintaining the highest standards and unparalleled professionalism in every aspect.
We Are One Of The Leading Hack Teams in The United States🇺🇸🇺🇸 With So many Accolades From The Dark Web and the IT Companies🏆🏅🥇. In this online world there is no Electronic Device we cannot hack. Having years of experience in this Job, We Can Provide the Following Services:
✅Website hacking 💻,✅Facebook and social media hacking📲, ✅Database hacking, Email hacking⌨️, ✅Phone and Gadget Hacking📲💻,✅Clearing Of Criminal Records❌ ✅Location Tracking and many More✅
• We Can help you HACK into your spouse’s phone and give you unnoticeable access to everything they are doing on their phone Which includes Messages, Calls, Social media Apps e.g WhatsApp, Facebook, Instagram etc. as long as the App is installed on their phone.
🏅We have a trained team of seasoned professionals under various skillsets when it comes to online hacking services. Our company in fact houses a separate group of specialists who are productively focussed and established authorities in different platforms. They hail from a proven track record and have cracked even the toughest of barriers to intrude and capture or recapture all relevant data needed by our Clients. 📲💻
🏅 COMPOSITE HACKS understands your requirements to hire a professional hacker and can perceive what actually threatens you and risk your business⚔️, relationships or even life👌🏽. We are 100% trusted professional hacking Organization and keep your deal entirely confidential💯. We are aware of the hazards involved. Our team under no circumstances disclose information to any third party❌❌. The core values adhered by our firm is based on trust and faith. Our expert hacking online Organization supports you on time and reply to any query related to the unique services we offer. 💯
🏅COMPOSITE HACKS is available for customer care 24/7, all day and night. We understand that your request might be urgent, so we have a separate team of allocated hackers who interact with our Clients round the clock⏰. You are with the right people so just get started.💯✅
✅CONTACT US TODAY VIA:
📲 compositehacks@gmail.com 📲
★COMPOSITE HACKS★
Delete🔍🔍Are you Seeking for the Best Legit Professional Hackers online??❓💻💻💻
Congratulations Your search ends right here with us. 🔍🔍🔍🔍
🏅COMPOSITE HACKS is a vibrant squad of dedicated online hackers maintaining the highest standards and unparalleled professionalism in every aspect.
We Are One Of The Leading Hack Teams in The United States🇺🇸🇺🇸 With So many Accolades From The IT Companies🏆🏅🥇. In this online world there is no Electronic Device we cannot hack. Having years of experience in serving Clients with Professional Hacking services, we have mastered them all. You might get scammed for wrong hacking services or by fake hackers on the Internet. Don't get fooled by scamers that are advertising false professional hacking services via False Testimonies, and sort of Fake Write Ups.❌❌❌❌
* COMPOSITE HACKS is the Answers to your prayers. We Can help you to recover the password of your email, Facebook or any other accounts, Facebook Hack, Phone Hack (Which enables you to monitor your kids/wife/husband/boyfriend/girlfriend, by gaining access to everything they are doing on their phone without their notice), You Wanna Hack A Website or Database? You wanna Clear your Criminal Records?? Our Team accepts all types of hacking orders and delivers assured results to alleviate your agonies and anxieties. Our main areas of expertise include but is never confined to:
✅Website hacking 💻,✅Facebook and social media hacking📲, ✅Database hacking, Email hacking⌨️, ✅Phone and Gadget Hacking📲💻,✅Clearing Of Criminal Records❌ ✅Location Tracking✅ Credit Card Loading✅ and many More✅
🏅We have a trained team of seasoned professionals under various skillsets when it comes to online hacking services. Our company in fact houses a separate group of specialists who are productively focussed and established authorities in different platforms. They hail from a proven track record and have cracked even the toughest of barriers to intrude and capture or recapture all relevant data needed by our Clients. 📲💻
🏅 COMPOSITE HACKS understands your requirements to hire a professional hacker and can perceive what actually threatens you and risk your business⚔️, relationships or even life👌🏽. We are 100% trusted professional hacking Organization and keep your deal entirely confidential💯. We are aware of the hazards involved. Our team under no circumstances disclose information to any third party❌❌. The core values adhered by our firm is based on trust and faith. Our expert hacking online Organization supports you on time and reply to any query related to the unique services we offer. 💯
🏅COMPOSITE HACKS is available for customer care 24/7, all day and night. We understand that your request might be urgent, so we have a separate team of allocated hackers who interact with our Clients round the clock⏰. You are with the right people so just get started.💯✅
✅CONTACT US TODAY VIA:✅
📲 compositehacks@gmail.com 📲
Selling good and fresh cvv fullz
Deletetrack 1 and 2 with pin
bank login
bank transfer
writing cheques
transfer to cc ...
Sell Fresh CVV - Western Union Transfer - Bank Login - Card Dumps - Paypal - Ship
Fresh Cards. Selling Dumps, Cvvs, Fullz
Tickets,Hotels,Credit card topup...Paypal transfer, Mailer,Smtp,western union login,
Book Flight Online
SELL CVV GOOD And HACKER BIG CVV GOOD Credit Card
Fresh Cards. Selling Dumps, Cvvs, Fullz.Tickets,Hotels,Credit cards
Sell Cvv(cc) - Wu Transfer - Card Dumps - Bank login/paypal
And many more other hacking services
contact me : hackerw169@gmail.com
whatsapp: +1 613-701-6078
- I have account paypal with good balance
- I hope u good customers and will be long-term cooperation
Prices WesternUnion Online Transfer
-Transfer(Eu,Uk,Asia,Canada,Us,France,Germany,Italy and very
easy to do African)
- 200$ = 1500$ (MTCN and sender name + country sender)
- 250$ = 4000$ (MTCN and sender name + country sender)
- 400$ = 6000$ (MTCN and sender name + country sender)
- 500$ = 8000$ (MTCN and sender name + country sender)
Then i will do transfer's for you, After about 30 mins you'll have
MTCN and sender name + country sender
- Dumps prices
- Tracks 1&2 US = 85$ per 1
- Tracks 1&2 UK = 100$ per 1
- Tracks 1&2 CA / AU = 110$ per 1
- Tracks 1&2 EU = 120$ per 1
Bank Logins Prices US UK CA AU EU
- Bank Us : ( HALIFAX,BOA,CHASE,Wells Fargo...)
. Balance 5000$ = 250$
. Balance 8000$ = 400$
. Balance 12000$ = 600$
. Balance 15000$ = 800$
. Balance 20000$ = 1000$
- Bank UK : ( LLOYDS TSB,BARCLAYS,Standard Chartered,HSBC...)
. Balance 5000 GBP = 300 GBP
. Balance 12000 GBP = 600 GBP
. Balance 16000 GBP = 700 GBP
. Balance 20000 GBP = 1000 GBP
. Balance 30000 GBP = 1200 GBP
contact me : hackerw169@gmail.com
whatsapp: +1 613-701-6078
I'm hacker and Services provider
Deleteintersted in any thing i do fair deals.
I will show you each and everything
also teaching
Western Union transfer
I have all tools that you need to spam
Credit cards.. money adders.. bill paying
College fee.. fake documents.. grade change
Contact me:
skype : ianscarffe_1
gmail : omoskovitz@gmail.com
ICQ : 728612475
Hello, I purchased the Alfa AWUS036NEH 1000mW 1W 802.11g/n High Gain USB Wireless G / N Long-Rang WiFi Network Adapter., I cannot get it to work with Cain and Abel in monitor/promiscuous mode for packet capture and injection. I appreciate any feedback on how to fix this problem.
ReplyDeleteAnonymous in May:
DeleteI found several videos on youtube that demonstrate how to use Cain and Abel for wifi capture. If you're determined to move forward with Cain and Abel, I would definitely reference some of them.
However, my personal recommendation would be to ditch Windows entirely, boot up BackTrack and start to use the Aircrack suite. The Alfa adapter you have purchased is well supported in Linux and it is really just so easy to use in BackTrack. If you want easy success in minutes, get your hands on that.
That may not be the answer you're entirely looking for. Sorry.
If Truly you Are In Need Of A PROFESSIONAL HACKER Who Will Get Your Job Done Efficiently With Swift Response, You Have Met the Right Person.
DeleteANONYMITY:
I don't care who you are. The reason why I am hired is to simply get the job done.
I engage in"silent" attacks so the target remains unaware of the hack.
MY HACKING CAPABILITIES:
No job is too small, no job is too difficult. There are series of people who needs to crack their target email I.D for many reasons such as husband cheating on wife, girlfriend cheating on boyfriend or vice versa. Or important information needed to be dumped from the target email address or for whatsoever reason you want to hack your target email (gmail, hotmail, outlook, yahoomail,). Or if you want to hack a private domain email account(business email), Facebook, Twitter, contact me.
Frankly speaking, I always give a 100% guarantee on any job I am been asked to do, because I have always been successful in all my job for the past 10years and my clients can testify to that . To hack anything needs time though, but I can provide a swift response to your job depending on how fast and urgent you need. Time also depends on what exactly you want to hack and how serious you are. Enough time with social engineering is required for hacking. So if you want to bind me in a short time, then just don't contact me because I can't hack within one hour,*sorry*. Basically, time depends on your luck. If its good luck, then it is possible to hack within one hour but, if its in the other way round, it would take few hours. I have seen FAKE HACKERS claiming they can hack in 1hr , but there is no REAL HACKER who can say this (AVOID THEM).
If your target account is Facebook, MySpace, Twitter, sexual accounts or other social accounts etc, or you want to hack into someones smartphone so you can monitor their calls, read their messages, chats, and social account activities without their notice, feel free to contact me and we would have a nice deal! I will explain to you how I am going to get the job done.
HACKING A WEBSITE
Perhaps, many people want to hack their target website for their personal reasons. I am enough experienced and skilled in hacking websites and getting access to database and I am providing the web hacking services. It may be for database access, database dump, getting access to a specific information, defacing, maybe for political reasons or competitor company etc. I dont care what type of site you will give me to pen test. Is it high profile or low profile or medium profile, I will do my possible best (just be sure that you are not going to make it a real crime otherwise I will ignore you).
PAYMENT:
PLEASE, think how much you will be paying for your job and don't waste time offering 100$ or 200$ (because we will require higher than that, depending on what you want to hack and the hack tool we are going to use.
I accept various secure payment methods that maintains your anonymity. However, bank direct deposits and/or transfers are not accepted due to federal tracking laws.
You can contact me for any other type of "hijacking and attacks". I do almost everything.
Compositehacks@gmail.com
PLEASE READ!!!! Hello Guys,This is a Life Time transformation !!!Am so happy I got mine from Elizabeth. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $8,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Elizabeth because i met two people before her and they took my money not knowing that they were scams. But am happy now. Elizabeth sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Elizabeth because she changed my story all of a sudden . The card works in all countries except Philippines, Mali and Nigeria. Elizabeth's email address is elizabethcole232@yahoo.com
DeleteINSTEAD OF GETTING A LOAN, CHECK OUT THE BLANK ATM CARD IN LESS THAN 24hours {blankatmhaker@gmail.com}
DeleteAm Mark Oscar,I want to testify about Jack Robert blank ATM cards which can withdraw money from any ATM machines around the world. I was very poor before and have no hope then I saw so many testimony about how Jack Robert send them the ATM blank card and use it to collect money in any ATM machine and become rich. I also email him and he sent me the blank card. I have use it to get 70,000 dollars. withdraw the maximum of $5,000 daily. Jack Robert is giving out the card just to help the poor. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email Him on how to get it now via: blankatmhaker@gmail.com or call/Text on +1(406) 350-4986
thx for yr document i have one question i buy dell n5110 laptob ist suitable for hacking wireless because i want to start learning
ReplyDeleteand if i want to buy wireless card which type i must have adaper or access point or wireless modem because i go to computer market and dnt know exactly
Question - can one do this on a VMWare image running Ubuntu inside of a Win7 host? I am guessing not, because all traffic still goes through the Windows drivers
ReplyDeleteSteve you can connect your cards usb into backtrack with vmware and seperate it from the windows drivers.
ReplyDeleteVmware will disconnect the card from windows and connect it through itself which works just fine when loaded with ubuntu backtrack or what ever distro people prefer.
PLEASE READ!!!! Hello Guys,This is a Life Time transformation !!!Am so happy I got mine from Elizabeth. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $8,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Elizabeth because i met two people before her and they took my money not knowing that they were scams. But am happy now. Elizabeth sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Elizabeth because she changed my story all of a sudden . The card works in all countries except Philippines, Mali and Nigeria. Elizabeth's email address is elizabethcole232@yahoo.com!
DeleteHere is the issue with Cain and Abel if you actually know what to look for you would see that the software starts sniffing your own network and starts to dial home. Explicit Warning when using the application. Stick to linux when pentesting.
ReplyDeletePLEASE READ!!!! Hello Guys,This is a Life Time transformation !!!Am so happy I got mine from Elizabeth. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $8,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Elizabeth because i met two people before her and they took my money not knowing that they were scams. But am happy now. Elizabeth sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Elizabeth because she changed my story all of a sudden . The card works in all countries except Philippines, Mali and Nigeria. Elizabeth's email address is elizabethcole232@yahoo.com!
DeleteHi, I got the AWUS036NEH dongle and I'm currently using it with Backtrack5 R2 gnome 64 bits, the thing is working because I was able to crack WPA2, however it seems that it has an awful working range, I am only able to get two wifi connections with it (and one it's mine :S), and around eight to ten with the built-in wifi adapter of my laptop.
ReplyDeleteDo you have any advise for me? Maybe some configuration I could try? I've already tried boosting the power to 30db, didn't change anything.
There seems to be some information (and similar notes to yours about range) here: http://www.backtrack-linux.org/forums/showthread.php?t=32993 Don't know if this will help but there's some info on it there.
DeleteASUSTeK Computer Inc Product Name: K54L comes stock with
ReplyDeleteAtheros Communications Inc. AR9285 Wireless Network Adapter (PCI-Express) 8gigs ram 500gb HD perfect for injection using Kali linux $329.00 out the door. sweet for on the go
I built one of these as I live in the catskills anyway after a little soldering and a useless dish and a few bucks I was able to receive over 4000 connections averaging 10 miles away no joke. http://www.engadget.com/2005/11/15/how-to-build-a-wifi-biquad-dish-antenna/
ReplyDeleteI got the AWUS036NEH and I am using Kali Linux.
ReplyDeleteThe dongle won't work on the newest Kali Linux version. I had to get the .deb package firmware-ralink for wheezy and install it.
But it seems the firmware with that doesn't support monitoring, any suggestions?
I really searched the web for hours, reading forums, articles and so on. But I cannot find a working solution.
I hope you might help.
I have a HP G series with a ralink rt5390 802.11b/g/n wifi adapter and cant get backtrack 5 to recognise it in when i pull up my term, any suggestions? I did check to make sure the software was updated on the driver, and its the most up to date there is, just kinda lost as to what I as what i should do next should i just go and buy another adapter and be done with it?
ReplyDeletechecking the systems for the vulnerabilities is penetration testing, and if you don.t have high quality wi fi than its very hard to do this. so have good wi fi connection
ReplyDeleteenlace wifii
Thanks for sharing. Learn a lot from your Blog.I have read your blog about it-security-matter It is very help full.I really enjoyed reading it, you may be a great author.I must say you've done a wonderful job by sharing your article with us.Penetration Testing UK
ReplyDelete
ReplyDeleteI totally agree with this,
and in fact I was about to mention some importance of satellite dish installer insurance in my comment below.
It’s certainly a fact that helps makes us work more and faster.see more
satellite dish installer insurance
i have a dell laptop
ReplyDeletedell inspiron 3521
i dont know anything about its inbult wifi
how to find it also
when i try iwconfig in my kali linux it didnt showed my card
how to install its driver ????
BEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS OR TO START LIVING A
ReplyDeleteGOOD LIFE.....
Hack and take money directly from any ATM Machine Vault with the use of ATM
Programmed Card which runs in automatic mode. email (lasscold@gmail.com) for how to get it and its cost .
CALL ME +2348168631153
.......... EXPLANATION OF HOW THESE CARD WORKS..........
You just slot in these card into any ATM Machine and it will automatically
bring up a MENU of 1st VAULT $1,000, 2nd VAULT $5,000, RE-PROGRAMMED, EXIT,
CANCEL. Just click on either of the VAULTS, and it will take you to another
SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the
amount you wish to withdraw from the ATM and you have it cashed
instantly... Done.
To get the card email (lasscold@gmail.com)
CALL ME +2348168631153
NEED A HACKED ATM CARD WITH PIN?
ReplyDeleteWe sell physical loaded ATM cards . It is a corned card that can be used to withdraw Cash at any ATM Machine. This Cards comes in Visa/Master card. Therefore it works at any ATM Machine that accept Visa/master card Worldwide.
CAN I USE THIS READY MADE ATM CARD TO BUY STUFF IN STORES? OR ONLINE SHOPPING? PAY BILLS?
Yes, with this physical ATM card, you can use it to pay stuff at stores through POS. With this ATM card information, you can use it online to pay bills or do online shopping. When you order for this card, Full information about the card will be given to you. We also reload your card when funds exhausted.
DO I NEED TO ORDER NEW CARD EVERY TIME I SPENT THE FUNDS FINISH?
No, if you have already ordered our card, there is no need to keep ordering new cards, Just contact us for a reload. We shall easily reload the ATM card already in your possession
HOW LONG DOES IT TAKE TO RECEIVE ATM CARD IN MY COUNTRY?
If you are in the USA, you will receive your card in 48 HOURS with guaranteed. If you are outside the USA, Your card will arrive to you between 3 – 5 business days guaranteed.
HOW SAFE IS THIS CARD?
It is 100% safe to use this card. Because it will be shipped to you as a gift card.
DO YOU ALSO RELOAD ANY OTHER CARD NOT FROM THIS CRONED CARDS?
Yes, we can reload any Active and valid cards, any type of card just contact us for a reload (prepaid cards, credit/debit cards).
HOW DO I ORDER FOR THE ATM CARD?
Send us an Email: WILSONATMHACKER@GMAIL.COM OR ADD ON WHATSAPP NUMBER +2349038420842 NOW
HOW DO WE MAKE THIS CARD?
we use a machine MSR to crone this cards . You can also buy this machine from us at $850 Only. You can order for the ATM card either the designed card or the blank card but still same information on them.
if you are interested, send an email to WILSONATMHACKER@GMAIL.COM
INSTEAD OF GETTING A LOAN, CHECK OUT THE BLANK ATM CARD IN LESS THAN 24hours {blankatmhaker@gmail.com}
DeleteAm Mark Oscar,I want to testify about Jack Robert blank ATM cards which can withdraw money from any ATM machines around the world. I was very poor before and have no hope then I saw so many testimony about how Jack Robert send them the ATM blank card and use it to collect money in any ATM machine and become rich. I also email him and he sent me the blank card. I have use it to get 70,000 dollars. withdraw the maximum of $5,000 daily. Jack Robert is giving out the card just to help the poor. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email Him on how to get it now via: blankatmhaker@gmail.com or call/Text on +1(406) 350-4986
If you need to hack into any database, delete record, improve credit score, spy on whatsapp, text, phone, emails, as long as it's hack contact Black@v ia Email :: worldspy86@yahoo.com Whats-App ::+27747340647 he is great, you won't be disappointed, cheap and fast, he saved my relationship Tell him Shade
ReplyDeleteThanks to Smith he made me find a solution to my cheating spouse if you need to hack into any database, delete record, improve credit score, spy on whatsapp, text, phone, emails, as long as it's hack contact Smith Email:: lorddatabase@gmail.com And Whats App at (+1) 319-512-6937 he saved my relationship i am so grateful ::: Tell him Bailey
ReplyDeleteGET YOUR BLANK ATM CARD AND BE RICH FOREVER EMAIL: DICKSONBLANKATMHACKER@GMAIL.COM
ReplyDeleteAlicia Orlando by name from USA.. i am here to share this message of greatness to only those who will seize the opportunity life will offer to become somebody great and actualize their dreams.so happy I got mine from Mr Dickson. My blank ATM card can withdraw 5000 dollars daily. I got it from Him last week and now I have 50000 dollars monthly. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr.Dickson because i met two people before him and they took my money not knowing that they were scams. But am happy now. Mr Dickson sent the card through UPS Express Delivery Shipment, and i got it in 4 days. Get your own card from him now he is not like other scammer pretending to have the ATM card,he is giving it out to help people even if it is illegal but it helps a lot and no one ever gets caught.Start living your big dreams, living that large and comfortable life that you always wised for, contact email: dicksonblankatmhacker@gmail.com cell whatsapp/ +12048178403 and make your purchase immediately.
GET YOUR BLANK ATM CARD AND BE RICH FOREVER EMAIL: DICKSONBLANKATMHACKER@GMAIL.COM
ReplyDeleteAlicia Orlando by name from USA.. i am here to share this message of greatness to only those who will seize the opportunity life will offer to become somebody great and actualize their dreams.so happy I got mine from Mr Dickson. My blank ATM card can withdraw 5000 dollars daily. I got it from Him last week and now I have 50000 dollars monthly. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr.Dickson because i met two people before him and they took my money not knowing that they were scams. But am happy now. Mr Dickson sent the card through UPS Express Delivery Shipment, and i got it in 4 days. Get your own card from him now he is not like other scammer pretending to have the ATM card,he is giving it out to help people even if it is illegal but it helps a lot and no one ever gets caught.Start living your big dreams, living that large and comfortable life that you always wised for, contact email: dicksonblankatmhacker@gmail.com cell whatsapp/ +12048178403 and make your purchase immediately.
Hello , are you in any financial problems or you are finding it very difficult to pay your bills? or you need money to start a new business ? if yes then email us today to get a Blank ATM Programmed Card and cash money directly in any ATM Machine around you. You can withdaw $1200 daily and the card is programmed with efficient and unique technology It's 100% guaranteed secure with no worries, there is no risk of being caught, because the card has been programmed in such a way that it's not traceable, it also has a technique that makes it impossible for the CCTV to detect you. Now email us today at our E-mail address at: johnsiphas@gmail.com and get your card today and live that luxury life you every dream to live.
ReplyDeleteContact Mr John Siphas at johnsiphas@gmail.com
Good day to all viewer online..Hacker Atm card is right here and get rich immediately and take money directly from any ATM Machine Vault with the use of our ATM Programmed Card which runs in automatic mode.This is an opportunity you all have been waiting for. Get the new programmed ATM BLANK CARD that can hack any ATM MACHINE and withdraw money from any where in the world. it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr Dickson because i met two people before me and they took my money not knowing that they were scams. But am happy now.Mr Dickson sent the card through DHL and i got it in 24hours. Get your own card from Mr Dickson now he is not like other scammer pretending to have the ATM card,Mr Dickson is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Mr Dickson because he changed my story all of a sudden . The card works in all countries except,his whatsapp number +12048178403 or email him:dicksonblankatmhacker@gmail.com
ReplyDeleteIf you need to hack into any database, delete record, improve credit score, spy on whatsapp, text, phone, emails, as long as it's hack contact Frank @v ia Email :: hackanydatabase98@gmail.com Whats-App ::+1(507)3127027 he is great, you won't be disappointed, cheap and fast, he saved my relationship
ReplyDeleteI have my ATM card already programmed to withdraw the maximum of $ 4,000 a day for a maximum of 20 days. I'm so happy with this because I got mine last week and I've used it to get $ 44,000. Mr Martins is giving the card just to help the poor and needy even though it is illegal but it is something nice and it is not like another scam pretending to have the ATM cards blank. And no one gets caught when using the card. Get yours today by sending a mail to martinshackers22@gmail.com
ReplyDeleteTo hack any website, email, mobile phone (call, text message, Whatsapp, bbm), social network (fbk, twitter, Instagram) change your grades, find your target password (friends, wife, husband, boss, girl, boy friends) to know if they are cheating or not...Contact jack, Email ; ( dhackerjack@gmail.com ) .Whats-App ::+60167569133
ReplyDeleteDavidbenjaminltd@outlook.com is indeed the right place to get your blank ATM card. Much has been said about this company which i saw online about their reliability and certified services am reaffirming this because i have tested them too and they are trusted. I got my card 4 days ago and it took just 2 days for it to be delivered to me after i made all necessary payments. If you are tired of wasting your money an time on fake companies then davidbenjaminltd@outlook.com is the right place
ReplyDeleteWhatever you need to hack,there's a genuine proffessional hacker, graduate from oxford university who does his work
ReplyDeleteto your satisfaction before recieving payment.contact him; Jamiehacking99@gmail.com; +1 571-441-2342.
I got my already programmed and blanked ATM card to
ReplyDeletewithdraw the maximum of $50,000 MONTHLY for a maximum of 12 MONTHS. I am so happy about this because i got mine last week
and I have used it to get $150,000 already. Georg Bednorz Hackers is giving
out the card just to help the poor and needy though it is illegal but it
is something nice and he is not like other scam pretending
to have the blank ATM cards. And no one gets caught when
using the card. get yours from Georg Bednorz Hackers today! Just send an email
to georgbednorzhackers@gmail.com
Good Day Sir/Madam: Do you need an urgent loan to finance your business or in any purpose? We are certified,legitimate and international licensed Loan Factory we offer loans to Business firms.interest rate of 1%.
ReplyDeleteAvailable loans we offer are,
1. Personal Loan
2. Business Loan
3. Investement Loan
- Complete Name:
- Loan amount needed:
- Loan Duration:
- Purpose of loan:
- City / Country:
- Telephone:
Contact us today via:
bdsfn.com@gmail.com
anatiliatextileltd@gmail.com
Get your instant loan approval
Good Day Sir/Madam: Do you need an urgent loan to finance your business or in any purpose? We are certified,legitimate and international licensed Loan Factory we offer loans to Business firms.interest rate of 1%.
- Complete Name:
- Loan amount needed:
- Loan Duration:
- Purpose of loan:
- City / Country:
- Telephone:
- How Did You Hear About Us:
Have You Applied Before?...
With Best Regards.
Mrs. Magaret Becklas
Emaill: anatiliatextileltd@gmail.com
Emaill: bdsfn.com@gmail.com
Good Day Sir/Madam: Do you need an urgent loan to finance your business or in any purpose? We are certified,legitimate and international licensed Loan Factory we offer loans to Business firms.interest rate of 1%.
Available loans we offer are,
1. Personal Loan
2. Business Loan
3. Investement Loan
- Complete Name:
- Loan amount needed:
- Loan Duration:
- Purpose of loan:
- City / Country:
- Telephone:
Contact us today via:
bdsfn.com@gmail.com
anatiliatextileltd@gmail.com
Get your instant loan approval
Good Day Sir/Madam: Do you need an urgent loan to finance your business or in any purpose? We are certified,legitimate and international licensed Loan Factory we offer loans to Business firms.interest rate of 1%.
- Complete Name:
- Loan amount needed:
- Loan Duration:
- Purpose of loan:
- City / Country:
- Telephone:
- How Did You Hear About Us:
Have You Applied Before?...
With Best Regards.
Mrs. Magaret Becklas
Emaill: anatiliatextileltd@gmail.com
Emaill: bdsfn.com@gmail.com
Hello All
ReplyDeleteI'm offering following hacking services
..hacking Tools
..Spamming Tools
..Scam pages
..spam tools scanners make your own tools
..Keyloggers+fud+xploits
Other hacking svs
..Western union Trf
..wire bank trf
..credit / debit cards
..email hacking /tracing
..Mobile hacking / mobile spam
fully proof work
Availability 24/7 only given below addresses
Contact info
salvrosti@gmail.com
salvrosti@yahoo.com
Icq: 718684828
Skype: live:Salvrosti
There is no pleasure in being poor, you have to be competittive change
ReplyDeleteyour financial status now with the help of the Blank ATM Card that has no
trace or risk, it will give your life a meaning,withdraw up to $2500 daily,so
you can be able to pay your bills with no need for a loan and provide for
your family. This Blank ATM card is a programmed card that has the ability
to break into any ATM machine in the world and rendering all CCTV useless
when making withdrawal contact a reliable and dependable COMPANY
today via email:
davidbenjaminltd@outlook.com
I have been so poor and sick before, but now i am rich and healthy
ReplyDeleteI got a master card from my spanish friend on the internet and this card is loaded with money
with this card i am able to collect 3000$ per day, i collected my card last week and
my friend still have many of this card to give out,
if you are poor and you need help you can get this card
To get this card contact tarjetaservicio@gmail.com and you will have your card.
contact: tarjetaservicio@gmail.com
thanks
f you need to hack into any database, delete records, improve credit score,website, email, mobile phone (call, text message, Whatsapp, bbm), social network (fbk, twitter, Instagram) change your grades, find your target password (friends, wife, husband, boss, girl, boy friends) to know if they are cheating or not. ( he saved my relationship Tell him Linda ) Very cheap and Fast
ReplyDeleteContact Jerry
Email ; ( jerrydhacker2000@gmail.com )
Let's look at this question...
ReplyDeleteIs $2,000 too much for the hacker you hired who successfully helped you clear evidence from your blackmailer database?
This is basic business. If he did the job then he should get the agreed upon fee.
I want you to think about something as well:
If he pulled off a job like that, do you think it is wise to not hold up your end of the agreement? I am assuming that since you hired him to wipe part of a database for you, that his actions were illegal and your hiring him was illegal. you think that he will not take illegal actions to get his agreed upon fee?
To answer your question: $2000USD seems pretty standard. It would take a few hours to fuzz the system and find a way in. Then the hacker would have to edit the database which is probably in SQL. So we are probably talking about a skilled pen tester and also someone with decent SQL knowledge. That is worth some money on the open market. To get away with this job, your hacker probably is fairly skilled at masking his online identity. So lets say that he gets a value of about $100 per hour and took 5 hours to perpetrate the hack. That would be about $500 at face value. But then you have to factor in that the hacker is breaking the law for you, so expect a hefty premium just for that. That on its own is enough to justify a 2k payday assuming the hacker was legit and did what you wanted.
A better way to look at it is this: If you hadn’t hired the hacker, how much would you have lost to the blackmailer?
So, if you need a legit hacker, to get your work done, contact
Contracthacks@gmail.com. cheers
ReplyDeleteThis is is a dream come true !!! I have being hearing about this blank ATM card for a while and i never really paid any interest to it because of my doubts. Until now i discovered a hacking lady called williams . he is really good at what she is doing and he is Godsent, Back to the point, I inquired about The Blank ATM Card from her If it works or even Exist. she told me Yes and that its a card programmed for random money withdraws without being noticed and can also be used for free online purchases of any kind. This was shocking and i still had my doubts. Then i gave it a try and asked for the card and agreed to their terms and conditions. praying and hoping it was not a scam i used the blank CARD and it was successful i withdraw nothing less than 8,000 dollar daily the blank CARD worked like a magic and now i have am rich and famous in my society,im grateful to williams because she changed my story all of a sudden,The card works in all countries except Philippines, Mali and Nigeria. williams email address is williamshackers@hotmail.com...
Good day to all viewer online..Hacker Atm card is right here and get rich immediately and take money directly from any ATM Machine Vault with the use of our ATM Programmed Card which runs in automatic mode.This is an opportunity you all have been waiting for. Get the new programmed ATM BLANK CARD that can hack any ATM MACHINE and withdraw money from any where in the world. it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mr Dickson because i met two people before me and they took my money not knowing that they were scams. But am happy now.Mr Dickson sent the card through DHL and i got it in 24hours. Get your own card from Mr Dickson now he is not like other scammer pretending to have the ATM card,Mr Dickson is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Mr Dickson because he changed my story all of a sudden . The card works in all countries except,or his email: dicksonblankatmhacker@gmail.com
ReplyDeleteHello everyone, my name is Kate and I want to recommend a reliable hacker who helped hack my husband's cell phone remotely.
ReplyDeleteWhich gave me full access to all his texts and, and now he has nothing to hide from me. If you require his service, contact ghosthacker2351@gmail.com, tell him Kate referred you he'll help.
Do you need Personal Loan?
ReplyDeleteBusiness Cash Loan?
Unsecured Loan
Fast and Simple Loan?
Quick Application Process?
Approvals within 24-72 Hours?
No Hidden Fees Loan?
Funding in less than 1 Week?
Get unsecured working capital?
Contact Us At :mrhamdnloanoffer@gmail.com
LOAN SERVICES AVAILABLE INCLUDE:
================================
*Commercial Loans.
*Personal Loans.
*Business Loans.
*Investments Loans.
*Development Loans.
*Acquisition Loans .
*Construction loans.
*Business Loans And many More:
Contact Us At :mrhamdnloanoffer@gmail.com
Hello All
ReplyDeleteI'm offering following hacking services
..Western union Trf
..wire bank trf
..credit / debit cards
..Perfect Money / Bintcoing adders
..email hacking /tracing
..Mobile hacking / mobile spam
..hacking Tools
..Spamming Tools
..Scam pages
..spam tools scanners make your own tools
..Keyloggers+fud+xploits
Fake peoples have just words to scam peoples
they just cover their self that they are hacker
but when you ask them a questions they don't have answer
they don't have even knowledge what is hacking
am dealing with real peoples who interested and honest
also teaching hacking subjects in reasonable price
with private tools and proof.
Availability 24/7 contact only given below addresses
salvrosti@gmail.com
Icq: 718684828
Skype: live:Salvrosti
ReplyDeleteBasically think we all don’t have to face all these deceit and lies from our spouse…
in a case of mine when i got sick and tired of all the lies and deceit i had to contact a friend of mine to get me the
Contact of one of the best hackers in the states.
just contact him on cyberprofessionalhacker@gmail.com he is 100%
PLEASE READ!!!! Hello Guys,This is a Life Time transformation !!!Am so happy I got mine from Elizabeth. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $8,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Elizabeth because i met two people before her and they took my money not knowing that they were scams. But am happy now. Elizabeth sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Elizabeth because she changed my story all of a sudden . The card works in all countries except Philippines, Mali and Nigeria. Elizabeth's email address is elizabethcole232@yahoo.com
ReplyDeletePLEASE READ!!!! Hello Guys,This is a Life Time transformation !!!Am so happy I got mine from Elizabeth. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $8,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Elizabeth because i met two people before her and they took my money not knowing that they were scams. But am happy now. Elizabeth sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. im grateful to Elizabeth because she changed my story all of a sudden . The card works in all countries except Philippines, Mali and Nigeria. Elizabeth's email address is elizabethcole232@yahoo.com
ReplyDeleteHEY GUYS,CONTACT GHOSTHACKER2351@GMAIL.COM FOR ALL KINDS OF HACK(CELLPHONE HACK,CHANGE OF GRADE,BOOST YOUR CREDIT SCORE)IF INTERESTED TELL HIM I REFERRED YOU.
ReplyDelete"Cybershieldnotch" a large orgnisation of solution technologists..!! We Render help to strictly talented computer gurus that finds it hard to make good living with obviously what they good at "HACKING"..we have worked and still in conjunction with DARK WEBBERS,AGENT GURUS, CHECKHATTERS,SONY PLAYSTATION,GMASS COPERATIONS,CYBER WORLD and TECH CRAFTS Etc..for years now, We've helped keeping situations in check with these organisations listed above and so many sites, Bank Accounts, school upgrades also clear criminal records of all sort and in short timing hacked petty cyber sites accounts like Skpe, Fb, Whatsapp, Tinder, Twitter but these are significant experience a good and effectively recognized organisation must firmly ascertain and minorly our "AIM" here.
ReplyDelete1: The aim is to render proficient solution to those having cyber issues and technically needs a hacker to get their job done effectively fast...!!
2: to recruit real hackers (gurus only) in need of job with or without a degree..!!
So if you ever need a job done or interested in joining the organization (an online binanry exam will be set for those in need of these job) you can write us on
Cybershieldnotch@protonmail.com
Thank you!!!
Tried a lot of hackers but i strongly recommend cyberapphack@gmail.com.These are ethical hackers that’ll solve all your problems like hack emails,Facebook, Twitter ,Instagram , change grades ,erase criminal records, credit and debit top up, insurance paper, access or recover lost files, background checks on individuals and organizations or monitor cheating spouses’ phone or social media activities, contact at CYBERAPPHACK@GMAIL.COM.
ReplyDeleteHello Everyone ,I have been living with my wife for some years now,she has been keeping late nights and also receiving calls late at night,i was afraid she has been cheating on me and a friend of mine introduced me to a private investigator who helped me and gave me the password to her Facebook and Gmail account and also linked all her phone conversations to me.He saved me from all her lies and infidelity,he gave me all i wanted during our divorce and helped me with evidence in court.Contact (ethicalhacking618@ gmail .com) .tell him i referred you he will help you
ReplyDeleteMany WANT TO BE ONLINE HACKERS BEWARE OF THEM, IF YOU NEED GENUINE AND PROFESSIONAL HACKERS SERVICES, CONTACT SOLUTIONHACKERS95@GMAIL.COM
ReplyDeleteThey are a professional hacking group based in U S A, TURKEY, INDIAN AND EUROPE, They are the best hackers and also software developers to penetrate all websites, all other hackers contact them for the best Algorithm Software. Their services are 100% guaranteed too, with their penetration software unreachable. They offer the following services;
- illegal card hacking
-Removal of the old credit score
-University of change of notes
-Bank accounts hack
-Procedures of crime
-Facebook hack
-Tweitters hack
- personal mail accounts
-Grade Changes hack
- Policy blocked on site
-server crashed hack
-Skype hack
-Dates hack
-Word Press Blogs hack
- Individual Computers
-Control devices remotely
-Burner Numbers hack
- Verified Paypal accounts pirate
- Any social network account you make
-Auto and iPhone Hack
Text message intercept text
- Trapping in the mail
- credit card for free online transactions
Credit Card and Credit Card Blank Atm
-Intraceable Ip etc.
Contact SOLUTIONHACKERS95@GMAIL.COM
NOTE they are the solution to all your hacking problem
Many WANT TO BE ONLINE HACKERS BEWARE OF THEM, IF YOU NEED GENUINE AND PROFESSIONAL HACKERS SERVICES, CONTACT SOLUTIONHACKERS95@GMAIL.COM
ReplyDeleteThey are a professional hacking group based in U S A, TURKEY, INDIAN AND EUROPE, They are the best hackers and also software developers to penetrate all websites, all other hackers contact them for the best Algorithm Software. Their services are 100% guaranteed too, with their penetration software unreachable. They offer the following services;
- illegal card hacking
-Removal of the old credit score
-University of change of notes
-Bank accounts hack
-Procedures of crime
-Facebook hack
-Tweitters hack
- personal mail accounts
-Grade Changes hack
- Policy blocked on site
-server crashed hack
-Skype hack
-Dates hack
-Word Press Blogs hack
- Individual Computers
-Control devices remotely
-Burner Numbers hack
- Verified Paypal accounts pirate
- Any social network account you make
-Auto and iPhone Hack
Text message intercept text
- Trapping in the mail
- credit card for free online transactions
Credit Card and Credit Card Blank Atm
-Intraceable Ip etc.
Contact SOLUTIONHACKERS95@GMAIL.COM
NOTE they are the solution to all your hacking problem
INSTEAD OF GETTING A LOAN, CHECK OUT THE BLANK ATM CARD IN LESS THAN 24hours {blankatmhaker@gmail.com}
ReplyDeleteAm Mark Oscar,I want to testify about Jack Robert blank ATM cards which can withdraw money from any ATM machines around the world. I was very poor before and have no hope then I saw so many testimony about how Jack Robert send them the ATM blank card and use it to collect money in any ATM machine and become rich. I also email him and he sent me the blank card. I have use it to get 70,000 dollars. withdraw the maximum of $5,000 daily. Jack Robert is giving out the card just to help the poor. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email Him on how to get it now via: blankatmhaker@gmail.com or call/Text on +1(406) 350-4986
INSTEAD OF GETTING A LOAN,, I GOT SOMETHING NEW
ReplyDeleteGet $5,500 USD every day, for six months!
See how it works
Do you know you can hack into any ATM machine with a hacked Atm card??
Make up you mind before applying, straight deal...
Order for a blank Atm card now and get millions within a week!: contact us
via email address:: ( illuminatinetweb@gmail.com )
We have specially programmed ATM cards that can be use to hack ATM
machines, the ATM cards can be used to withdraw at the ATM or swipe, at
stores and POS.
you order for::
Here is our price lists for the ATM CARDS:
Cards that withdraw $5,500 per day costs $200 USD
Cards that withdraw $10,000 per day costs $355 USD
Cards that withdraw $35,000 per day costs $550 USD
Cards that withdraw $50,000 per day costs $3670 USD
make up your mind before applying, straight deal!!!
The price include shipping fees and charges , order now: contact us via
email address::( illuminatinetweb@gmail.com )
CONTACT US TODAY TO GET YOUR CARD AND ENJOY FREE CASH!!!
( illuminatinetweb@gmail.com )
I GOT MY PROGRAMMED BLANK ATM CARD TO WITHDRAW A MAXIMUM OF $5000 DAILY.
ReplyDeleteI AM SO EXCITED BECAUSE I ORDERED AND PAID FOR DELIVERY, DIDN'T GET SCAMMED, AND I NOW OWN MY HOME,
MY BUSINESS HAS GROWN BIGGER.
GEORG BEDNORZ (georgbednorzhackers@gmail.com) IS THE NAME OF THIS USA HACKER THAT GAVE ME THE CARD AND MADE MY
FAMILY MORE HAPPIER THAN EVER.
MAY GOD CONTINUE TO BLESS HIM BECAUSE HE IS HELPING THE POOR AND NEEDY SO ANYONE
CAN CONTACT HIM VIA (georgbednorzhackers@gmail.com)
I cannot over emphasize the professionalism of CYBERPROFESSIONALHACKER@GMAIL.COM I have spent several hours monitoring my husband
ReplyDeleteand his co-worker flirting literally and there has not been any technical malfunctions. I have been able to monitor
all his communications with his girlfriend and I can see clearly that he has alot of them, he must be a devil, because
I dont understand how he still comes home to tell me he loves me.. I have never been this dissapointed and sad in my
life before. I really want to thank my stars I took courage to contact him and for all his tender kindness towards
assisting me and giving me exactly what I requested for in the hack. You can also take a
bold step t contact him and findout about your cheating spouse: CYBERPROFESSIONALHACKER@GMAIL.COM
ReplyDeleteHello !
Do you Need legitimate and quick loan service?
Apply now and get your money urgently!
* Position between 5000 to 50 million
* Choose between 1 to 30 years to repay.
* Flexible loan terms.
Reply Back To Us With The Following: Email: (thompson.loanservice@gmail.com)
All these and more, please contact us.
Full name: ..........
Telephone number:.......
Monthly income: .............
Country ...............................
Loan Purpose ...........
The amount needed .................
Loan Status............
Duration: ...........................
Contact us by email: thompson.loanservice@gmail.com
Management.
Contact the credit Speedy now !!!
BEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE..... Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) for how to get it and its cost . .......... EXPLANATION OF HOW THESE CARD WORKS.......... You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $1,000, 2nd VAULT $5,000, RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly... Done. ***NOTE: DON'T EVER MAKE THE MISTAKE OF CLICKING THE "ALL" OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com). We are located in USA
ReplyDeleteHello everyone, Do you need hacking services? TESTED AND TRUSTED WITHIN 2 HOUR .. please contact SOLUTIONHACKERS95@GMAIL.COM
ReplyDeleteBe warned, most of these hackers called here are imposters, I know how real hackers work, they never advertise in such a gullible way and they are always discreet. I was tricked so many times out of desperation trying to find urgent help to change my grades from school, finally my friend introduced me to a group of trusted hackers who work with discretion and delivery promptly, they do all sorts of hacking that vary;
- Sales of ATM cards in white.
- Changes in university or school
- Confidence in bank accounts and transfer of funds
- Delete criminal records hack
- Facebook hack, Twitters hack
- email accounts hack, gmail, yahoomail, hotmail etc.
- Skype hack
- Databases pirate
- Word Press Blogs hack
- Individual Computers
- Remote control devices
- Verified accounts of the Paypal hack
- Android and iPhone Hack etc.
But they helped me;
- Changed my school grades
- Hacked my girlfriend boyfriend
- Most of it, they helped me with the money transfer Western Union and I accompanied and confirmed the money. I've made them my permanent hackers and you too can enjoy their services.
You can contact them at: SOLUTIONHACKERS95@GMAIL.COM for any hacking service and also strive to spread the good news about how they have helped you to merit publicity.
Hello everyone, Do you need hacking services? TESTED AND TRUSTED WITHIN 2 HOUR .. please contact SOLUTIONHACKERS95@GMAIL.COM
ReplyDeleteBe warned, most of these hackers called here are imposters, I know how real hackers work, they never advertise in such a gullible way and they are always discreet. I was tricked so many times out of desperation trying to find urgent help to change my grades from school, finally my friend introduced me to a group of trusted hackers who work with discretion and delivery promptly, they do all sorts of hacking that vary;
- Sales of ATM cards in white.
- Changes in university or school
- Confidence in bank accounts and transfer of funds
- Delete criminal records hack
- Facebook hack, Twitters hack
- email accounts hack, gmail, yahoomail, hotmail etc.
- Skype hack
- Databases pirate
- Word Press Blogs hack
- Individual Computers
- Remote control devices
- Verified accounts of the Paypal hack
- Android and iPhone Hack etc.
But they helped me;
- Changed my school grades
- Hacked my girlfriend boyfriend
- Most of it, they helped me with the money transfer Western Union and I accompanied and confirmed the money. I've made them my permanent hackers and you too can enjoy their services.
You can contact them at: SOLUTIONHACKERS95@GMAIL.COM for any hacking service and also strive to spread the good news about how they have helped you to merit publicity..,.
◾PROTOCOLHACKS/SHIELDERS◾
ReplyDeleteI am COREY RODRIGUEZ by name, CEO of protocol & shield hack Team..
we give guidelines to all of our clients as advisors to them, you don't get ripped off by fake hackers...
POSSIBILITIES OF CLEARING CREDIT HISTORY:
A hacker cant change or clear your credit score history,
but moderate it.
Thus rare in most cases!!
There are three credit bureaus and literally dozens of different scores,
That carries 3 max trojan w#asβ security guide!.
not to mention security procedures.
Honestly you might need close to 2800usd to get each tools of the security guards to get it cleared perfectly in a week without any defect later On.
But in cases of credit moderations?
The hacker can help moderate by reduction of bad performances
Your Credit Information Report (CIR) plays a large part in the loan application process and hence a lower score can impact your chances for a loan approval anywhere.
If you intend this moderation package, it will only cost a couple of tool, that sound nice right??
we also, suggest working on improving your credit as another option, which is possible, rather than going for hackers or other gimmick solutions.
If you intend MODERATION, it will cost you like I've said..
Think of it.. And let us know if you need a hire for this,
We deal with forms of cyber attacks!
◾Protocolhacks@gmail.com
◾Cybershieldnotch@gmail.com
◾Cybershieldnotch@protonmail.com..
Endeavour to write us..!
I sincerely didn’t like the idea, but this is my way of saying thank you to the Quora user that recommended a hacker (ETHICALHACKERS009@GMAIL.COM)
ReplyDeleteI hired him for a very private and difficult matter of helping me hack a my spouse’s phone and social networks and some other personal stuffs and he far exceeded my expectations. which Jeremie, helped me get the info(whatsapp, facebook, text messages, call logs etc) faster and cheaper than I had imagined. The first time we spoke, we had a very long phone consultation in he gave me all my options that he could think of to resolve my case, and he even recommended I try other options before hiring him, which shows that he is honest. I decided to hire him and I am glad I did. he is a fantastic investigator and a great person. If you need a professional, reliable and efficient hacker, then you should contact this guy ; ETHICALHACKERS009@GMAIL.COM
You can also call him or send him a text +16692252253
Hello Everybody,
ReplyDeleteMy name is Mrs Sharon Sim. I live in Singapore and i am a happy woman today? and i told my self that any lender that rescue my family from our poor situation, i will refer any person that is looking for loan to him, he gave me happiness to me and my family, i was in need of a loan of S$250,000.00 to start my life all over as i am a single mother with 3 kids I met this honest and GOD fearing man loan lender that help me with a loan of S$250,000.00 SG. Dollar, he is a GOD fearing man, if you are in need of loan and you will pay back the loan please contact him tell him that is Mrs Sharon, that refer you to him. contact Dr Purva Pius,via email:(urgentloan22@gmail.com) Thank you.
My Brothers and Sister all over the world, I am Mrs Boo Wheat from Canada ; i was in need of loan some month ago. i needed a loan to open my restaurant and bar, when one of my long time business partner introduce me to this good and trustful loan lender DR PURVA PIUS that help me out with a loan, and is interest rate is very low , thank God today. I am now a successful business woman, and I became useful. In the life of others, I now hold a restaurant and bar. And about 30 workers, thank GOD for my life I am leaving well today a happy father with three kids, thanks to you DR PURVA PIUS Now I can take care of my lovely family, i can now pay my bill. I am now the bread winner of my family. If you are look for a trustful and reliable loan leader. You can Email him via,mail (urgentloan22@gmail.com) Please tell him Mrs Boo Wheat from Canada introduce you to him. THANKS
ReplyDeleteGet the best 2018 celebration ever with our Blank ATM card and be a Millionaire, Cool way to have financial freedom!!! Are you tired of living a poor life, here is the opportunity you have been waiting for, We give out a Blank ATM Card. Do you want to live a good life thought its illegal, its the easiest way to be a millionaire. Get your card today and live that luxury life you always dream to live and to get this card, contact us via email:(Atmcardcashmachine@gmail.com) TO GET YOURS NOW
ReplyDeleteHello Everybody,
ReplyDeleteMy name is Mrs Sharon Sim. I live in Singapore and i am a happy woman today? and i told my self that any lender that rescue my family from our poor situation, i will refer any person that is looking for loan to him, he gave me happiness to me and my family, i was in need of a loan of S$250,000.00 to start my life all over as i am a single mother with 3 kids I met this honest and GOD fearing man loan lender that help me with a loan of S$250,000.00 SG. Dollar, he is a GOD fearing man, if you are in need of loan and you will pay back the loan please contact him tell him that is Mrs Sharon, that refer you to him. contact Dr Purva Pius,via email:(urgentloan22@gmail.com) Thank you.
Do not use all of these Private Money Lender here.They are located in Nigeria, Ghana Turkey, France and Israel.My name is Mrs.Ramirez Cecilia, I am from Philippines. Have you been looking for a loan?Do you need an urgent personal or business loan?contact Fast Legitimate Loan Approval he help me with a loan of $78.000 some days ago after been scammed of $19,000 from a woman claiming to be a loan lender from Nigeria but i thank God today that i got my loan worth $78.000.Feel free to contact the company for a genuine financial Email:(urgentloan22@gmail.com)
ReplyDeleteDo you need Personal Loan?
ReplyDeleteBusiness Cash Loan?
Unsecured Loan
Fast and Simple Loan?
Quick Application Process?
Approvals within 24-72 Hours?
No Hidden Fees Loan?
Funding in less than 1 Week?
Get unsecured working capital?
Email us:urgentloan22@gmail.com
Application Form:
=================
Full Name:................
Loan Amount Needed:.
Purpose of loan:.......
Loan Duration:..
Gender:.............
Marital status:....
Location:..........
Home Address:..
City:............
Country:......
Phone:..........
Mobile / Cell:....
Occupation:......
Monthly Income:....
Email us (urgentloan22@gmail.com)
GENUINE LOAN WITH LOW INTEREST RATE APPLY
ReplyDeleteDo you need finance to start up your own business or expand your business, Do you need funds to pay off your debt? We give out loan to interested individuals and company's who are seeking loan with good faith. Are you seriously in need of an urgent loan contact us.Email: (urgentloan22@gmail.com)
BORROWERS DATA FORM
1)YOUR NAME:_______________
2)YOUR COUNTRY:____________
3)YOUR OCCUPATION:_________
4)YOUR MARITAL STATUS:_____
5)PHONE NUMBER:____________
6)MONTHLY INCOME:__________
7)ADDRESS:_________________
8)PURPOSE:_________________
9)LOAN REQUEST:____________
10)LOAN DURATION:__________
11)CITY/ZIP CODE:__________
12)HAVE YOU APPLIED FOR LOAN BEFORE?
E-mail: (urgentloan22@gmail.com)
Do not use all of these Private Money Lender here.They are located in Nigeria, Ghana Turkey, France and Israel.My name is Mrs.Ramirez Cecilia, I am from Philippines. Have you been looking for a loan?Do you need an urgent personal or business loan?contact Fast Legitimate Loan Approval he help me with a loan of $78.000 some days ago after been scammed of $19,000 from a woman claiming to be a loan lender from Nigeria but i thank God today that i got my loan worth $78.000.Feel free to contact the company for a genuine financial Email:(urgentloan22@gmail.com)
ReplyDeleteHello everyone, this message is only for people that live in united state if you are interested in credit card top up email us via: jameshacker157@gmail.com we only need people that are very faithful and you will also gain from this alot.
ReplyDeleteI GOT MY PROGRAMMED BLANK ATM CARD TO WITHDRAW A MAXIMUM OF $5000 DAILY.
ReplyDeleteI AM SO EXCITED BECAUSE I ORDERED AND PAID FOR DELIVERY, DIDN'T GET SCAMMED, AND I NOW OWN MY HOME,
MY BUSINESS HAS GROWN BIGGER.
GEORG BEDNORZ (georgbednorzhackers@gmail.com) IS THE NAME OF THIS USA HACKER THAT GAVE ME THE CARD
AND ALSO HE IS OFFERING ALL KINDS OF LOAN WITH ONLY 2% INTEREST RATE.
I sincerely didn’t like the idea, but this is my way of saying thank you to the Quora user that recommended a hacker (ETHICALHACKERS009@GMAIL.COM)
ReplyDeleteI hired him for a very private and difficult matter of helping me hack a my spouse’s phone and social networks and some other personal stuffs and he far exceeded my expectations. which Jeremie, helped me get the info(whatsapp, facebook, text messages, call logs etc) faster and cheaper than I had imagined. The first time we spoke, we had a very long phone consultation in he gave me all my options that he could think of to resolve my case, and he even recommended I try other options before hiring him, which shows that he is honest. I decided to hire him and I am glad I did. he is a fantastic investigator and a great person. If you need a professional, reliable and efficient hacker, then you should contact this guy ; ETHICALHACKERS009@GMAIL.COM
Y ou can also call him or send him a text +16692252253
Hello Everybody,
ReplyDeleteMy name is Mrs Sharon Sim. I live in Singapore and i am a happy woman today? and i told my self that any lender that rescue my family from our poor situation, i will refer any person that is looking for loan to him, he gave me happiness to me and my family, i was in need of a loan of S$250,000.00 to start my life all over as i am a single mother with 3 kids I met this honest and GOD fearing man loan lender that help me with a loan of S$250,000.00 SG. Dollar, he is a GOD fearing man, if you are in need of loan and you will pay back the loan please contact him tell him that is Mrs Sharon, that refer you to him. contact Dr Purva Pius,via email:(urgentloan22@gmail.com) Thank you.
hello everyone, my name is Rebecca Monique, a kind Hearted widow with no kids. and i want to use this medium as an opportunity to advice all loan seekers to kindly reach out to FRANK LEXIE FINANCE LOAN FIRM, a private loan lending organization that you can trust, they base their efforts in empowering the general public financially in all areas, their services are fast, clear, sharp and comprehensive, and they grant business loans, personal loans, as well as auto loans. with an interest rate as low as 3% I never had a loan online successfully before, I was denied even by my own bank and other banks too because my credit score was low, i also got scammed of $780 by a fake online lender who promised to grant me the loan as soon as i paid a non collateral fee of $780, and i did, only to realize that he was just a scam from Cameroon, and a lieing bastard, who just ended up putting me in more debt!! i was really worried and confused, because i had to clear my debts, fund my project, and also set up something Little, few days later, i came across a post of someone on the nerd-wallet reviews site, testifying about how he successfully got a personal loan of $50,000 from Mr Frank Lexie Loan Firm, it drew my attention because he said that there are no credit checks and that the loans are approved and granted within 24 hours, so i decided to give it a shot,. I recently acquired a business loan of $150,000.00 which was fully transferred to my bank account about 20 hours after approval and cost of transfer was resolved. i was so surprised and happy, now i have paid off all my debts and my new business is going fine! sometimes all we need is to find the right persons, locate the right ones and everything goes perfect!!! If you are seriously in need of any kind of loan I fully advice you to contact this firm now via email ( lexiefinance@yahoo.co.uk ). And be rest assured of a getting your loan funds fully granted to you.
ReplyDelete
ReplyDeleteMy life was falling apart, I was being cheated and abused, I had to know the truth and needed proof. i saw a
recommendation about a private investigator cyberprofessionalhacker@gmail.com by a friend. i contacted them and they
took care of my needs. they hacked his iphone and gave me all information in his facebook,instagram, Whatsapp,
twitter and email account. I got all I wanted as proof .
I am glad i had a proven truth he was cheating.Contact them if you need help.
I got my already programmed and blank ATM card to
ReplyDeletewithdraw the maximum of $50,000 MONTHLY for a maximum of 12 MONTHS. I am so happy about this because i got mine last week
and I have used it to get $150,000 already. (georgbednorzhackers@gmail.com) is giving
out the card just to help the poor and needy though it is illegal but it
is something nice and he is not like other scam pretending
to have the blank ATM cards. And no one gets caught when
using the card. get yours from Georg Bednorz Hackers today! Just send an email
to (georgbednorzhackers@gmail.com)
ATM CARD THAT CAN CHANGE YOUR LIFE TODAY
ReplyDeleteCREDIBLE ATM HACKERS decided to develop a way to make easy money. Though its illegal, but still one can easily survive with it HACK ATM MACHINES AND MAKE NOTHING LESS THAN $20,000 EVERYDAY We have been able to develop this programmed ATM cards, that are capable of hacking into any ATM machine . It has been tested and its trusted.It works any where in the world. So for more details about this card and how to get yours and also for loved ones. Kindly contact the hackers via email:
cliffordhackerspays@gmail.com....
Hello,
ReplyDeletewelcome to technechhacks where problems are been solved,
We deal with the total functioning of sites like Facebook, twitter, Instagram, Snapchat, bank account, icloud, criminal records, school grades, Credit cards, spouses phones etc.
Thus Beware of scammers because most persons are been scammed and they end up getting all solutions to their cyber bullies and attacks by US.
I am Jason Williams one of the leading hack agents.
PURPOSE IS TO GET YOUR JOBS DONE AT EXACTLY NEEDED TIME REQUESTED!!
And our WORK SUCCESS IS 100%!!!
I'm always available for you when you need help.
Contact or write us on:
technechhacks@gmail.com
Thanks for your time.
A lot of people have no idea about a working blank ATM card and a lot of people have been scammed in search of the Blank ATM card. It is longer news that GEORG BEDNORZ HACKERS (email: georgbednorzhackers@gmail.com) is one of the few hacking groups that can provide you with a working Blank ATM card in anywhere around the globe. The programmed Blank ATM card can provide you with up to $5000 daily on any ATM without been caught. Those that require the Blank ATM card should look no further but contact now and get working Blank ATM card within a week
ReplyDelete(email: georgbednorzhackers@gmail.com)
Whatsapp: +12672776634
I remember my experience with hackers i contacted online, i almost lost hope in finding out if my husband was loyal to me and has been loyal in our 20 years marriage, i lost a lot of funds in paying these so called hackers so i made up my mind that if i get scammed again i'll just forget about finding out what God doesn't want me to know, Then i saw reviews about ( mikejosh@cyber-wizard.com ) and decided contact him and if and if i hear any stupid excuse won't contact anybody and just accept that God doesn't want me to then he proved to me that he isn't a cheat by working a sample job for me but to my greatest surprise he did the job and sent results to me fast, i was so happy but sad part was i divorced my husband, and i will drop an advise for people who wants any kind of hacking services stopped being scammed by people who impersonate being hackers, contact ( mikejosh@cyber-wizard.com ) for a fast and clean job. Thank me later.
ReplyDeleteI’m Dr Williams Curry, I want to say a Grateful thank you to Joe Engressia after different experience of fake hacker i have met,, a friend recommend him to me with faith i contact him and explain my self,on what’s happening in my marriage life, told me not to worry and gave me his word, i don’t know him never met him before but makes me feel comfortable with is word and experience, i caught my cheating wife red handed cheating with my best friend, who has always been in my house when am not around… i had to share this as am sure that most here are looking for the right hacker and have not seen yet,,, please try and contact Joe Engressia ( DIGITALDAWGPOUNDHACKERGROUP@GMAIL.COM ) on any service of help you need from him as hacker.. it a testimony you have the right to give yours too by helping others to know there is still high rate good hackers that are highly experienced, he responds on email,text messages and whatsapp…
ReplyDeleteName: Joe Engressia
Phone Number: +1(732) 639–1527..
Come on are you suspecting your Husband/Girlfriend/Boyfriend/Wife is cheating on you and why their are sudden changes behaviour towards you.
ReplyDeleteSMILE ! SMILE ! SMILE and relax yourselves and your mind, in world of Hacking this is what I do
*Facebook Hacking Tricks
* Database Hacking
* G-mail/AOL/Yahoomail/ Inbox Hacks
*Control Device Remotely Hack
*University Grade Hack
*Wiping of Credit Cards, Increase Credit Cards Hack
*Breaking Security Save Code Hack.
All you need do just E-mail:- pointekhack@gmail.com
In this cyber era everything is possible, no need to hire detectives to monitor your partner, no need to pay huge amount to lawyers and judges to reduce your sentence when you can just erase your criminal record either recent or past.
ReplyDeletewith Cybertron you can do all these and more at less expense.
Cybertron deal with
* Hacking(including all social media)
* Tracking
* Bank Jobs
* Flipping cash(credit cards)
* Taxes
* Criminal record or any form of
records
* Schools/Universities upgrade
* Military grade encryption, NASA
encryption and decryption.
You name it we do it all, we at your disposal 24/7
contact : infinitedataserver@gmail.com
ReplyDeleteBEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE..... Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) for how to get it and its cost . .......... EXPLANATION OF HOW THESE CARD WORKS.......... You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $5,000, 2nd VAULT $10,000, RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly... Done. ***NOTE: DON'T EVER MAKE THE MISTAKE OF CLICKING THE "ALL" OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com). We are located in USA.
I Lost my Money to scammers but not anymore
ReplyDeleteWell, who would have believed this. When I saw a comment
by one Allison babara, I thought it was one of the Scammers
ways to convince someone. Looking at his comment, I saw
an element of doubt since he was telling stories. Well I did it
50/50 which means I can’t lose my money to any scammer
again. I contacted the email on the testimony of Allison?
Babara (securehackers01@gmail.com) and I was
replied immediately. I was shocked but I didn’t lose my stand.
I asked them to give me proof to be sure they are not
scammers like others that I have met before and they sent me
a proof. Then I requested to get my card which they sent to
me in Germany in just 3 days. Am happy now because I have?
recovered my cash I lost to scammers. My first withdrawal?
was $10,000 and I couldn’t believe my eyes until I confirmed?
their word which says that I can withdraw up $63,000 in a
month. secureblankatmSolution? are real because I got my?
card in just 3 days when I requested for one. Contact their
mail (securehackers01@gmail.com ) for yours. They
didn’t scam me.
Morris mabel is my name and if you are scared, please reach
me through my mail dasinator02@gmail.com
I am very excited because i got my already programmed and blank ATM card to hack any ATM and withdraw money DAILY. A lot of people have no knowledge about the working Blank ATM card. a Cool way to have financial freedom.
ReplyDeleteGEORG BEDNORZ HACKERS (email: georgbednorzhackers@gmail.com) is one of the few hacking groups that can deliver a working Blank ATM card anywhere around the globe.
The programmed Blank ATM card can provide you with up to $5,000 daily on any ATM and no one gets caught when using the card.
DO YOU NEED A CARD? then you should look no further and contact now because you too can get the Blank ATM card and change your life
(email: georgbednorzhackers@gmail.com)
Whatsapp: +12672776634
I got my programmed and blanked ATM card to
ReplyDeletewithdraw the maximum of $5,000 daily for a maximum of 30
days via (wesleymarkhackers@gmail.com).
I am so happy about this because I have used it to get $150,000. Wesley mark Hackers is giving
out the card just to help the poor and needy though it is illegal but it
is something nice. He also give loans at 3%. get yours from Wesley Mark Hackers today! Just send an email
to (wesleymarkhackers@gmail.com),
or watsapp or call +16315383658
Thank you so much for sharing this great blog.Very inspiring and helpful too.Hope you continue to share more of your ideas.I will definitely love to read. best-wireless-access-points
ReplyDeleteHello! I am a citizen of US and have been living in Los Angeles I want to sincerely appreciate William who helped me with an already Programmed hacked ATM CARD and i was so poor without funds that i got frustrated. One morning as i was browsing the internet, i saw different comments of people testifying of how William helped them from being poor to rich through this already hacked ATM CARD. I was skeptical if this was true, i decided to contact one of the people giving this testimony to see proof before i contact this hacker, and they proved to me beyond all doubts that its was really for real so i urgently contacted the email: jameswellington114@gmail.com if you also want this BLANK ATM CARD i strongly advise you to contact this Hacker email: jameswellington114@gmail.com
ReplyDelete
ReplyDeleteI met this wonderful hacker that offers hacking services. Some of their services are: - Get any
password from any Email Address. - Get any password from any Face-book, Twitter
or Instagram account. - Cell phone hacking (whatsapp, viber, line, wechat,wire
wire transfer Western union/money gram etc) - Grades changes (institutes and
universities) Blank ATM - Websites hacking, pen-testing. - IP addresses and
people tracking. - Hacking courses and classes. their services are the best on
the market and 100% secure and discreet guaranteed. Just write them and ask for
your desired service: EMAIL ADDRESS: cyberhackingspecialist AT GMAIL DOT
COM or text +15165312529
As a divorced woman in my 50s, I had many things, fear and insecurity among them, as well as a limited knowledge of how credit worked since my husband always took care of our finances. The hacker FORD BLAZE took a chance on me, he helped remove all negative items on my credit report, collections including hard inquiries. My credit score went up drastically.
ReplyDeleteThank you FORDBLAZE for your keen eye and expert handling of what could have been a disastrous situation. You have proven your loyalty to me, now it's my turn to do the same for you. You all should contact via FORDBLAZE@MAIL.RU
Over the last several years my family and I have been hit hard: We had to file bankruptcy due to the housing market crash, move out of state, I had to change my career, and our daughter beat cancer at the age of 5.
ReplyDeleteIf it weren’t for the hacker WESTHIVE taking a chance on us and giving us a chance to start rebuilding our credit, then my family and I wouldn't have been able to rebuild ourselves and financially recover from all the challenges we have overcome. The hacker WESTHIVE has been understanding and supportive of our needs. Thank you. Contact him via WESTHIVE@MAIL.RU
I remember starting my credit journey and thinking it sounded like an easy concept as it was explained by my first bank: use what I needed, pay it back accordingly, and repeat. Then, like it does for most people, life showed just how unpredictable it could be. Everything from losing my job to not being able to afford my car payments, student loans to medical emergencies and even regular life stuff ran me ragged. I got to a point where I couldn't get any credit or loans or help. I couldn't believe how difficult banks or even local credit unions made it to build my credit back up.
ReplyDeleteI proposed to my girlfriend a year and a half ago and didn't know how we'd pay for a wedding, get our own place, and a few other things. About the same time, a friend recommended the hacker CYBORGUNLEASH to help and I got a chance at redemption. With help from the hacker, my credit score was increased within 10 days and now we are about to close on our first home. Thanks CYBORGUNLEASH. Contact him via CYBORGUNLEASH@MAIL.RU or call +16787866844
After multiple credit denials for even secured credit cards, the hacker CREDIT LORD took a chance on us and helped us in every way possible. . Through his help, we have been able to re-establish our profile and improve our scores by 300 points in the past week . We both now have scores of 750s and 762s respectively. We were able to recently secure a lease for a new car which would not have been possible if it wasn't for CREDIT LORD taking a chance. I would recommend his services to anyone looking to re-establish his/her credit. We hit rock bottom after our bankruptcy and didn't see any way out of the hole we had dug.
ReplyDeleteThank you for taking a chance on us. Thank you for giving us the opportunity to demonstrate the ability to be responsible again. The Hacker was going to be our last hope to get our credit fixed. If we hadn't been helped out of our situation I know we wouldn't have a safe, reliable vehicle for our 3 beautiful children. Thank you again for taking a chance. You can contact him via CREDITLORD@MAIL.RU
The Hacker CASPERDOVE helped me build my credit up, allowing for success in my financial future. He also allowed me to learn how to budget my money better and understand the importance of keeping a good credit score. I have received credit line increases and more credit card offers because I make sure that I pay my bill on time. I understand the value of having good credit and I am a very satisfied customer with the hacker CASPERDOVE.
ReplyDeleteI know that Credit Dove has allowed me to improve my credit score and helped set myself up for success in my future financial endeavors. You all should contact him via CASPERDOVE@MAIL.RU or call +15013869586
With the help of the hacker BRAINGURU, I was able to get my credit on track and, my debts were cleared and my Credit score upped by 250 points which was just enough for me to purchase a home. Some months later I and my wife bought a new car, lowering our monthly payments because we were finally offered good interest rates.
ReplyDeleteWorking with the Hacker BRAINGURU has helped me to see the value in taking the right steps, and seeing the fruit of my efforts by improving my family's life. Thank you BRAINGURU. Contact him via BRAINGURU@MAIL.RU
I am a single mom with six year-old triplets. When they were one year-old, I had to file for bankruptcy due to being out of work while they were in the NICU. I am a special education teacher and the triplets are now in first grade. The hacker TIGRESS BUZZ has helped me to rebuild my credit and helped me purchase things my triplets needed, from diapers to food to Christmas and birthday gifts! It's also helped me to build my credit up enough to buy us a vehicle that better fits our needs! Thank you once again to TIGRESS BUZZ. I highly recommend him for your credit fix. Contact him via TIGRESSBUZZ@MAIL.RU
ReplyDeleteMy family has always been the most important thing to me. I was married, owned a home and had four kids. I was living the American dream until, one day, it came crashing down. My husband and I got a divorce and although I tried to stay afloat, debt seemed to overtake everything. The house I worked so hard to keep was foreclosed on and I was suffocating in bills. I filed for bankruptcy as a last resort, but still worried about how I would rebuild my credit. I got in touch with CREDIT FIXER and within 7 days he got my credit fixed, removed bankruptcy, debts, collections and hard inquiries from my credit report with his ethical hacking skills.
ReplyDeleteI am now remarried. We are adopting my spouse’s nephew who has been with us since he was two days-old and my oldest son has started his first year of college. None of these major life changes have been easy or cheap, but having my credit rebuilt has helped make these changes possible for my family. Thanks to CREDIT FIXER , I believe the American Dream is possible and I am excited to see what the future holds. For your credit repairs I recommend you contact CREDITFIXER@MAIL.RU or call +15068008261
My name's Annabel and I'm a stay-home mom. My credit score is about 530- I have charged off several things on my report and been working at this for years, I literally have 30 pages of a credit report. No matter what I do to pay a bill of, it doesn't improve my score. I have never had a store card or any unsecured credit card. It's like a right of passage for teens(18 year olds, etc) to get a basic card and I'm sitting here at 32 and I can't even get anything. I've never even been able to get an apartment on my own & I feel like a failure. I had to open up to a close friend of mine who got touched with my predicament and eventually introduced me to a credit repair genius who helped her fix & maintain her current credit score. She encouraged me to contact him. I was quite optimistic and took a leap of faith by contacting him. He carefully explained the processes involved in getting my credit back on track and finally he increased my score from 530 to a whooping 780 & also removing the negative items on my report, all these done in week. I'm elated and appreciative of his efforts in giving me a better life, so here's me recommending him to you all out there with similar challenge like mine. Contact him on his personal mail: CYBERGENIUS@LIST.RU or Phone number: +1(512) 596-5268. Good-luck and feel free to thank me later.
ReplyDeleteHello Friends, this is a new month so avail yourselves of this opportunity: Improve your credit score by going for legitimate credit repair agency which will improve your credit score and expunge all your negative items permanently. One of the quickest and safest way is to hire a professional credit repair specialist who can effectively & economically re-establish your credit score and remove negative items. I was able to employ the services of (DIGITALMAESTRO@TECHIE.COM) who helped me increase my score & erase all bad items on my report permanently. To my amazement, he was able to remove damaging items like evictions & foreclosures from my report! Do not waste your time anymore with imposters who claim to be hackers when you can work with best without no hassles. He provides ethical, legitimate and affordable repair services. Right now I have an excellent score grade and all my debts have been wiped off. You can forward your request to the email address above or contact him via (865) 213-5456. Get on your way to strong credit again and I’m positive you will thank me later. Stay blessed!
ReplyDeleteI could not thank my friend enough for referring me here! EMPIRE HACK was a pleasure to interact with from day one. I went from great credit to near bankruptcy due to extremely unforeseen circumstances. I felt completely helpless. Erica Steeves accomplished more for me in few weeeks than I thought possible. I can honestly say they really went above and beyond to respond to my millions of concerns and make me feel that I was their number one priority EVERYTIME I called or emailed or just stopped by the office. This company not only gave me my confidence back with rebuilding my credit, I actually gained a friendship in Erica. I can literally count on her for any type of financial advice no matter how silly it may seem to her! I signed up in june this year and I still keep in contact with Erica because she really made me feel like family. With that experience I have referred my own family and friends to this company EMPIRE.HACK@INBOX.RU and they have all thanked me again and again.
ReplyDeleteMy name is Elizabeth and I was a very undisciplined spender. I would buy something with a credit card and tell myself I would pay that off before I would charge anything else. As you can probably guess, that didn't happen. I received help from a family member once before who paid off my debts for me so I could have a clean start. I was okay for a short time, but never learned a thing. I got one credit card. I convinced myself I would build up my credit with that one card by buying things and paying them off before I used it again. Needless to say, that didn't happen either. After five more cards, I started to feel that old dreadful trapped feeling I felt before.
ReplyDeleteI was embarrassed to ever want help again, but I was facing more interest than I could ever repay without years of payments. Five payments on credit cards plus interest is, by the way, is practically impossible. On top of that, I was planning on retiring in six years and needed to be out of debt to make it on social security and my retirement from my job.
That is when I went searching the Internet. I found several places that offered counseling and some loans. When I came across EMPIRE HACK, I looked into the background of the company, the Better Business Bureau, and past customers that were very happy with how this company helped them. I like that they go to your creditors for you and negotiate a lower interest rate, and/or, lower payment each month. You then pay EMPIRE HACK one week payment, which I have taken directly out of checking account.
I called them and found out from the very beginning, they were there to help and be supportive. Every person I have every spoken to at EMPIRE HACK has been kind, helpful, and knowledgeable. I can't say how much the employees impressed me. I was feeling embarrassed and they treated me like I was fixable. And I was.
Because you are paying your debts off, you cannot take out any credit for the period time it takes to be debt free. Meanwhile, I found out I can live on just what I make, while my debt is being paid down.. I wish I would have found this help a long time ago. I have paid extra when I have it so I am now just 1 months away from EMPIRE HACK making my last payment to my last creditor for me.
I am grateful to EMPIRE HACK for helping me to learn I can be in control of finances. I will be debt free soon and am not looking back. I know how good it feels and don't ever want that "out-of-control" feeling again. You can reach out to them on this EMPIRE.HACK@INBOX.RU OR +1 847-752-9580
I met a Trusted Certified Binary Options Recovery Expert through there happy again client's recovery reviews that they've recently helped to put smiles back on their faces after been cheated and scammed of their hard earned money . I invested with four binary companies and lost all of my investments totalling £720,000 Then I was contacted by someone offering help – a company who specializes in binary recovery. I was scammed by them again. By the end of it all I had lost all of my savings and I was in serious debt. I was desperate for help and that made me vulnerable to recovery scams. My husband is not around anymore and I have an 8 year old son with learning difficulties. The pressure of being a single, working mother with a child who needs so much additional attention and support became overwhelming for me. I also felt too traumatized to trust anyone else and I was very afraid, but I had no choice other than to trust Viapreferred@GMAIL.COM. He has been incredibly helpful and supportive and also very understanding about all of my fear and concerns he helped recover all of my funds back within a week using unethical means OR SKYPE contact - Parker joas . I really hope that others do not have to go through what I did, and I wish that I had realized before things were so bad that I was being scammed.
ReplyDeleteI highly recommend this organization. Within 5 working days of employing them to help with some derogatory items on my credit reports, they successfully disputed all 5 items (between the 3 main agencies) and were successful in having them removed! I am delighted with their results and attribute their success to their depth and expertise in an area where I had been unsuccessful on my own. I now have credit scores in the 700’s and am pleased to be back on track thanks to their assistance. you should contact EMPIRE.HACK@INBOX.RU OR
ReplyDelete+1 847-752-9580. if they can do mine, trust me they will do yours.
The truth is my family has always been the most important thing to me. I was married, owned a home and had four kids. I was living the American dream until, one day, it came crashing down. My Wife and I got a divorce and although I tried to stay afloat, debt seemed to overtake everything. The house I worked so hard to keep was foreclosed on and I was suffocating in bills. I filed for bankruptcy as a last resort, but still worried about how I would rebuild my credit. I got in touch with a CREDIT FIXER and within 4 days he got my credit fixed, removed bankruptcy, debts, collections and hard inquiries from my credit report with his ethical hacking skills.I am now remarried. We are adopting my spouse’s nephew who has been with us since he was two days-old and my oldest son has started his first year of college. None of these major life changes have been easy or cheap, but having my credit rebuilt has helped make these changes possible for my family. Thanks to REALWEB HACKER, I believe the American Dream is possible and I am excited to see what the future holds. For your credit repairs I recommend you contact REALWEB.HACKER@INBOX.RU or +1323-713-1043
ReplyDeleteMy wife and I, was in a terrible situation sometimes last year. We urgently needed to get a new house and my credit score and my wife own too was bad. We tried all we could to get a loan but all effort was in vain due to the bad credit score 574 and 590 . God so good to us, I later met with a credit score specialist and instructor, he gave me some instructions and requested some information from me regarding my credit score in which I provided everything to him. Luckily for me, this man was able to fix my credit score to 721 and 736 , I was so amazed. I’m happy to tell you that I’m writing this review from our new house which I wouldn’t have got without the specialist’s help. I know some people out there are in this kind of situation and I would love to help to put specialist’s contact here, You can message him privately on his mail which is CREDITCOMPANY@INBOX.RU , this help came at the time I already lost all hope.you can thank me later.
ReplyDeleteI have a story to tell. i and my WIFE needed credit repair, so we contacted this hacker, We explained to him about all the negative items on our report (around 25 negative items and 3 positive items) on my report with total debt was around $38,000. He stated to me: Yes! I can fix it in 5 days! i was excited! Now my wife’s credit had 15 negative items and 5 positive items. Her total debt was around $19,000. After analyzing both credit he stated we can correct both within 45 days! i was like WoW. its been 6 years the last time we had good credit. It was hard for me to believe. Well we got around to the cost of credit repair. When i asked he told me our price $3000 but i will receive a discount if both (H&W) start credit repair at the same time. i was like: that is a lot of money. he agreed. he asked me: How much total you and your wife need to pay off both of your debt? i calculated a total of $57,000 in debt (H&W) he said: Well, you can pay off the $57,000. or you can pay me $3000 to correct both credit reports within 45 days. After the 45 days had passed and he provided the finished jobs the least score was 782. Both my wife and i introduced him to our close colleagues and friends. He is very efficient and thorough type of person, asides from being an elite, if he works for you , you never have to worry about anything backfiring ….it is permanent, contact him (CYBERGURU@INBOX.RU). I am saying all this here cause i don’t think anyone deservers to miss the train, you want to end the bad credit?
ReplyDeleteI'm sure you here this all the time but i couldn't stop singing songs of praise to the staffs at the EASY.HACKER firm. I got an updated copy of my Experian Credit Report today and i was so happy i started jumping up and down in the driveway. They deleted six out of nine negative entries in less down 21days. Now that is what i call service. I can't wait to see the negative entries fall off my other reports as well. I urge everyone that read this testimony to contact them via email at EASY.HACKER@BK.RU or text +13237131043 and you will never believe what hit you as soon as all your negative bad debts is been cleared without stress or delay. Thanks in a million EASY.HACKER@BK.RU and God bless all your staffs for giving me the chance to stand up once again on my feet
ReplyDeleteAs a single mom, you have to be ready to run the extra miles for your kids. I promised TIGRESSBUZZ i was going to post a review about him if he could increase my credit score and hack my business competitor’s website. So i guess now i have no choice but to post a review. TIGRESS BUZZ is indeed an excellent hacker, my credit score has been increased to a golden score and my business competitor’s website is now in my control. Thank You So much . His Email address is TIGRESSBUZZ@MAIL.RU
ReplyDeleteI had two things on my credit that were holding me back. one is from sears which I paid off and I am not sure of the other one but they are both 17 years old. I filed bankruptcy 17 years ago and settled with them both. It was just brought to my attention that they are still on my reports I recently got referred by my best friend to contact JAVACOMPGEEK@MAIL.RU which I did and he helped me fix my credit and my score was improved I recommend him to anyone that needs to fix his or her credit.
ReplyDeleteI was thinking of applying for a bankruptcy form because i have no other options, I’m on a fixed income and cannot afford new things like auto loan, mortgage loan. My insurance premiums increased and interest rate has hindered me from getting some benefits and securing a job of my choice.,i came across a comment of a young man on a blog giving kudos for job well done to a hacker who assisted him in clearing off his debts and bad credit report, i took a risk by hiring him to Fix my credit score. I’m happy to tell you that this was fixed within 48hours by this exceptional hacker called CYBORGUNLEASH, i was impressed by his work and that’s the reason I’m recommending him as well. You can reach him through this email CYBORGUNLEASH@MAIL.RU
ReplyDeleteWe are authorized Financial consulting firm that work directly with
ReplyDeleteA rated banks eg Lloyds Bank,Barclays Bank,HSBC bank etc
We provide BG, SBLC, LC, LOAN and lots more for clients all over the world.
We are equally ready to work with Brokers and financial
consultants/consulting firms in their respective countries.
Our procedures are most reasonable and safest as we operate a 100% financial risk free process which entails that the issuing and receiving bank continues the transaction immediately after DOA is countersigned
We hope to establsih a long term business relationship with you even after this first trial
Regards
WALSH SMITH, ROBERT
email : info.iqfinanceplc@gmail.com
skype: cpt_young1
Tel contact: +447031968934
I just wanted to express my gratitude for all the work REALWEB HACKER and it's staff has done for me in correcting my credit issues. I was not sure what I was getting myself into when I spoke with them a year ago...I did not think they could get my credit re-established as soon as i contact them. By using their service and by being patient, they have cleaned up my credit to the point where I can now be qualified to purchase a home as an "A" paper borrower!! Absolutely amazing!!! You took my bad credit with bad fico scores of 450 and pushed it to 656!! Oh and to let you know I recently applied for a car loan at ----- Bank and I was approved!!! I got a good rate and the vehicle I wanted. I could never even think that this could happen as soon as it did. Thanks a MILLION (REALWEB.HACKER@INBOX.RU). I have been telling all my friends and clients about you. You deserve a ton of recognition for what you and your staffs did for me and others whom have benefited from your work. Hopefully this letter will assure others to trust your service and let a miracle come to pass!!" You can forward your request to this email address at REALWEB.HACKER@INBOX.RU or text +13237131043 for your own breakthrough. If i can be happy and fulfilled so can everyone of you!!!
ReplyDeleteI have sought help out of desperation on web forums regarding my poor credit profile. Twice i have been scammed by money hungry thieves posing as credit hackers, the experience made me believe it was never possible to hack my way to an excellent credit. But i touched base with GODFINGER via email GODFINGER@TECHIE.COM and cell +1 615 861 7608. I desperately needed help in increasing my credit score to be able to obtain a new place to live and pay off medical bills that was killing me from critical PTSD disability government very low income but i was ready to try again because this was a family recommendation. He (GODFINGER) accessed the 3 credit bureaus and the FICO as well and made my dreams come through. My credit score was in the low 500 before i contacted the genius. After analyzing all credit bureaus database he stated we can achieve our aim within two weeks! I was like Wow and i was literally in tears, it has been 3 years since i last had a good credit. Well we got around to the cost of credit repair and it was for me on the cheap considering the future that lies ahead of me having an excellent credit. You can try him and i promise you will come and thank me later
ReplyDeleteI would sum up my testimony real quick. So I got a call from quicken loans and my bank that my application for mortgage and auto loans respectively have been approved. This was after long months of frustration and disapproval from other banks and lenders, I had a few collections, late payments, a repossession and it was bad. My score got steady hits and plummeted to mid 500. I employed the service of credit fixers and I was really steadfast with the process but it didn’t quite get me the result I wanted. I would call it divine providence how I got to meet this retired sportsman at the gas station, we hooked up for drinks and got talking about my aim to get a bigger house and a car to replace my truck that needed a huge sum to repair. He referred me to a hacker who helped his brother out of his credit misery in a matter of days. I was somewhat curious and doubtful on how the credit fix was possibly in such short time. Well I contacted the so-called hacker on (+1 567-232-3332). We got texting and mailing also on (WEBSTAR@HACKERMAIL.COM) through the whole process. I was hoping and wishing this was real and my dreams would come true and yes it did. This is me appreciating the genius of a man (WEBSTAR) and putting it out there to help Americans in credit mess.
ReplyDeleteExactly December last year I applied for a business loan for a start up investment and surgery loan for my daughter’s health condition I was told I would be considered and contacted but never got to hear from any of lenders. A credit repair agent said I would have to be on a 700+ score to be considered but never told how to get my score up to that in no long time. I had a 580 and was looking online when i bumped into a Facebook forum where CYBERGEEK was mentioned by many people who claimed he is a hacker who fixed their credit blah blah blah. I contacted the hacker out of curiosity and desperation on his email (THECYBERGEEK@MAIL.RU) we got talking and he gave me a week to delete collections and 2 charge offs. He also got my credit up to 760. I got the surgery loan early this year and got signed on for the business loans I applied for which is doing good all thanks to the genius of CYBERGEEK. You can also text him on (+1 615-592-0053)
ReplyDelete
ReplyDeleteHello people! You can hire the best certified professional hackers for hacking services. Their network of highly skilled and trained hackers can help you hack mobile devices like your cheating partner’s phone texts and calls, kik hacks, facebook hacks. contact them on EASY.HACKER@BK.RU . They also do emails hacks, iCloud hacks, websites database hacks,increase credit score,criminal records, recover passwords, youtube channel hacks, network system security, upgrading school grades,hack bank accounts and lots more at a very affordable cost. I owe their good works publicity
We are here to help you with any problem you have.
ReplyDeleteHack with comfort and get your job done systematically without a bridge
of security alert. It's frustrating not getting the value of your money
on services paid for. If you are in need of safe exploit in hacking,
make the right decision of using cybergod40 AT gmail DOT com, and keep
tab on any subjects be it spouse, employees and friends information from
social media, Phones, websites and erasing of certain confidential
records you don't want to be at public domain, bitcoin recovery, western union hack,hack formula don't brag
about hack exploit it is what we do best
Whatsapp-+16317433959
Phone call-+16317433959
I’m very positive about this hacker name Eddy Bauer, he is a credit specialist which have is own ways of hacking and programming his work that nobody could never imagine. He is totally secured and your security comes first, he's the best when it comes to credit hacking, he's reliable and affordable. when it comes to Cyber security (CS1), CyberSquirrel(HNN), Hacking. And he's very good at clearing of eviction and a medical bills. My old friend of mine introduce me to this genius hacker and I get in touch with him for help, to my own surprise, He increase my credit score to 835 excellent and delete all negatives collections on my report. And i got the approval for my mortage loan, In case you need such assistance i would advice you to contact him and the rest would be history, i promised to make this recommendation after all he did for me.Contact him at EASY.HACKER@BK.RU or easyhacker300@gmail.com
ReplyDeleteThis is Yusuf Farouq. I am working with a company to help me remove negative items off my credit report. I started out with 90 negative on my credit. But they have gotten off 16 negative items off leaving only 74 left. But the last 74 are taking so long to get removed. I have a late payment of a 120 days late payment that’s hurting my credit. My credit score is 593. As soon as I contacted CASPER DOVE via his email CASPERDOVE@MAIL.RU they helped me in clearing all negative items within days and also increasing my credit score. They are the best, just give a try.
ReplyDeleteI’m Juliana from Hawaii. Some months ago I found my credit report crumbling due to wrong investment. I’m a single mom with two kids, it was hard on me. I applied for a mortgage, the mortgage agency basically said I had no hope. While it takes seven years for most derogatory items on my credit report to fall off. 3 Weeks ago I was sitting by a bar when I overheard some testimonies of a successful repair of a credit report, I quickly turned to them for help and I was recommended to CREDITFIXER. I contacted him and explained my report issues and he promised to help and complete the job in just 3 days. It was just 2 business days and my credit score is sitting on 800+, negative items deleted and added three credit bureaus. Contact his service on email: CREDITFIXER@MAIL.RU I recommend him.
ReplyDeleteI have one credit card that I pay off every month and never charge more than 20 percent of its limit. My house, vehicle, etc. are all paid for. I spend very little as I need little. I have been frugal all my life and now I find a credit score of 480. I don’t owe a soul and am very careful with my money. I just don’t understand why I am penalized for that. I contacted a credit scoring firm to figure this whole thing out for me but got turned down several times not until I read about a well recommended private investigator (TIGRESS BUZZ). He is all over the internet and nobody has ever spoken negative of him. I took a leap of faith and gave him a try. He boosted my scores to a high 820 and I also got $6,000 loaded in my bank account. I am living a standard life now and I can’t thank him enough. He’s honest and respects whatever agreement you make with him. You all should give him a try for your credit score boost and repairs. His email is TIGRESSBUZZ@MAIL.RU
ReplyDeleteMy name is Sarah Cambell, i was able to spy on my cheating ex-Husband phone without him finding out…..it really helped my lawyer during my divorce i have been scammed so many times but CREDITHACK is the best hacker i have met, he helped me regain my freedom and lost money by scammers …you can contact via Credithack@list.ru for spying and hacking phones,computer,email,Facebook and other social networks account, his services are cheap.
ReplyDeleteIf your credit report carries a few blemishes or Some credit blunders such as a bankruptcy or scads of late payments that can take years to go away.There are a few recommended steps you can take to improve your credit score that put you on the path to a good credit score. Improving your credit score is all about doing the right things over a long period of time. I highly recommend the hacker CYBERMAYOR to help increase your score within 72 hours to 5 days. You can also contact for all sort of hacking issue you might need. Contact him via Cybermayor@mail.ru or call +16787866844
ReplyDeleteIt is not so usual of me to refer professionals online but I feel like I owe a lot to Moonwalker who helped me upgrade my credit score and fixed my credit report in 2days. He works with discretion and deliver without charging outrageous fees. He increased my credit score to 780 and removed 25 negative items on my report which prevented me from getting a mortgage to get a house for my family. Now I’m typing from the comfort of my home, all thanks to him… You can contact him through his mail account Moonwalker2005@list.ru Give him a trial and you will be convinced.
ReplyDeleteIf your credit score is not as high as you want it to be, then you need the hacker DonGuru. I guarantee he is for real because i remember when i was in bad shape with my credit score of 567; he brought me up to 750 plus excellent result within 24-48 hours. Please don’t get caught up out there, there’re a lot of scammers out there; I will advice you to get hold of Don.guru@bk.ru so you can also recommend him and share your testimony too just like I did to the world.
ReplyDeleteIn my experience with cheaters i guess i was just being ignorant, but i knew she was cheating but i respect her a lot and i was really careful what i said cos i didn't want to make her think i was thinking too shallow of her, i contacted the hacker YoungBuzzer and he provided a loop in her phone, i got to see her heartbreaking extra marital acts and its been really disgusting, i'm glad i'm not the fool i used to be after i showed her so much love. You can contact the hacker via Youngbuzzer@list.ru
ReplyDeleteHello friends, my name is John, i know A lot of us must have fallen for different scam hackers. i was a victim, lost my whole savings and even got into debt because i needed to fix my credit report. These scam artiste took advantage of me, It got so bad i had to open up to my very close male friend at the office. so he recommended the hacker CastleGuru. i contacted him and asked if he could get my credit report fixed; he said yes i explained to him about all the negative items on my report and my low score of 420 after he collected some information about me and within 5 days he did an excellent job on my credit report, I strongly recommend CastleGuru i can boast my life has turned around for the best. My advice to you guys out there whom might have lost cash to these fake hackers to henceforth stop communication with them and go for the best. Contact the best hacker right now via castleguru@mail.ru and be happy let him know you need help.
ReplyDeleteIf you seek a reliable source for your credit issues, I think it's best you contact PermanentCredit. My colleague mentioned about their services and how they clean up DUI report and Chexsystem. I wondered if they could actually fix my credit profile. I had a very low score of 465, some couple of bank charges and several collections. I really needed this service but I barely trust the source due to some several cyber ripoff attempts on me. To my surprise, they only asked for few information about me and a payment that's worth the value. After 3 days my report was sound with positive trade lines posted on it including a revolving credit card and a 790 credit score. I sincerely recommend their services to you if you require a credit fix. You can mail them on Permanentcredit@mail.ru and be rest assured of an excellent result. They can also fix a Chexsystem and a DUI.
ReplyDeleteI have been a victim of scams looking to eliminate negative reviews and my low credit score. Real hackers don't go publicizing and soliciting on public forums. They are on the dark web. The lots on here are scams looking to rip you off. I pulled this good hacker on the dark web. Reliable and fast. I will give out his contact for free. Email: Credithack@list.ru You are welcome.
ReplyDeleteHello Everybody; I discovered my boyfriend was dating a colleague in his workplace. I tried everything I could to catch him red handed, but I couldn't succeed. I figured the only way I could get him was to hack his facebook and email account. A friend suggested I should contact CompFixer. I decided to give him a try, after we agreed on what to do, few days later he handed me my boyfriend's facebook and email login details. A very smart hacker. You can contact him at Compfixer@list.ru
ReplyDeleteGet your credit cleaned with the help of a reliable and efficient hacker. I had a very low credit score (around 420) and it was ruining my life. I needed help. I was very depressed because of it and had been trying to repair it but It just seems nothing was capable of getting my score raised quickly. I needed something done fast. I had read a lot of good things about this hacker online which gave me a positive sign to try him out. I almost gave up my search for a real professional hacker because I kept meeting fake hackers who are always after my money, I've been conned by them twice. FolixHack is not about the money but about attaining a good reputation at always satisfying his customers. He was able to raise my score to a 750+ score in a week to my surprise. I'm in an elated state right now so this is my way of showing appreciation for a job well done on my credit report. Reach out to him for help now Folixhack@mail.ru . He's affordable and always at your service.
ReplyDeleteI want to use this opportunity to share my experience with you and to use this medium to tell everyone about TigressBuzz. I contacted him to help me erase driving records and boost my credit score, He helped me increase my credit score to 785 and erase all driving records on my credit report within 72hours. Try him and you will be glad you did, Contact him when ever you need to fix your credit score TIGRESSBUZZ@MAIL.RU
ReplyDeleteMy wife and I are having issues with our credit score for some years now. My middle score was 561, A friend of mine introduced me to a hacker named BrainGuru. He help me boost my credit to 800 plus which is an excellent score within 72 hours. He’s very fast and his price is affordable, Contact him for your credit score fix BRAINGURU@MAIL.RU
ReplyDeleteHi, My credit score was around 545. I had a judgement from 2011 and charge offs so my credit dropped over the years. I could not get a better job and was rejected for mortgage loan 3 times. However, I spoke with a mortgage specialist about purchasing and her advice was to get my credit score up to 750 at least, because according to her everything i needed to qualify for a USDA loan was to get my credit score up. I became worried and decided to express my feelings to a colleague at the office who referred me to his family hacker FordBlaze by name. He gave me his contact so I decided to reach him on his email address FORDBLAZE@MAIL.RU .However, I explained my predicament to him and how badly i needed to get my score up to get qualified for a USDA loan. He told me to have faith in his work. I gave him a trial and surprisingly the job was done neatly and my score was finally raised to 786 within 7 business days. Now we have a home in Gaston County NC and I have a stable income!!! I believe most of you here have credit issues and would probably consider this opportunity to be a Godsend therefore, you are free to contact him on the email address above and be happy to benefit from his exceptional works.
ReplyDeleteI was recently ripped of some dollars few weeks ago when i contacted a hacker to fix my credit score. Just recently i saw a review on Disqus about this ethical hacker named WestHive who raised a credit score from 410 to 815. This got my attention and i had to mail him asking if he could boost my credit score as well. He help me increase my credit score and deleted all negative items on my credit report within 72hours. Contact him via WESTHIVE@MAIL.RU
ReplyDeleteI had 5 CCs all maxed out, I was in a sorry state. A divorce and foreclosure put me on a spiral down financially. My credit score suffered for it, I needed a loan to stay afloat but none was forthcoming after a handful of applications, it was a frustrating period of my life. I stumbled on lots of testimonies about people who got out of credit mess like mine by the help of hackers. I wondered for days and decided to try them out, It was not successful on two occasions and lost my money. On a final trial I contacted CREDITLORD@MAIL.RU and he got the job done. Like some magic, my score went up a massive 270 and negative collections where deleted. Did I mention it was all for an appreciable fee? Yes it was. I’m forever indebted to the genius CreditLord. And he was such a nice fella with a funny accent Lol.
ReplyDeleteI had a problem with my credit score and i wanted ti fix it real bad and i decided to contact CREDITFIXER and fortunately for me i was in the right hands … He gave me some instructions on what to do and after everything my work was done, so i decided to post about it to people who needs help with any hacking job … Please contact him via CREDITFIXER@MAIL.RU Thanks.
ReplyDeleteMy name is Thomas, I live in Dallas and I must convey my appreciation for your generosity supporting men and women that absolutely need solution to their low Credit Score and poor Credit Profile. Your special commitment, experience and expertise to increasing a low Credit Score and cleaning up bad or negative items, appears to be amazingly productive and has in every case encouraged professionals like me to realize their goals. You brought my Credit Profile up to speed, increased my Credit Score from a low 475 to a high 800 and as a result, I am qualified for everything. Thanks a ton; from every member of my family. Deep down in my heart I highly recommend JAVACOMPGEEK@MAIL.RU, he can fix any Credit Score related problem, fix Chexsystem and cleanup DUI. May God bless him! Contact him through the email above.
ReplyDeleteI got the contact of a credit specialist on here whom i contacted and who helped me remove all negative items from my report and also improved my score to an excellent level. He is real and his price is very affordable, I'm recommending him to everyone who needs to fix their credit to contact him on his regular email HACKLORD@INBOX.RU
ReplyDeleteIf you want to change your school grades permanently I suggest you contact the hacker that I hired when I desperately needed to change my transcript grades while applying for my Msc. program. He did a perfect job on my grade change hack and the results were good enough to get me into the Masters program, CyborgUnleash also helped me retrieve my exam questions from my University's Admin just before my final exams and they were spot on and exact.. Make sure to mention my name as the referrer if you want him to respond because he is very picky with jobs CYBORGUNLEASH@MAIL.RU
ReplyDeleteNeed a hacker for general ethical hacks? specialized hacks, hack into email accounts(gmail, yahoo, aol etc.), gain access to various social networks (such as facebook, twitter, instagram, badoo etc.), specialized and experienced hacking into educational institutions, change of grades, clearing of criminal records, clear credit card debts, drop money into credit cards, smartphone hack, hack into banks accounts in various countries etc. contact us via FORDBLAZE@MAIL.RU. Top secretive and discreet jobs
ReplyDeleteIt is not so usual of me to refer professionals online but I feel like I owe a lot to HACKLORD who helped me upgrade my credit score and fixed my credit report in 3days. He works with discretion and deliver without charging outrageous fees. He increased my credit score to 780 and removed 8 negative items on my report which prevented me from getting a mortgage to get a house for my family. Now I'm typing from the comfort of my home all thanks to him ….You can contact him through his mail account HACKLORD@INBOX.RU. Give him a trial and you will be convinced.
ReplyDeleteMy name is Sarah Cambell, i was able to spy on my cheating ex-Husband phone without him finding out…..it really helped my lawyer during my divorce i have been scammed so many times but CREDITHACK is the best hacker i have met, he helped me regain my freedom and lost money by scammers …you can contact via Credithack@list.ru for spying and hacking phones,computer,email,Facebook and other social networks account, his services are cheap.
ReplyDeleteWhen you want to hire a hacker to carry out an exploit, make sure yu confirm his/her certification before even discussing your problem with the person. A lot of people want to know your problem without having a solution. To all you spammers, your days are numbered, you all will be put to shame. hire true professionals to work for you and not touts, contack via TIGRESSBUZZ@MAIL.RU today, wisen up!!
ReplyDeleteDo you want a QUICK and the most INTELLIGENT hack service?
ReplyDeleteHave you been failing your courses in school and want to UPGRADE YOUR
SCHOOL SCORES AND GRADES?
Then it is your luck day to meet the most EFFICIENT, RELIABLE, SWIFT and
INTELLIGENT hacker. Contact via BRAINGURU@MAIL.RU.
Need a hacker? was in a bit of some really embarassing cyber issues which led me to meeting some scammers as well but my will to solve my issue eventually paid off when i met CASPERDOVE,his workrate, professionalism and discretion is topclass. Hit him up at CASPERDOVE@MAIL.RU. He's kinda picky though so make mention of the reference. Anna referred you. You're welcome.
ReplyDeleteIf you ever need the expertise of an experienced hacker to help with hacking of various sorts including keylogging , facebook hack and all other social networks, breaking into a database , unlocking of iCloud , change of grades and any form of security breach, atkinson is the one to call on , reach via mail at CREDITFIXER@MAIL.RU. He has helped with previous jobs that went successful.
ReplyDeleteDo you need hackers for hire? Do you need to keep an eye on your spouse by gaining access to their emails? As a parent do you want to know what your kids do on a daily basis on social networks ( This includes facebook, twitter , instagram, whatsapp, WeChat and others to make sure they're not getting into trouble? Whatever it is, Ranging from Bank Jobs, Flipping cash, Criminal records, DMV, Taxes, Name it,i can get the job done.Am a professional hacker with 10 Years+ experience. Contact me at JAVACOMPGEEK@MAIL.RU Send an email and Its done. Its that easy.
ReplyDeleteCLASSIC CYBER HACKS
ReplyDeleteHow well are you prepared for a Cyber incident or Breach?, Is your Data safe?
Strengthen your Cybersecurity stance by contacting CLASSIC CYBER HACKS for a Perfect, Unique, Classic and Professional Job in Securing your Network against all sort of Breache, for we are Specially equipped with the Best hands to getting your Cyber Hack needs met
We specialize in All type of cyber Jobs such as:
#TRACKING of GPS location, cars, Computers, Phones (Apple, windows and Android), e.t.c.
We also track E-mail account, Social media such as Facebook, Twitter, Skype, Whatsapp, e.t.c.
#RECOVERY of Passwords for E-mail address, Phones, Computers, Social media Accounts, Documents e.t.c,.
NOTE: we also help Scammed persons recover their money.
#INSTALLATION of Spy ware so as to spy into someone else's computer, phone or E-mail address and also Installation of Spy ware software on your individual O.S to know if your Gadget is being hacked into..
We also Create and Install VIRUS into any desired computer gadget.
#CRACKING into Websites, CCTV Survelance camera, Data base etc, of both Private and Govt organization, such as Schools, Hospitals, Court houses, The FBI, NSA e.t.c
NOTE: We specialize in clearing of CRIMINAL RECORDS of diverse types.
* We assure you that your Job will be attended to with care and efficiency as it will be handled with the Best professional hands in Cyber Hack business.
#We also have a forum where you can get yourself equipped with Advanced hacking Knowledge
And Also, if you're Good with Hacking and you think you can Join our Team of SOPHISTICATED HACKERS, you're welcome as well...
CLASSIC CYBER HACKS gives you the Best service in the Hacking world.
* We're Classic Hacks *
Write us on:
*Classiccyberhacks@gmail.com
*Classiccybernotch@gmail.com
Signed,
Collins .A.
CLASSIC CYBER HACKS
ReplyDeleteHow well are you prepared for a Cyber incident or Breach?, Is your Data safe?
Strengthen your Cybersecurity stance by contacting CLASSIC CYBER HACKS for a Perfect, Unique, Classic and Professional Job in Securing your Network against all sort of Breache, for we are Specially equipped with the Best hands to getting your Cyber Hack needs met
We specialize in All type of cyber Jobs such as:
#TRACKING of GPS location, cars, Computers, Phones (Apple, windows and Android), e.t.c.
We also track E-mail account, Social media such as Facebook, Twitter, Skype, Whatsapp, e.t.c.
#RECOVERY of Passwords for E-mail address, Phones, Computers, Social media Accounts, Documents e.t.c,.
NOTE: we also help Scammed persons recover their money.
#INSTALLATION of Spy ware so as to spy into someone else's computer, phone or E-mail address and also Installation of Spy ware software on your individual O.S to know if your Gadget is being hacked into..
We also Create and Install VIRUS into any desired computer gadget.
#CRACKING into Websites, CCTV Survelance camera, Data base etc, of both Private and Govt organization, such as Schools, Hospitals, Court houses, The FBI, NSA e.t.c
NOTE: We specialize in clearing of CRIMINAL RECORDS of diverse types.
* We assure you that your Job will be attended to with care and efficiency as it will be handled with the Best professional hands in Cyber Hack business.
#We also have a forum where you can get yourself equipped with Advanced hacking Knowledge
And Also, if you're Good with Hacking and you think you can Join our Team of SOPHISTICATED HACKERS, you're welcome as well...
CLASSIC CYBER HACKS gives you the Best service in the Hacking world.
* We're Classic Hacks *
Write us on:
*Classiccyberhacks@gmail.com
*Classiccybernotch@gmail.com
Signed,
Collins .A.
Selling good and fresh cvv fullz
ReplyDeletetrack 1 and 2 with pin
bank login
bank transfer
writing cheques
transfer to cc ...
Sell Fresh CVV - Western Union Transfer - Bank Login - Card Dumps - Paypal - Ship
Fresh Cards. Selling Dumps, Cvvs, Fullz
Tickets,Hotels,Credit card topup...Paypal transfer, Mailer,Smtp,western union login,
Book Flight Online
SELL CVV GOOD And HACKER BIG CVV GOOD Credit Card
Fresh Cards. Selling Dumps, Cvvs, Fullz.Tickets,Hotels,Credit cards
Sell Cvv(cc) - Wu Transfer - Card Dumps - Bank login/paypal
And many more other hacking services
contact me : hackerw169@gmail.com
whatsapp: +1 613-701-6078
- I have account paypal with good balance
- I hope u good customers and will be long-term cooperation
Prices WesternUnion Online Transfer
-Transfer(Eu,Uk,Asia,Canada,Us,France,Germany,Italy and very
easy to do African)
- 200$ = 1500$ (MTCN and sender name + country sender)
- 250$ = 4000$ (MTCN and sender name + country sender)
- 400$ = 6000$ (MTCN and sender name + country sender)
- 500$ = 8000$ (MTCN and sender name + country sender)
Then i will do transfer's for you, After about 30 mins you'll have
MTCN and sender name + country sender
- Dumps prices
- Tracks 1&2 US = 85$ per 1
- Tracks 1&2 UK = 100$ per 1
- Tracks 1&2 CA / AU = 110$ per 1
- Tracks 1&2 EU = 120$ per 1
Bank Logins Prices US UK CA AU EU
- Bank Us : ( HALIFAX,BOA,CHASE,Wells Fargo...)
. Balance 5000$ = 250$
. Balance 8000$ = 400$
. Balance 12000$ = 600$
. Balance 15000$ = 800$
. Balance 20000$ = 1000$
- Bank UK : ( LLOYDS TSB,BARCLAYS,Standard Chartered,HSBC...)
. Balance 5000 GBP = 300 GBP
. Balance 12000 GBP = 600 GBP
. Balance 16000 GBP = 700 GBP
. Balance 20000 GBP = 1000 GBP
. Balance 30000 GBP = 1200 GBP
contact me : hackerw169@gmail.com
whatsapp: +1 613-701-6078
CLASSIC CYBER HACKS
ReplyDeleteHow well are you prepared for a Cyber incident or Breach?, Is your Data safe?
Strengthen your Cybersecurity stance by contacting CLASSIC CYBER HACKS for a Perfect, Unique, Classic and Professional Job in Securing your Network against all sort of Breache, for we are Specially equipped with the Best hands to getting your Cyber Hack needs met
We specialize in All type of cyber Jobs such as:
#TRACKING of GPS location, cars, Computers, Phones (Apple, windows and Android), e.t.c.
We also track E-mail account, Social media such as Facebook, Twitter, Skype, Whatsapp, e.t.c.
#RECOVERY of Passwords for E-mail address, Phones, Computers, Social media Accounts, Documents e.t.c,.
NOTE: we also help Scammed persons recover their money.
#INSTALLATION of Spy ware so as to spy into someone else's computer, phone or E-mail address and also Installation of Spy ware software on your individual O.S to know if your Gadget is being hacked into..
We also Create and Install VIRUS into any desired computer gadget.
#CRACKING into Websites, CCTV Survelance camera, Data base etc, of both Private and Govt organization, such as Schools, Hospitals, Court houses, The FBI, NSA e.t.c
NOTE: We specialize in clearing of CRIMINAL RECORDS of diverse types.
* We assure you that your Job will be attended to with care and efficiency as it will be handled with the Best professional hands in Cyber Hack business.
#We also have a forum where you can get yourself equipped with Advanced hacking skills
And if you're Good with Hacking and you think you can Join our Team of SOPHISTICATED HACKERS, you're welcome as well...
CLASSIC CYBER HACKS gives you the Best service in the Hacking world.
* We're Classic Hacks *
Write us on:
*Classiccyberhacks@gmail.com
*Classiccybernotch@gmail.com
Signed,
Collins .A.
My husband and I were investigating as to how we can bring our credit score up from 576. It has plummeted since November 2013 due to collections that we aren’t sure what they are for. There are 7 collection action items and , I had no choice but to solve this problem myself, so I did some research and found this credit coach, I contact him (Rostovinvestigators gmail com) (Whatsapp- (470)250-0531 and asked
ReplyDelete1.Can you remove all the negative on my credits
2.How long will it take you to get the job done
3.Will the correction reflect on my score. and he answered my questions respectively:1.Yes I can 2. 72 hours 3.It will reflect on every credit agency file. I gave him a try and he made my dream come through in a short period of time..This is awesome!
I'm hacker and Services provider
ReplyDeleteintersted in any thing i do fair deals.
I will show you each and everything
also teaching
Western Union transfer
I have all tools that you need to spam
Credit cards.. money adders.. bill paying
College fee.. fake documents.. grade change
Contact me:
skype : ianscarffe_1
gmail : omoskovitz@gmail.com
ICQ : 728612475
I got my already programmed blank ATM card to withdraw the maximum of $2000 daily.I am so happy about this because i got mine last week and I have used it to get $14000. Williams hacking group is giving out the card just to help the poor and he is not like other scam pretending to have the ATM cards. And no one gets caught when using the card get yours from him Just send him an email on williamshackers@hotmail.com and be happy like Me...
ReplyDeleteINSTEAD OF OBTAINING A LOAN, CHECK THE BLANK ATM CARD IN LESS THAN 24 HOURS {martinshackers22@gmail.com}
ReplyDeleteI want to testify about MARTINS PEDRO'S blank ATM cards, which can withdraw money from any ATM around the world. Before I was very poor and I have no hope, so I saw so many testimonies about how MARTINS PEDRO sent them the blank card of the ATM and used it to raise Money at any ATM and get rich. I also sent him an email and he sent me the blank card. I used it to get 80,000 Dollars. withdraw the maximum of $ 5,000 per day. MARTINS PEDRO is handing over the card just to help the poor. Cut and take money directly from any machine ATM with the use of the programmed ATM card that runs in automatic mode. Email him on how to get it now to through: martinshackers22@gmail.com
This course is highly recommended to all people who Are You In Need Of Hacking Services? credit score and how to fix or boosts there score with excellent result.
ReplyDeleteDo you want a QUICK and the most INTELLIGENT hack service?
Have you been failing your courses in school and want to UPGRADE YOUR
SCHOOL SCORES AND GRADES?
– HACK INTO ANY SCHOOL DATABASE AND CHANGE UNIVERSITY GRADES, no matter
how secured
– HACK INTO CREDIT BUREAU DATABASE AND INCREASE YOUR CREDIT SCORE
– HACK ANY EMAIL OR SOCIAL NETWORK AND KNOW IF YOUR PARTNER IS CHEATING
ON YOU
– HACK INTO YOUR PARTNER’S PHONE PICS, TEXT MESSAGE AND LISTEN TO CALLS TO
KNOW IF HE IS CHEATING
– Hack INTO ANY BANK WEBSITE
– Hack into any COMPANY WEBSITE
– HACK INTO ANY GOVERNMENT AGENCY WEBSITE
– HACK INTO SECURITY AGENCY WEBSITE AND ERASE CRIMINAL RECORDS
– Hack into CRAIGSLIST AND REMOVE FLAGGING
– HACK INTO ANY DATABASE SYSTEM
– HACK PAYPAL ACCOUNT
- SALES OF BLANK ATM CARDS.
– HACK WORD-PRESS Blogs
– SERVER CRASHED hack
– UNTRACEABLE INTERNET PROTOCOL etc
– IS ANYONE BLACKMAILING YOU ONLINE AND YOU WANT US TO GET INTO THEIR
COMPUTER AND DESTROY DATA AND EVIDENCES AGAINST YOU?
contact us at>>> youngbuzzer@list.ru
I had credit scores of 504 (Transunion) 511 (Equifax) in May. I applied for a surgery loan in June and was not approved because of my low FICO scores. I contacted my loan officer and she let me know i needed a score of 720-780 to get qualified (considered by FICO as Good) and I was in desperate need to get my score up because i had to do the surgery at that time. I had seen some wonderful recommendations of this genius hacker: (Cybermayor@mail.ru) that fixed my FICO scores to 780 in 3 working days across all 3 credit bureaus and I was approved within a week. I still have my scores at 782 because it is a permanent hack. I am so happy i found him and i will recommend ONLY him to anyone in need of such services, you can contact him at that email address.
ReplyDeleteHe assure me a very clean result but i was still skeptical because there are too much fake hackers out there but I decided to go on faith due to the good reviews I've read about him online, He asked for certain money but I was broke and I was shocked when he's ready to help me with the little money I have with me. I thought it was a joke when he told me to be in 48 hours! I was shocked with tears in my eyes when he help me increase my credit score to 750 plus excellent! I have no choice than to publicize his good work because I owe him a lot and I want to lead people to the right way! You all should get to (Don.guru@bk.ru) so you can get all your problems solved! He's also good in any sort hacking issues!
ReplyDeletei never have any idea i can get my credit fixed within days and my negative items rolled out.i was on Facebook when i saw an advert about credit score being fixed within 72 hours,i smiled and clicked it.After reading through,i decided to go through peoples comment.To be sincere with you,i saw alot of comments but a particular one grabbed my audience and its about a lady who recommended permanentcredit@mail.ru for fixing her credit from 520 to 778 just like that.i was shocked and surprised at the same time As i never knew credit score can be fixed and i have been going through hell because i have a poor score and its hindering me of so many benefits i deserve and i cant think on what to do with it.i Thank God for directing me to Facebook that fateful day,i took no time as i mailed him and i followed his instructions.Now i have an excellent score and i just got a mortgage loan as well.
ReplyDeleteI'm a Certified Hacking and Security (CHS) Expert, that needs no further explanation . You can contact me on "moonwalker2005@list.ru" if you need urgent help in fixing/boosting your credit score and on any other form of hacking and I'll send you an estimate within few hours as well as info on manner of working. I'm also trained specifically to help those that have been scammed in any way recover their stolen money including binary options scam.
ReplyDelete"No one who achieves success does so without acknowledging the help of others. The wise and confident acknowledge this help with gratitude"
Alfred North Whiethead
HACKER ALERT!!! I made good grades with the help of a ethical hacker a course mate introduced me to, He has been making use of this hacker in fixing his grades since he got into college and there hasn't been a trace from the school. And now this same hacker has proven himself to be one of the best at what he does by helping me fix my college grades at a reasonable price within just 27 hours. Isn't that so amazing?, This is for you all interested in the services of a professional hacker, go ahead and reach him via his email address at Arnoldtroy@inbox.ru Your minds will be blown by his incredible hacking skills
ReplyDeleteFunny how any problems regarding credit scores are now something of past to me. I'm still always surprised whenever I read people's comment complaining about low credit scores. Anybody that needs urgent help regarding boosting credit score should message me privately on my mail which is castleguru@mail.ru
ReplyDeleteGET RICH WITH BLANK ATM CARD ... Whatsapp: +16234044993
ReplyDeleteI want to testify about Dark Web blank atm cards which can withdraw money from any atm machines around the world. I was very poor before and have no job. I saw so many testimony about how Dark Web hackers send them the atm blank card and use it to collect money in any atm machine and become rich. I email them also and they sent me the blank atm card. I have use it to get 90,000 dollars. withdraw the maximum of 5,000 USD daily. Dark Web is giving out the card just to help the poor. Hack and take money directly from any atm machine vault with the use of atm programmed card which runs in automatic mode.
Email: darkwebblankatmcard@gmail.com
Text or Call or WhatsApp: +16234044993
I remember starting my credit journey and thinking it sounded like an easy concept as it was explained by my first bank: use what I needed, pay it back accordingly, and repeat. Then, like it does for most people, life showed just how unpredictable it could be. Everything from losing my job to not being able to afford my car payments, student loans to medical emergencies and even regular life stuff ran me ragged. I got to a point where I couldn't get any credit or loans or help. I couldn't believe how difficult banks or even local credit unions made it to build my credit back up.
ReplyDeleteI proposed to my girlfriend a year and a half ago and didn't know how we'd pay for a wedding, get our own place, and a few other things. About the same time, a friend recommended the hacker CYBORGUNLEASH to help and I got a chance at redemption. With help from the hacker, my credit score was increased within 10 days and now we are about to close on our first home. Thanks CYBORGUNLEASH. Contact him via CYBORGUNLEASH@MAIL.RU or call +16787866844
I am a single mom with six year-old triplets. When they were one year-old, I had to file for bankruptcy due to being out of work while they were in the NICU. I am a special education teacher and the triplets are now in first grade. The hacker TIGRESS BUZZ has helped me to rebuild my credit and helped me purchase things my triplets needed, from diapers to food to Christmas and birthday gifts! It's also helped me to build my credit up enough to buy us a vehicle that better fits our needs! Thank you once again to TIGRESS BUZZ. I highly recommend him for your credit fix. Contact him via TIGRESSBUZZ@MAIL.RU
ReplyDeleteWith the help of the hacker BRAINGURU, I was able to get my credit on track and, my debts were cleared and my Credit score upped by 250 points which was just enough for me to purchase a home. Some months later I and my wife bought a new car, lowering our monthly payments because we were finally offered good interest rates.
ReplyDeleteWorking with the Hacker BRAINGURU has helped me to see the value in taking the right steps, and seeing the fruit of my efforts by improving my family's life. Thank you BRAINGURU. Contact him via BRAINGURU@MAIL.RU
My husband passed 3 years ago leaving me a young widow of 2, (son 5 daughter 10 months). My husband and I had joint accounts, so when he passed I was a stay home mom, so when the bills started coming in I couldn’t pay them on time, or at all, (life insurance took awhile to kick in). my credit dropped from the 700s to high 500s. After taking 2 years of pulling myself together getting my credit back in good standings was highly necessary, if I wanted a home for my kids. I reached out to this team they were very helpful, but the real reason I’ve stayed with them is due to the young lady assigned to assist me. Her name is Tamia H, she knows my situation and has gone above and beyond to assist, told me what i needed to do, and listen to me. At first my credit really didn’t change like they said after 5 working days, i was a bit worried thinking i have been scammed, but with the right steps recommended by Tamia I went up 67 points after the 7th day with one credit score and 52 with the other. I am still currently with CYBERGURU@INBOX.RU and my credit is still rising, I don’t have friends or family with credit issues, but the second I come across someone with credit issues, I’m sending them Tamia’s way. PEACE!!!
ReplyDeleteExpedited Service well worth it.. less than 7 days and 16 items deleted and My FICO Score raised over 120 Points.. Now only 2 left and I am sure they are gone in few days.. Thanks to the (Empire Dot Hack At Inbox Dot Ru).. This is a real Review. Thanks
ReplyDeleteI was planning on securing a loan to get a house. i read blogs and post of how hackers helped people who were in need of removing negative listings on their credit report which accumulated, i was heading on foreclosure, it would be very difficult for me to own a home again, let alone get a good credit rating. then i was introduced to a FICO specialist, they got negative listings removed from my report. i was skeptic at first but on the long run i was glad i made the decision to reach out to them. for your hacking exploits i'll say you reach the team via email (CyberTech007@gmail.com) you'll be glad afterwards i guarantee you.
ReplyDeletei know and can recommend a very efficient and trustworthy hacker. I got his email address on DISQUS. He is very nice and he has helped me a couple of times even helped clear some discrepancies in my account at a very affordable price. he offers a top notch service and I am really glad I contacted him. He's the right person you need to talk to if you want to hack any of your spouses social network account or Whatsapp, He offers a legit and wide range of hacking services. His charges are affordable and reliable, This is my way of showing appreciation for a job well done. contact him for help via email address below.. WesleyBrian@CyberServices. com
ReplyDeleteDo you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
ReplyDeleteDo you need to retrieve your stolen bitcoin?
Do you need to increase your credit score?
Do you intend to upgrade your school grade?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : certifiedhacker04 AT gmail DOT com WhatsApp 16317433959.....
Hello people! You can hire the best certified professional hackers for hacking services. Their network of highly skilled and trained hackers can help you hack mobile devices like your cheating partners phone texts and calls, kik hacks, facebook hacks. contact them on CYBERGURU@INBOX.RU . They also do emails hacks, iCloud hacks, websites database hacks, increase credit score, criminal records, recover passwords, youtube channel hacks, network system security, upgrading school grades, hack bank accounts and lots more at a very affordable cost. I owe their good works publicity
ReplyDeleteI got my criminal records deleted in 48 hours with the help of this great man. I also have issues because i have bad negative report on my credit report. He helped me delete that particular negative items on my credit report and help me increase my credit score to 820 golden score, I’ll advise you all to get to him so he can help you get all your problems solved as well. (OptimumCyberService@gmail.com) Trust me he is a genius in the game.
ReplyDeleteHello all
ReplyDeleteam looking few years that some guys comes into the market
they called themselves hacker, carder or spammer they rip the
peoples with different ways and it’s a badly impact to real hacker
now situation is that peoples doesn’t believe that real hackers and carder scammer exists.
Anyone want to make deal with me any type am available but first
I‘ll show the proof that am real then make a deal like
Available Services
..Wire Bank Transfer all over the world
..Western Union Transfer all over the world
..Credit Cards (USA, UK, AUS, CAN, NZ)
..School Grade upgrade / remove Records
..Spamming Tool
..keyloggers / rats
..Social Media recovery
.. Teaching Hacking / spamming / carding (1/2 hours course)
discount for re-seller
Contact: 24/7
fixitrogers@gmail.com
I know a professional hacker named james who has worked for me this week. He offers very legitimate services such as clearing of bad records online without being traced back to you, He clone/hack mobile phones, hack Facebook account, instagram, WhatsApp, emails, Twitter, bank accounts, Skype, FIXES CREDIT REPORTs, track calls. He also help retrieve accounts that have been taking by hackers. His charges are affordable, reliable and 100% safe. For his job well done this is my own way to show appreciation, Contact him via address below...
ReplyDeleteEmail...hackintechnology@gmail. com
Text no..+1(669) 225-2253
We bring to you good news.. Discount is still on going right now to all our numerous customers as to wish them a prosperous new year, get a card from us today and get extra $500 to the amount you want to order.
ReplyDeleteWe have special cash loaded programmed ATM card for you to meet up with those needs of yours and also start up your own business. Our ATM card can be used to withdraw cash at any ATM or swipe, stores and POS. Our cards has daily withdrawal limit depending on the card balance you order.You can make from $2500 to $50,000.00 In USD And EUR,with our Programmed card. Contact us today for your own order at : hennager4040@gmail.com
Here are the price list for ATM Cards:
Balance Price
$2500---------------$155
$5000---------------$255
$10,000-------------$500
$13,000-------------$680
$15,000-------------$760
$17,000-------------$880
$20,000-------------$970
$25,000-------------$1000
$30,000-------------$1100
$35,000-------------$1200
$40,000-------------$1300
$45,000-------------$1350
$50,000-------------$1500
Do contact for more info and also on how you are going to get your order..
Order yours today via Email: Gmail-Compose mail to: hennager4040@gmail.com
call/sms +1-562-453-0961
Hangouts: hennager4040@gmail.com
We bring to you good news.. Discount is still on going right now to all our numerous customers as to wish them a prosperous new year, get a card from us today and get extra $500 to the amount you want to order.
ReplyDeleteWe have special cash loaded programmed ATM card for you to meet up with those needs of yours and also start up your own business. Our ATM card can be used to withdraw cash at any ATM or swipe, stores and POS. Our cards has daily withdrawal limit depending on the card balance you order.You can make from $2500 to $50,000.00 In USD And EUR,with our Programmed card. Contact us today for your own order at : hennager4040@gmail.com
Here are the price list for ATM Cards:
Balance Price
$2500---------------$155
$5000---------------$255
$10,000-------------$500
$13,000-------------$680
$15,000-------------$760
$17,000-------------$880
$20,000-------------$970
$25,000-------------$1000
$30,000-------------$1100
$35,000-------------$1200
$40,000-------------$1300
$45,000-------------$1350
$50,000-------------$1500
Do contact for more info and also on how you are going to get your order..
Order yours today via Email: Gmail-Compose mail to: hennager4040@gmail.com
call/sms +1-562-453-0961
Hangouts: hennager4040@gmail.com